This is a talk that I thought I would never talk about. I was never going to talk about this, because it was a little bit risky. But I think now that this is the best time to do this talk. Not because of all the elections and all that sort of stuff that’s been happening now with the Clinton emails, for example, but there was an article that was released; I’ll show you the slide:
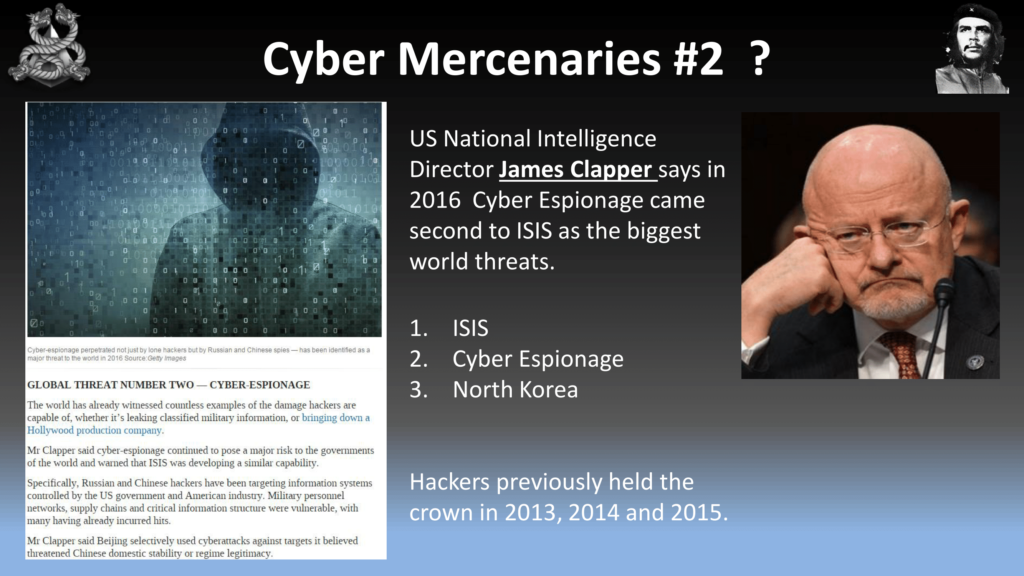
The US National Intelligence Director, James Clapper, said that cyber espionage came second. We came second to ISIS. Now, I don’t want to live in a world where ISIS is scarier than hackers, especially in 2016. We previously held the title in 2013, ’14, and ’15. And to be honest I was a little bit disappointed when I saw this result. So I thought I’m in my 40s now, there’s a lot of young hackers in the audience, and I’m not going to pass the baton to you guys unless we have that number one spot back in our pile.
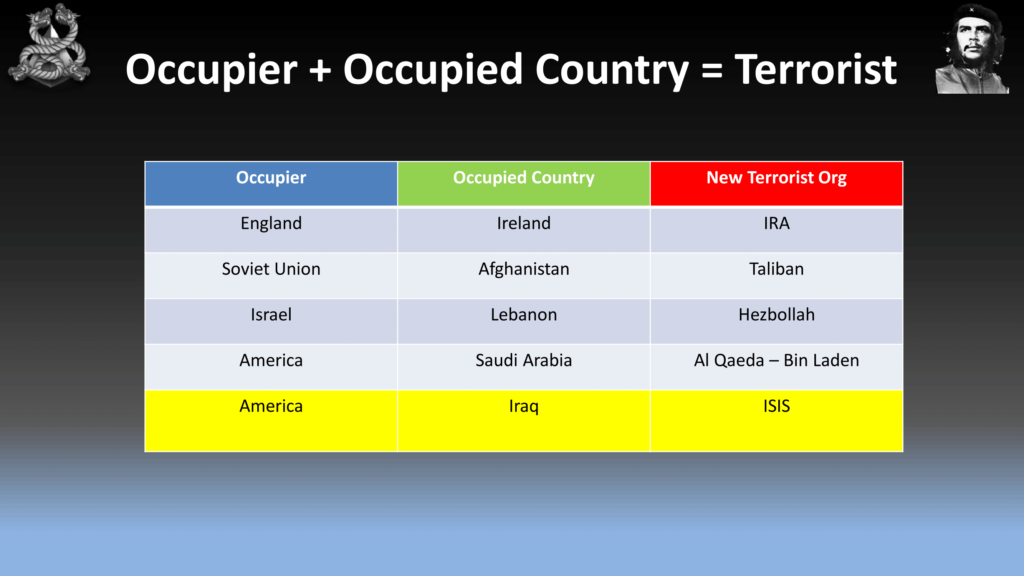
So let’s have a quick look at ISIS. Bit of a no-brainer here. When you have an occupier of an occupied country, you have a terrorist organization. Nothing has changed throughout history. I know it’s a simplistic view, but it is an accurate view.
So the first thing we need to do is when we lose, and we did lose—we came second. We beat North Korea. That’s really good. They’ve got nukes, they’re pretty scary. But we could hack anything we want. I know there’s a lot of people in this audience could hack anything I asked them to hack; banks, government, whatever. We just need to put it all together.
So the first thing we need to do is work out why we came second, so let’s have a look at ISIS. Let’s see how they fight. Now this this gets a little bit violent so if there is any any kids in the audience that have come by r00tz, I apologize. But I showed it to my 8 year-old son and he was cool with it. If he’s cool with it, you guys will be cool with it. So let’s have a look at our competition.
https://youtu.be/m1lhGqNCZlA?t=221
Now I don’t know about you guys but I think that was pretty embarrassing that we came second to that.
So now that we’ve analyzed our enemy, let’s have a look at ourselves. So, the Sony hack, that was a great hack. I love watching those movies every week. The Ashley Madison hack. My wife and her lawyer really loved that hack, seeing my name up on that list. Now, the Pokémon GO hack—now I know why we came second with that shit, with that denial of service on Pokémon GO. Thank you, PoodleCorp. And even my talk about death did not impress James Clapper enough to give us position number one.
So the reason I’m giving this talk is to rectify that. And to do that I need to escape away from our normal hacking environment and we need to skill up a little bit. The reason we did come second is we’re too tunnel focused. We had tunnel vision. We didn’t look outside. So I thought what I’ll need to do is I contacted a mercenary. He’ll be up to teach me some tactics in coups, revolutions, and then I’ll see if I can apply that, and see if I can do a coup or revolution myself. So I contacted this guy. His name’s Simon Mann, and I’ll let him tell you about himself.
https://youtu.be/m1lhGqNCZlA?t=354
Simon Mann: My name is Simon Mann, and I’m helping Chris Rock with his work to see if a coup d’etat, putsch, the overthrow of a regime, could be achieved by computer hacking and by cyber warfare methods. My background to that is that I led the 2004 attempted coup against the regime of Equatorial Guinea. That attempt failed, I was arrested, and I spent five and a half in years in prison for that.
Prior to that, in 1993, I was one of the founding people of Executive Outcomes, a South African private military contractor which is credited with winning the ghastly civil wars, first in Angola against the rebels UNITA, and then in Sierra Leone against the rebels there. I served in the first Gulf War on the staff of Sir Peter de La Billiere. My ten years prior to all of that was as a British Army officer. I served in the Special Air Service as a troop commander and an anti-terrorist team commander, as well as in the Scots Guards as a platoon commander and did tours in Northern Ireland with both of those units.
Chris Rock: So, he’s a master of his field and I’m a master of mine, so I thought it’d be good if we could combine the two together.
So why would we use mercenaries? Obviously, they’re clandestine. There’s no governments that are linked to mercenaries. They’re loyal, so as long as you pay them they’re yours. And it’s not a war if you use mercenaries.
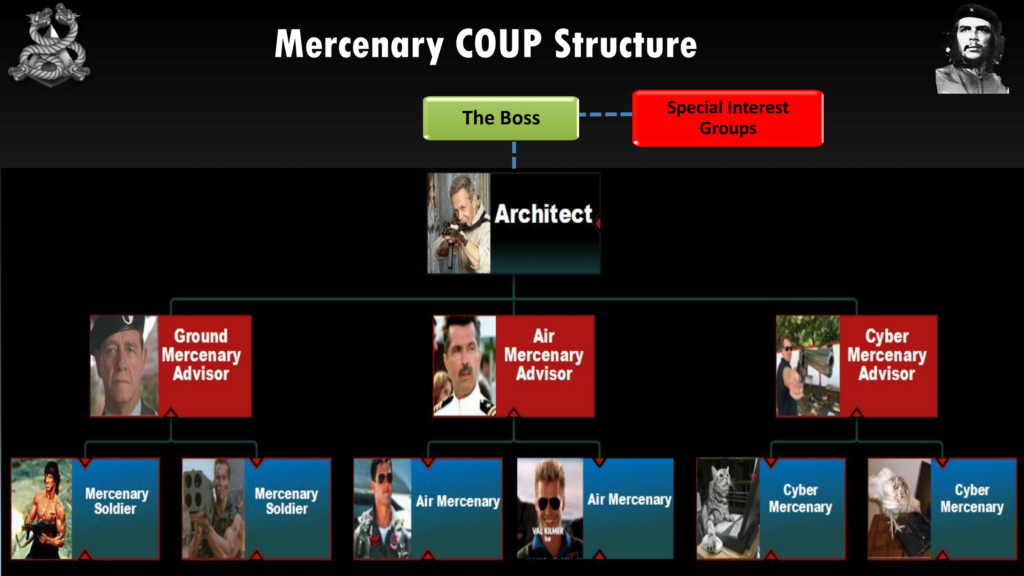
So this is a traditional mercenary coup structure. The important position there is the architect, and you can see a picture of of Simon Mann there with the gun. He’s the man that pulls the levers. So above him, for example, we have special interest groups. This is traditional organizations such as the CIA or private companies who’ve got oil interests, and things like financiers.
Now, under his direct personnel he has obviously advisors, and that’s an an important role, too. So when you guys are looking at doing this sort of stuff for real, you might decide that you’re an architect or advisor; it really depends on how you think. And you can see Simon would have ground, air, and he would also have sea. But now he’s developed the digital domain as well, which you’ll see in the future because let’s face it, the digital domain in terms of intelligence about what we can pull is very important. And again there’s the ground people as well. So we’ve got Rambo down there and Tom Cruise. But these are the ground. So in terms of a cyber perspective we’re talking about hackers.
So for example in Simon Mann’s failed coup in 2004, his special interest groups were people like—who provided finance were the Spanish government, there was also Sir Mark Thatcher, which is Margaret Thatcher’s son, who provided finance and an airplane to move the mercenaries around.

So here’s some traditional mercenary companies. You can see the CIA down in the bottom in the left-hand corner. And you’ll see obviously Blackwater, you guys know Blackwater quite well. But you’ll see also in the middle with the buffalo sign in the middle, that’s—there was a 32 Battalion in the South African Defense Force that were guerrilla fighters. They fought in Angola and modern-day Namibia. And that was part of the South African Defense Force after Apartheid was abolished in ’93. These guys were out of a job, so they became mercenaries. So the companies to the right of the buffalo such as Executive Outcomes, Aegis, and Sandline for example, are companies that were set up by mercenaries who came out of that battalion.
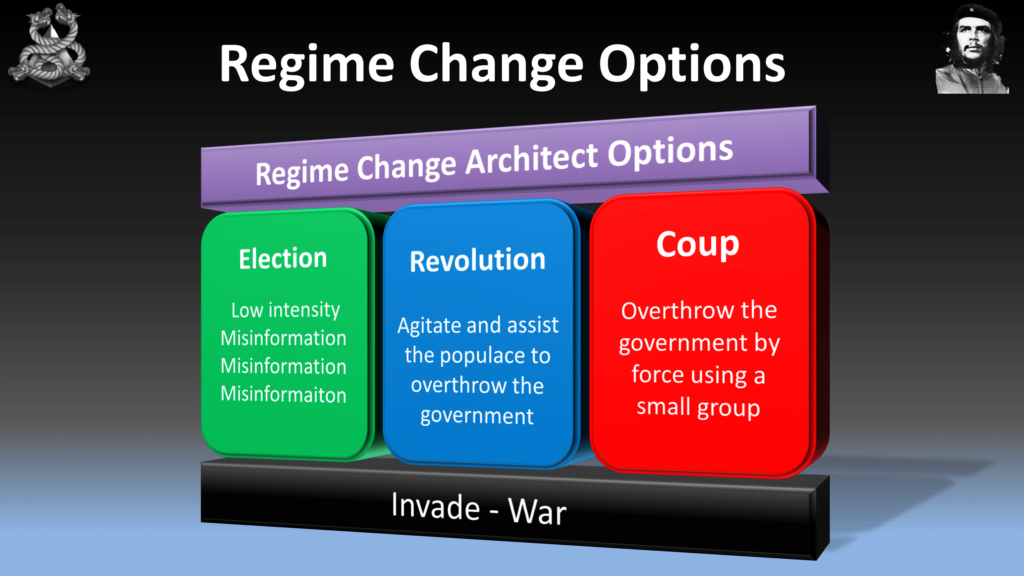
So, when you guys are looking at overthrowing a government you really have three options. We have the election—so rigging an election. Now, election is a legitimate way of changing government every three or four years—not in every country but most countries. We can incite a revolution. Or a coup.
So you guys are experiencing this at the moment, the election. You’re already seeing some email leaks with Trump and Hillary Clinton. I was watching this morning about someone was talking about the size of Trump’s hand, which I thought was fucking ridiculous. I think what they’re doing, what WikiLeaks’ doing is…releasing this information is great but it’s just not really what I’d be looking for in terms of using an election to overthrow a government. So I’d be looking at like a twelve days before Christmas or twelve days before an election tack. It doesn’t have to be real. We already own everything. We already own banks, investment companies. So we can use the items on the right-hand side just to fake whatever we want. So when someone goes towards an election, they can just use those things there on the right-hand side. You can actually move money between the parties, and we’ll have a look at that in depth later on.
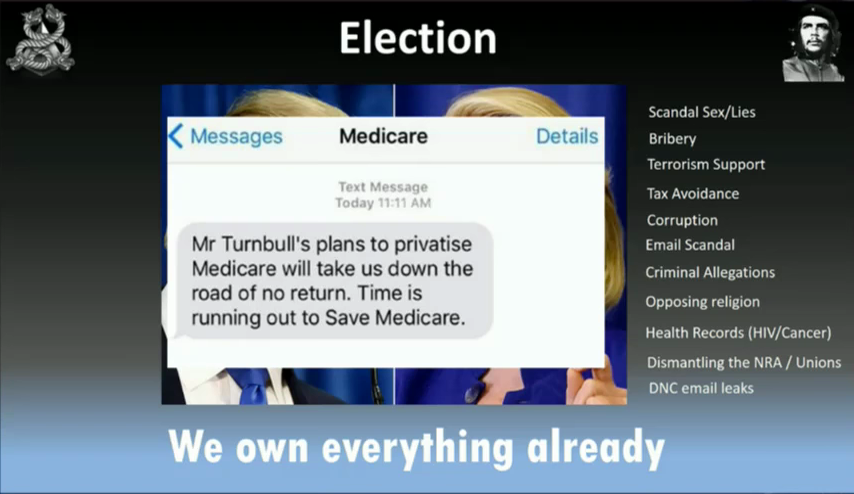
In my country Australia, we got an SMS just before we went to the polls. Medicare is a bit like your Obamacare, and it looked like the SMS was from Medicare. And it was pretty much to scare people into voting for the other party. A technique that you can use too to throw an election.
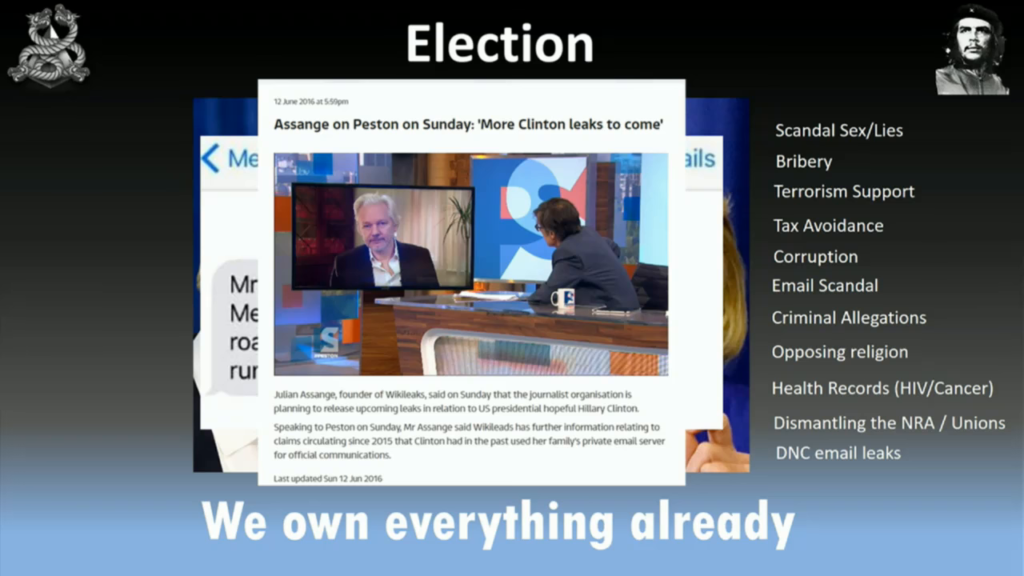
And again the email leaks. As I said, this one’s been going for too long. These things should be done in rapid succession to get into the voter’s mind just before they go to vote.

Okay, the second method we have is a revolution. So here’s a couple of revolutions in history. You guys have had one. We had Egypt 2011, and Ukraine 2014. So for those that don’t know Ukraine 2014, the president of Ukraine was about to sign a deal with the EU. Gets $700 million dollars in loans, and then Putin stepped in and offered them $2–3 billion dollars to get rid of that. So the people revolted against that. And we’ll have a look at that a little bit later on.

The other option is the coup, the coup d’etat. You saw that recently in Turkey, where a small portion of the army, or in our case mercenaries, try to overthrow the government by force. And you’ll see there some examples of coups, and American government was involved in the first two of those.
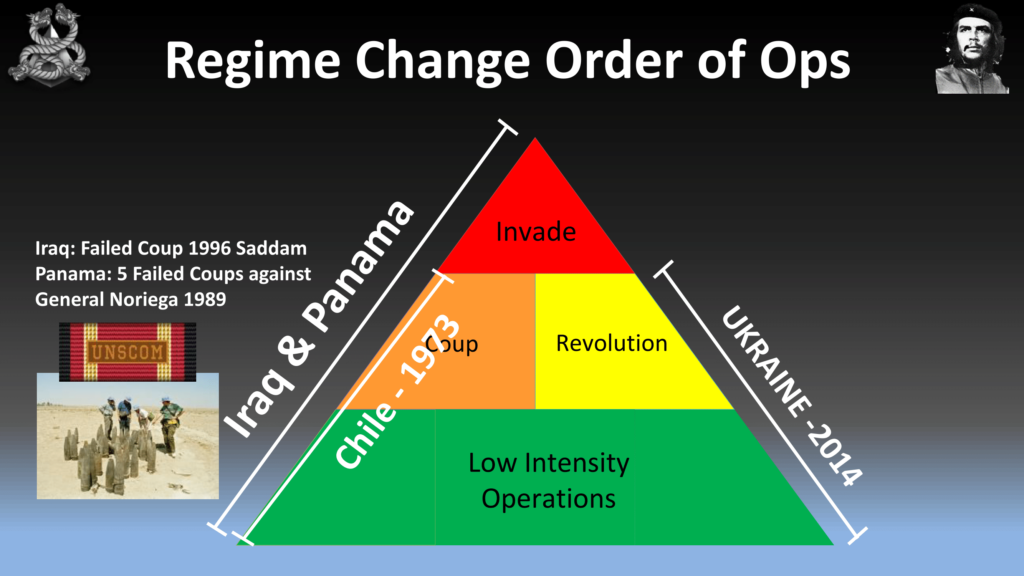
So in terms of where we’d want to start in overthrowing a government, we start down at the bottom. So we have what’s called Tactical Operations, or Low Intensity Operations. This is where you want to weaken the government with insurgency, sanctions, or really just telling them they’re doing a bad job. The example I put up there for the revolution—so if those fail, we have the revolution which we saw in Ukraine. And the picture there is the Deputy PM in 2013 before the revolution, was complaining that the American government were doing exercises called TechCamp and they’re actually teaching the people of Ukraine on how to organize protests via Twitter and Facebook. And he’s complaining the American government are causing the revolution before it happened.
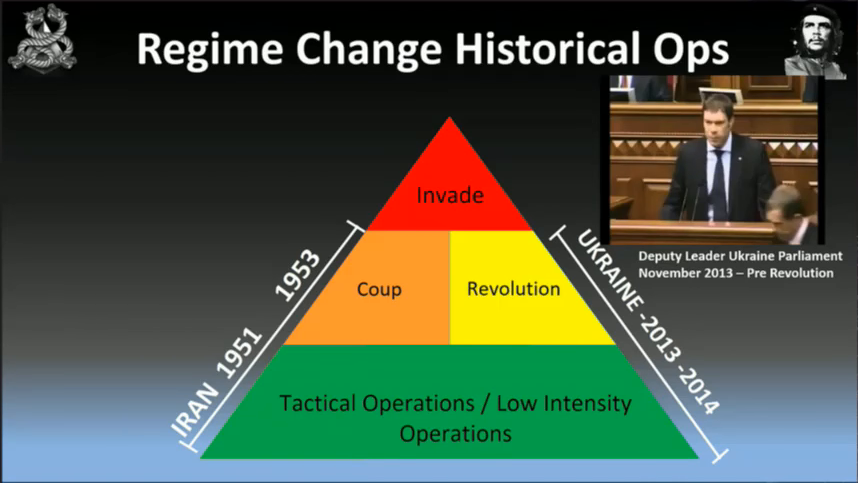
If a revolution is not going to work, then we look at the coup. So the Iran coup over ’51 to ’53 was done by the British government and the US government.
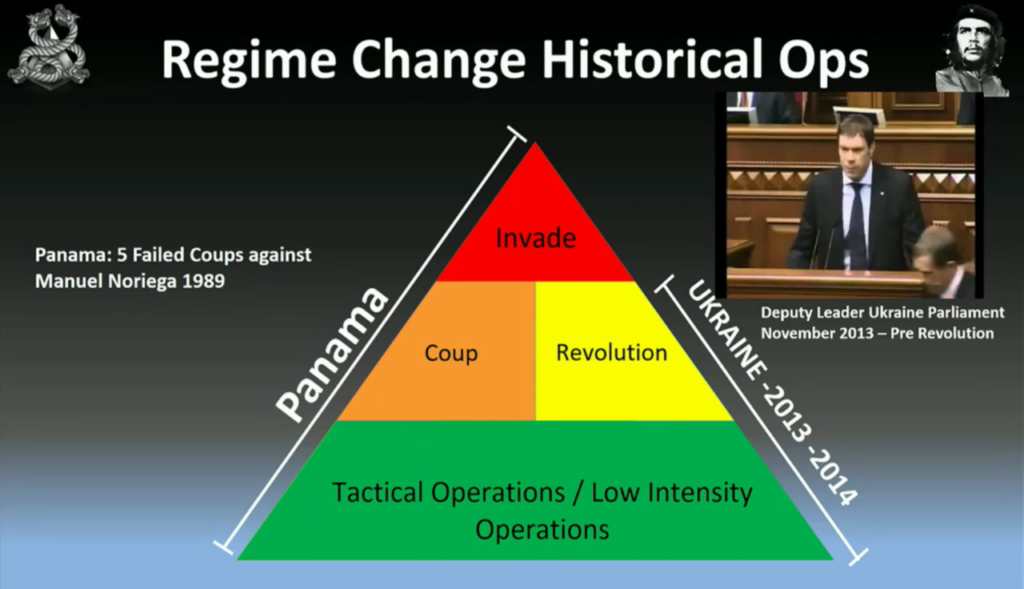
And if that fails, we look at invasion. So, before Panama was invaded, there were five failed coups before Manuel Noriega was replaced in 1999.
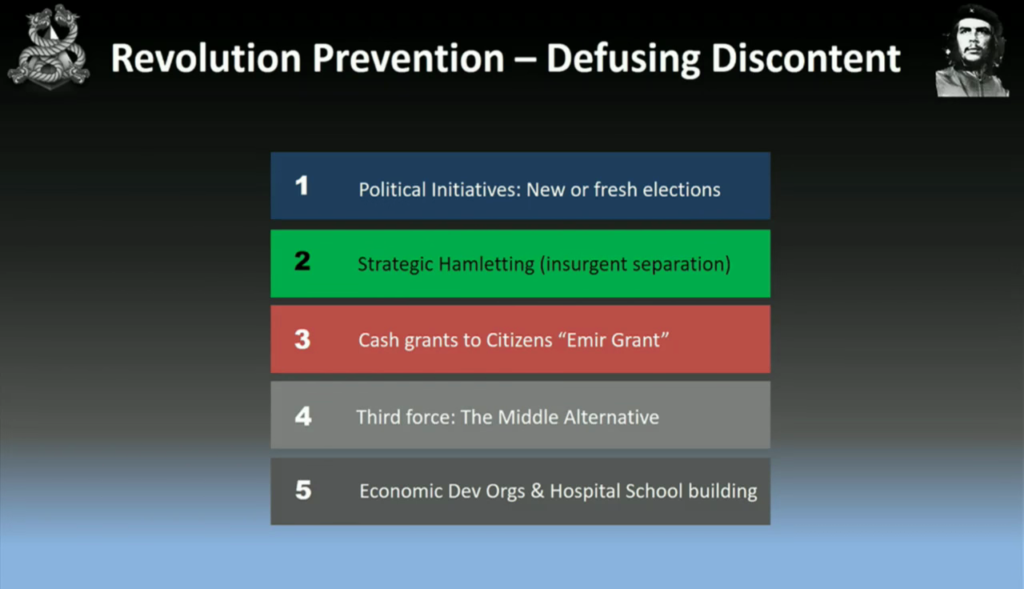
Things you need to watch out for when you’re doing a revolution. These are the five things that will try to stop your revolution. So, the government in power, for example, saying that they’re going to have new or fresh elections. Something called strategic hamletting, which is separating the insurgents from the population, used in the Vietnam war. The third one, which we’ll talk about a bit later, called cash grants—you’re pretty much bribing the people to shut them up. The third one is a middle alternative; so we have a left party, a right party, and you offer a middle party. These are all techniques just to quiet the population down. You just have to be aware of these because they may happen if you’re going to try to set up a revolution. And the last one is economic development organizations and hospital school building.
So when you see the military invade a country, for example like Iraq, and they’re building schools and all that sort of crap it’s all just bullshit. They’re just keeping an eye on the population to stop a revolution happening, post that event. It’s good publicity as well.

Some techniques for preventing coups. So, the private army or the mercenary private military contractor. So, Colonel Gadhafi with his three thousand revolutionary guards. The Saudi Royal family with it’s 25,000 White Army. And you guys have your own National Guard, your private military force protecting each state. That’s a great anti-coup measure; you really don’t have any central point to overthrow the government of the US.

There’s also spies. So Assad, for Syria for example, has these spy agencies that spy on the military and spy on each other to make sure that no overthrow takes place—there’s no coup. And that works quite well. They work so well that a civil war is now in play in Syria, as you guys know. And obviously you guys have a lot of intelligence organizations for this as well.
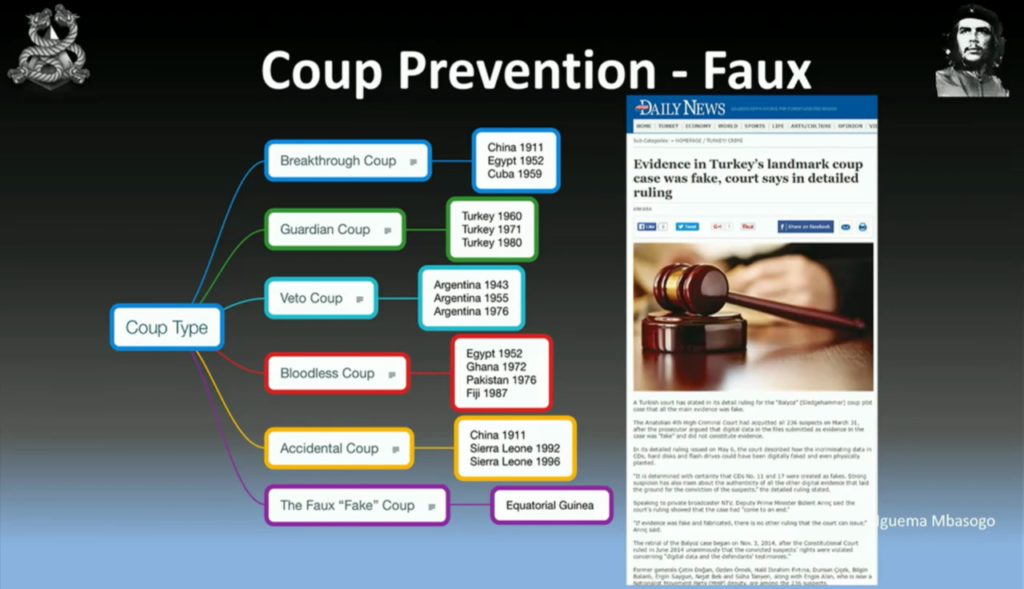
One thing I wanted to bring up is the fake coup—you’ve got to be aware of the fake coup. So, on the screen you’ll see some different coup types, and you’re welcome to study those and there’s some material on your CDs which talk about different types of coups. But when you’re opposition is getting close, you want to arrest them and just say that they’re causing a coup. This worked well in Turkey in early 2000, where the AKP party arrested generals and journalists to say that they were creating a coup. Now, this actually didn’t really happen. There was digital evidence that had been modified and these guys were cleared. And then obviously there was another just coup recently. We don’t know whether it was fake or not yet.

This is a little bit of theory to get you started. And I wanted to talk to you—I’m not really much of a theory guy. I need to know how to create a coup or a revolution, but now I want to apply it to a real country. Operation Nanny Goat, 2011.

You guys would’ve heard of Kuwait. Small oil producing country nestled between Iraq and Saudi Arabia. About three or four million people. That’s a picture of Kuwait. [audience laughter]
Actually it looks like this, so it’s pretty close.

No seriously, this is what Kuwait—it’s a beautiful city.

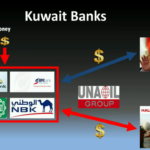
So what we’ll do is let’s have a look at Kuwait City. This is the government and also family tree. They’re pretty much exactly the same thing. We have the Emir at top. You might see a common link in the last names, Al-Sabah all the way through. So we have the Emir, Crown Prince, the Prime Minister—whose name is Nasser Al-Sabah, and then you can see the foreign affairs and defense ministries. Now, what we want to do here is we want to overthrow Prime Minister Nasser. And for those who know the Unaoil scandal, the bribery scandal, they referred to him as “the big cheese.”
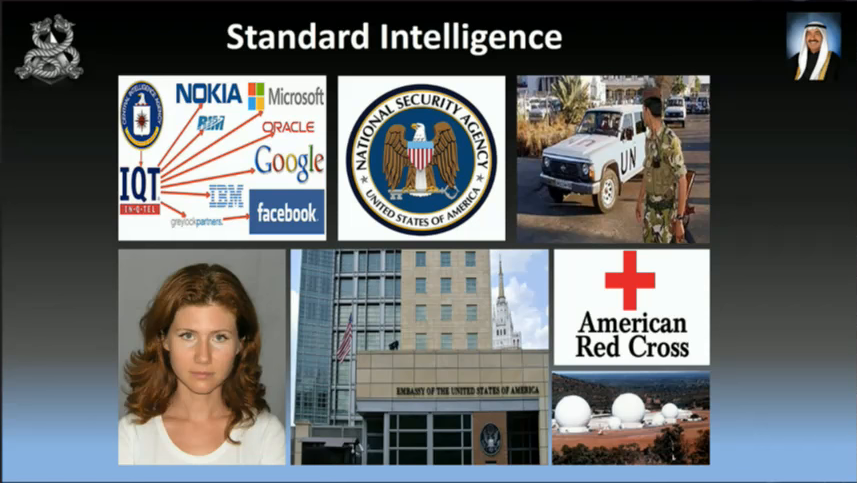
So, this is the standard intelligence that mercenaries or militaries will use. You guys probably will know this sort of stuff, like the NSA and also embassy spies and Five Eyes. What can we use?
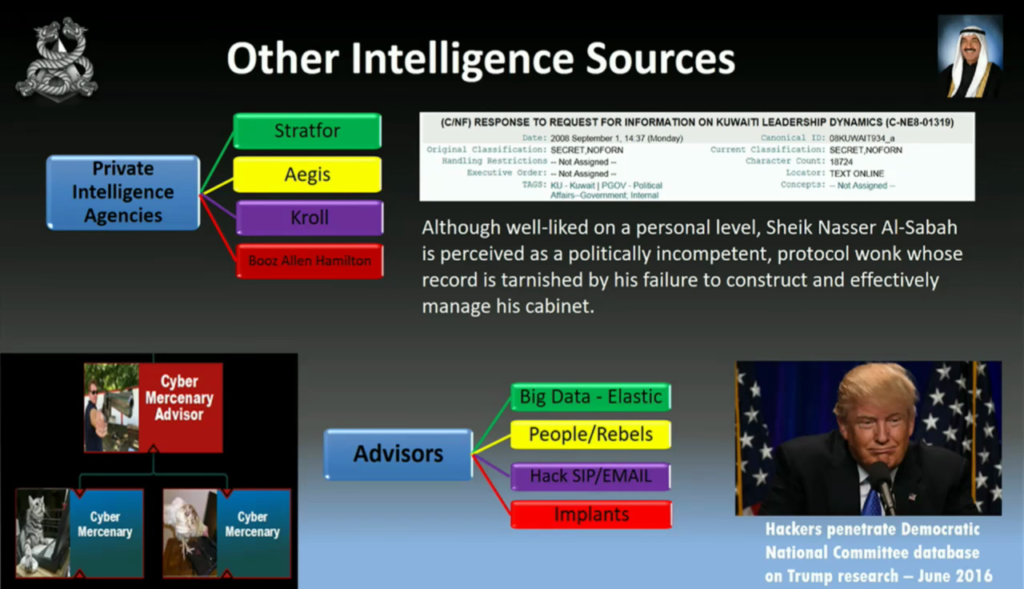
We can also we can use private intelligence agencies, WikiLeaks for example. And I don’t know if you guys can read that, but they referred to Sheikh Nasser Al-Sabah as a politically incompetent protocol wonk whose record is tarnished by his failure to construct and effectively manage his cabinet.
But I believe the best intelligence is the one you hack yourself, and I want to hack all the government, to find out what he’s up to.
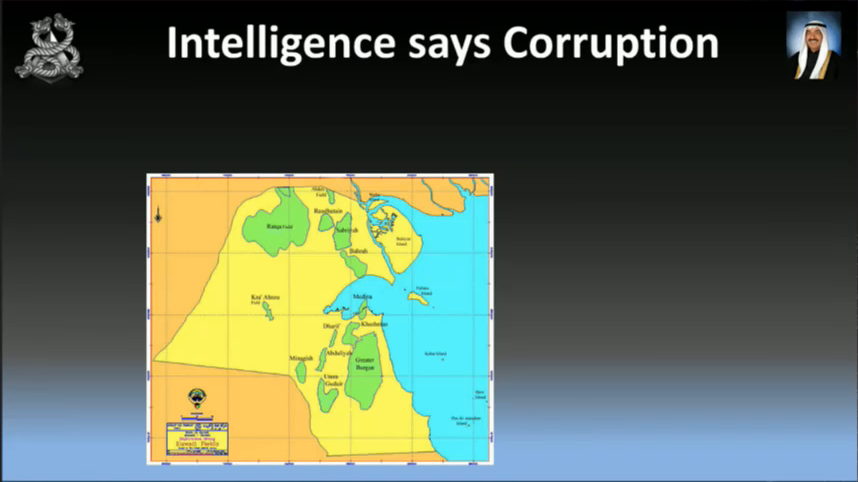
So looking at the intelligence, we think corruption is going to be the big point in this one. Here’s a map of Kuwait, and you can see the green which is the oil fields of Kuwait. And uh the people are not happy that the government are rich and the people feel really poor. Now corruption’s not going to work in every country. You’re going to have to find the weakness in each country. For example Anonymous thought they would attack Nigeria on their corruption, which is pretty fucking pointless because that is Nigeria’s biggest export. It won’t work there.

So what are our options for overthrow? Elections? Nah. There’s no real elections. Those three top parties there, the Emir, Crown Prince, and the Prime Minister? There’s no elections for those guys. The elections are for the guys below that. So we’re not going to look at the election.
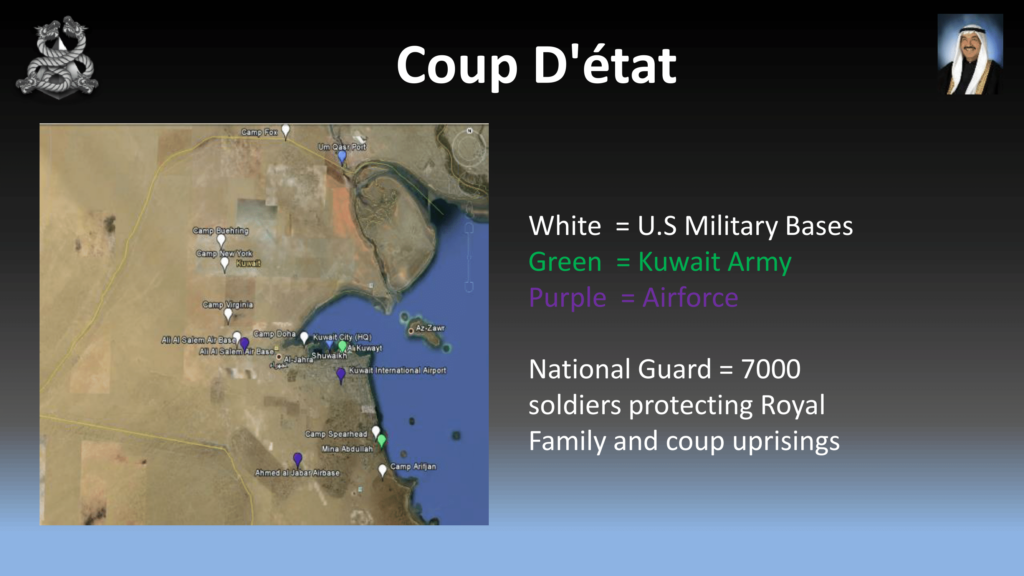
Coup d’etat? No, it’s too hot. Here’s a map of Kuwait. The white dots is the US military bases, the green is the Kuwait Army, and the purple is the Air Force. They also have 7,00 soldiers protecting the royal family. So coup, I’m not a big fan of racing against those forces. So it looks like revolution is our only option.
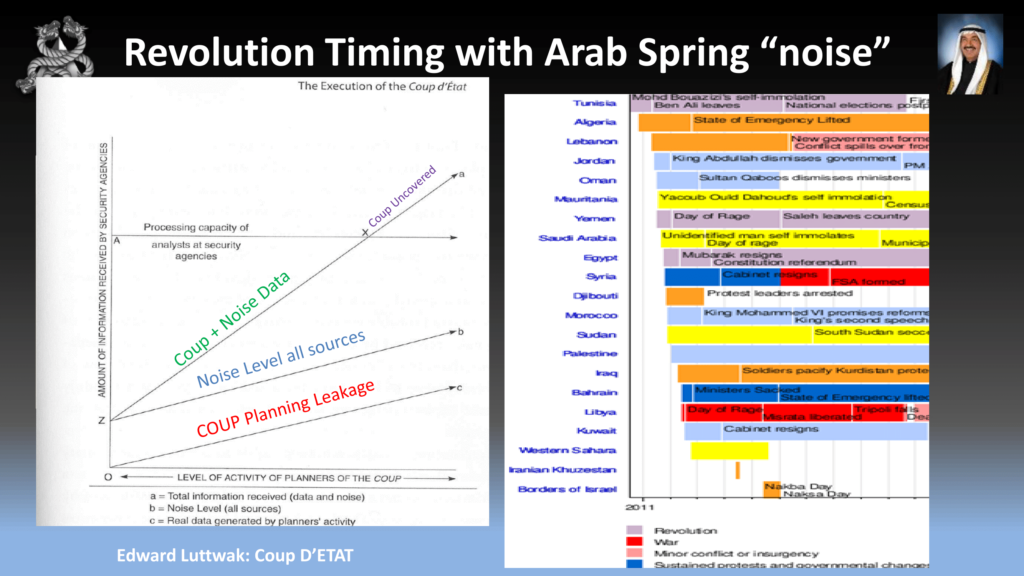
So in 2011, you guys all probably remember this was the Arab Spring. So, on the left-hand side you’ll see the countries that recently fell. And on the right-hand side you’ll see a timeline of the countries in that region that either fell by revolution, coup, assassination, or just protests. And you can see Kuwait down the bottom in light blue: cabinet resigns.
Here’s an extract from Edward Luttwak. If you guys want to to do these sort of coups and revolutions, you’re need going to have to study up on this guy. He’s pretty much a master for strategy. And this illustration shows what the intelligence agencies need to go through to find out whether there’s a coup taking place. So on the Y axis we have all the data the intelligence agencies are going to go through. On the A in coup planning leakage—that is, when I’m planning a coup operation of what’s going to leak out when I talk to my advisors and the hackers. The blue line above is noise all levels. And the green line, here “coup + noise data” is all the intelligence that has come through. And the little X point is when the coup is uncovered. Obviously you want to keep your OPSEC quite low so you don’t get detected.
So, with our cybermercenary structure, same as the traditional mercenary we’re going to use things such as Denial of Service attacks, social engineering, and all our normal hacking stuff. And it’s your job as the architect to employ the advisors to get the people on the ground such as hackers from your country or overseas countries.
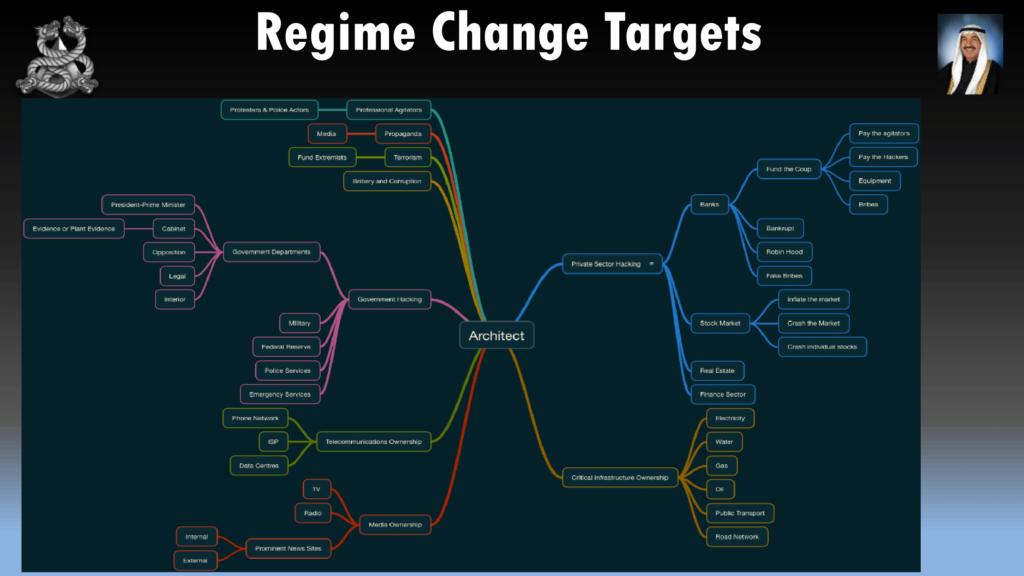
You’ll need to map out all the targets of the country that you want to hack. So we’re talking about government, media, electricity, oil, gas, all those sort of agencies. And you want to map out what you want to hack. Now, I’m not really much of a strategic in terms of what items I want to hack, so I just hack them all. At least then I have the options of what lever I want to pull.
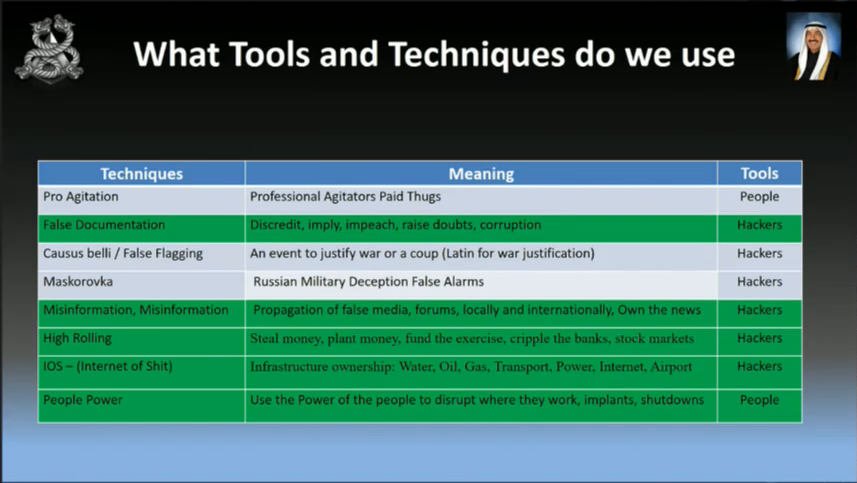
So, as a hacker we know what sort of tools we use on a normal day-to-day basis. You’re going to have to learn some new techniques and tools. Not hard; you just need to do a bit of research. I’ve just got a couple of them up there. A lot of them have to do with misinformation. So when we’re hacking into banks we want to move money around, to make it look really dodgy. And also things like professional agitation; so we want to employ people to do protests, like union members and also university students.
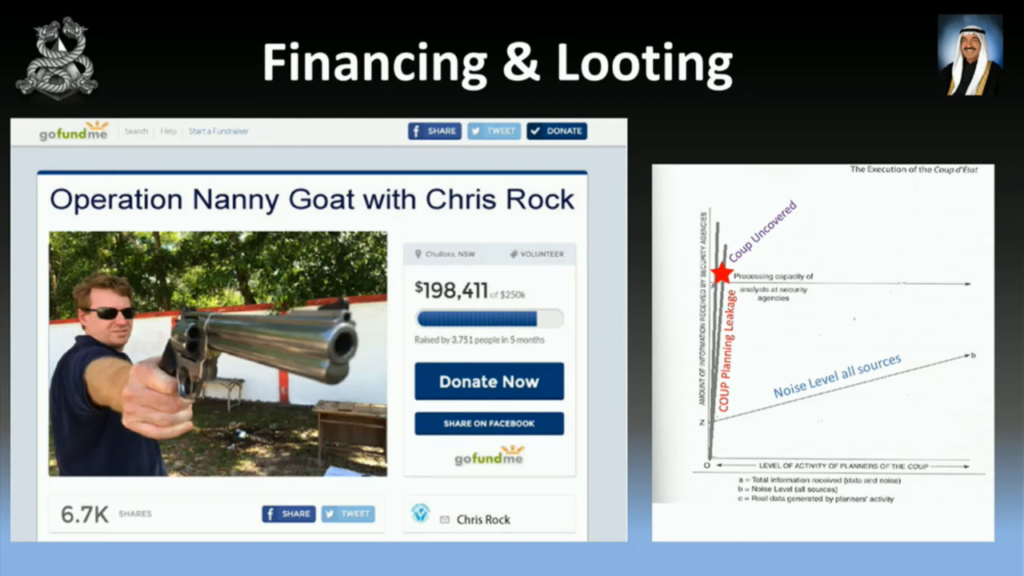
Now, you’re going to have to finance this operation. I probably wouldn’t recommend this method. We nearly got our goal. But by using the chart below, you see that it didn’t take long before we got uncovered.
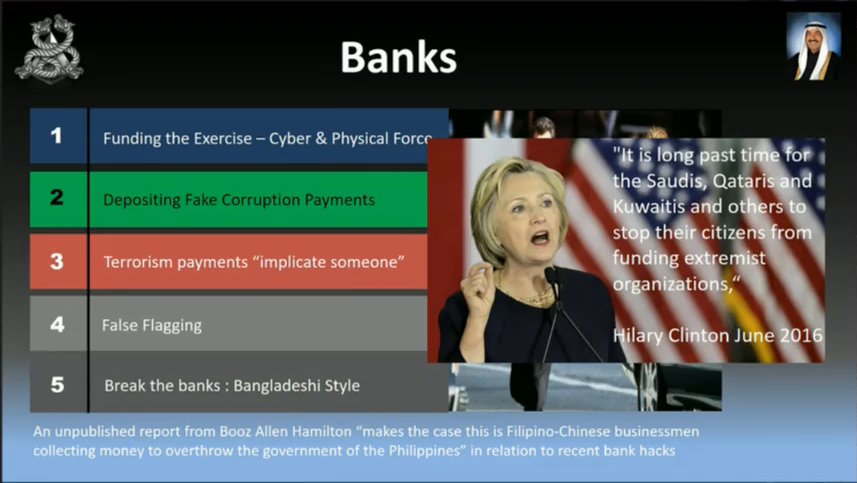
So I’m a big fan of robbing banks; they’ve got lots of money. So we’ll use the bank’s money. You can also use the banks for depositing fake corruption payments (and I’ll share that in a second), terrorism payments, or breaking into the banks such as removing all the money from the banks.
And then Hillary Clinton pretty much said here that we’ve got the green light to attack these countries here; Saudis, Qataris, and Kuwaitis need to stop their citizens from funding extremist organizations.
Another tactic you can use is move money between private accounts from these terrorists into private accounts such as Hillary Clinton, and use that evidence to paint a bad picture of her. Or Trump—I don’t care who wins. They’re both lunatics.

So let’s get into the real world. Here’s the Central Bank of Kuwait. That’s what it looks like in 2011 on the left-hand side. And that’s what it looks like now in 2016. Obviously if you can’t hack in through the front door, use the stuff that you’ve got around. We don’t have to use a zero day; we’ve got a thousand targets to hack. Don’t get all fancy pants on me and use zero days, just use whatever you can. So, whether it be a LAN turtle or Raspberry Pi… You can see that little box, I don’t know if you guys know what that is. The fourth picture along, that’s an NSLU slug. It’s a NAS box which we’ll use as a PC or rat—so a physical RAT within an organization.
Or what we did is we just hacked in the front door. If you can’t hack in through the front door, just pay a cleaner and they’ll put one of these implants in for you. Average cleaning salary in Kuwait is about $150 dollars a week. So you give them two grand, which you’ll use from robbing the banks, they’ll plant them in there for you.

So what we want to do for corruption is we want to steal money from the government and put it in private bank accounts of the government. So there’s a picture of Nasser, and there’s a couple of banks in Kuwait. And an offshore bank.
So now that we own the central bank, we need to hack private banks. Now, we didn’t know from our intelligence which banks he had bank accounts with so we just hacked them all. If we’re hacking them all, we can then move money between those bank accounts. So we used government money and funded the private bank accounts. By doing this too, we could also create bribe payments as well.
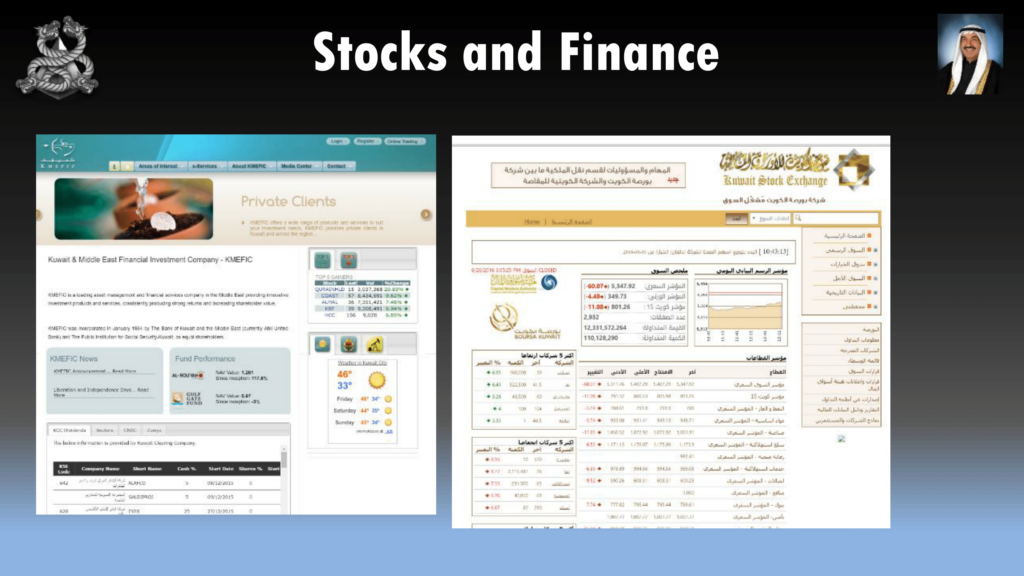
Also, there’s a lot of money in stocks and finance, too. So you want to hack those as well, even to crash the stock market. And again we went through the front door.
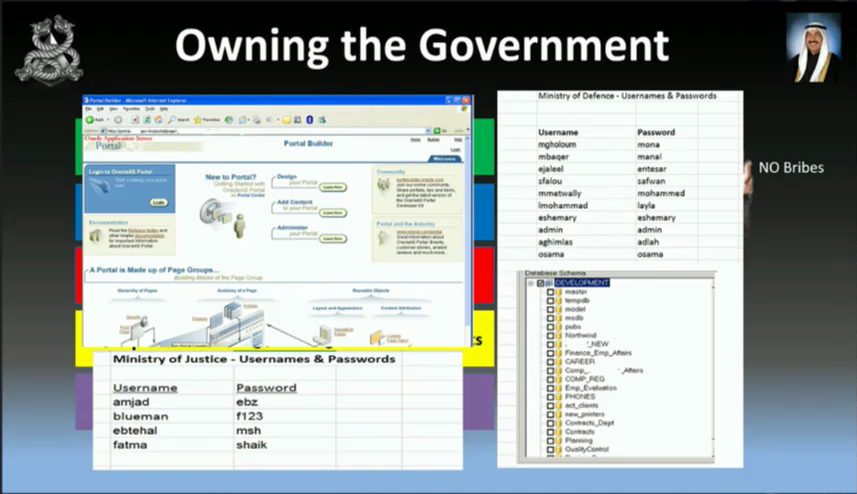
So you want to know what your government’s up to. Whether they’re on to you. Or you just want to see what weaknesses there are in the government. So you’ll need to hack into the government, to listen to their emails, their phone calls. The interior ministry, the judges, everything. These are live shots of of hacked government departments.
One thing you want to hack, too, is the telco. So, telcos are not just phone calls these days. Telcos are media, telcos are Internet… You want to siphon their Internet or you want to squish the Internet, for example. This is a prime case where you want to kill the Internet at the right time, or keep it open if they try and close it.
So obviously, MPLS, point-of-presence (POPS), you want to hack into those. You want to be able to stream your own media, to get the people angry. Obviously companies now are using telcos for cloud services, security services. So, Zajil is the biggest company in Kuwait, who also provide security services for these companies. So you want to hack in, just like what we did. That way you can control the flow of information. You own the ISP, you own the country.
Which brings us to global warming. You might think, “Why are we talking about global warming?” So, obviously they wanted to make sure they reduce emissions by 2050. And the G8 and the EU came together and said what we need to do is map out the current infrastructure such as oil, gas, and find out what’s going on with global warming. So we can use websites like Enipedia to find out where things are such as power, oil, and nuclear plants.
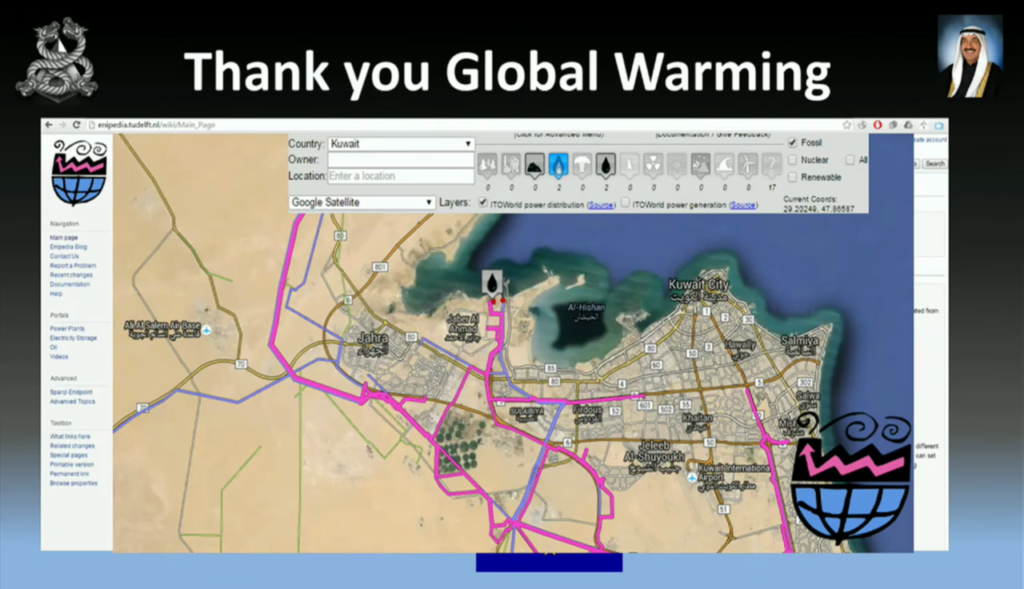
So you just plug in your country and it’ll show you all the maps. Now, why would you want to cut these services? It’s a no-brainer. When you want to do a revolution or coup, you want to cut the power at specific times, or cut the water to piss people off. And that does piss people off when they live in the desert.
And also your energy sector, as well. For example, the study’s online if you want to have a look at that. “Higher voltage transformer units make up less than 3% of transformers in the US, but carry 60% of the power.” So how do you map those out?
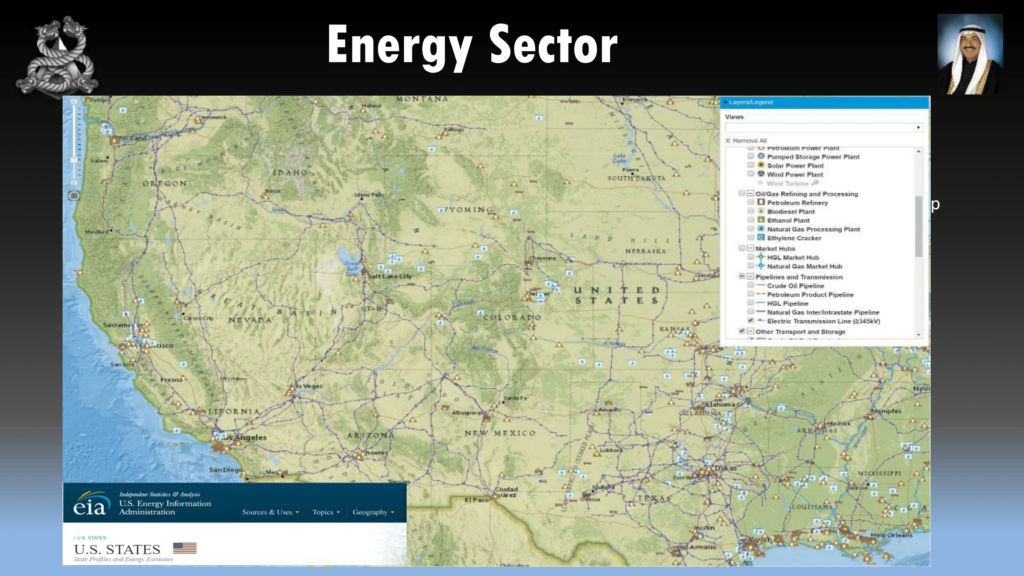
You guys have web sites that do that for you. So what you do is just take high voltage transformer lines, and it’ll just tell you where the all power comes from, if you want to disrupt power.
So, you’re going to need to study what a power station looks like to disrupt it. So when I was talking to Simon Mann he said to me, “Just blow it up.” [audience laughter]
I said, “I’m not Zoz, I don’t have C‑4 I’m just going to chuck on the bloody thing.”
So he said, “What you need to do is disrupt power.”
Okay, no worries. So I thought well, I can hack into power, so why don’t I just shut it off that way?
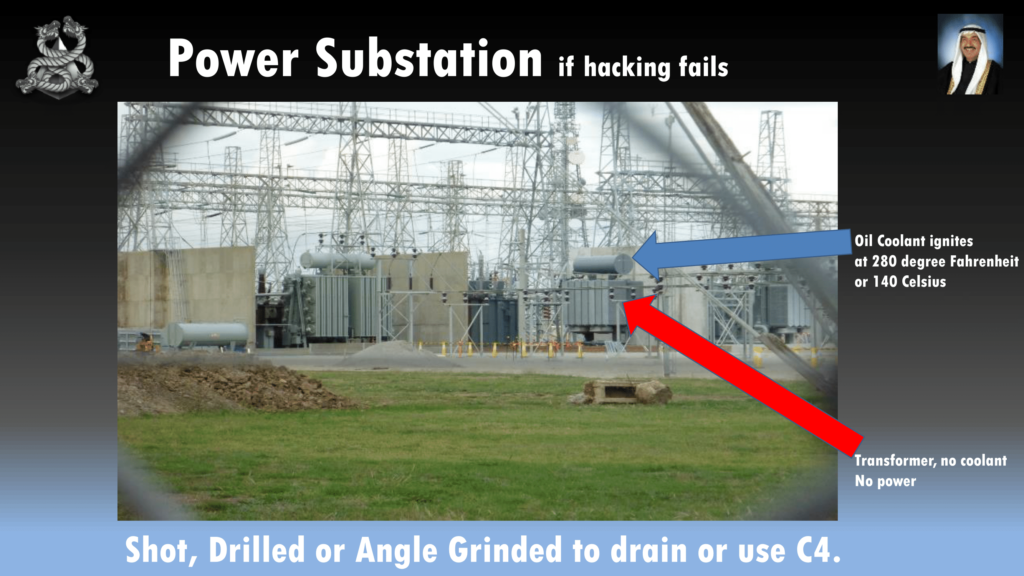
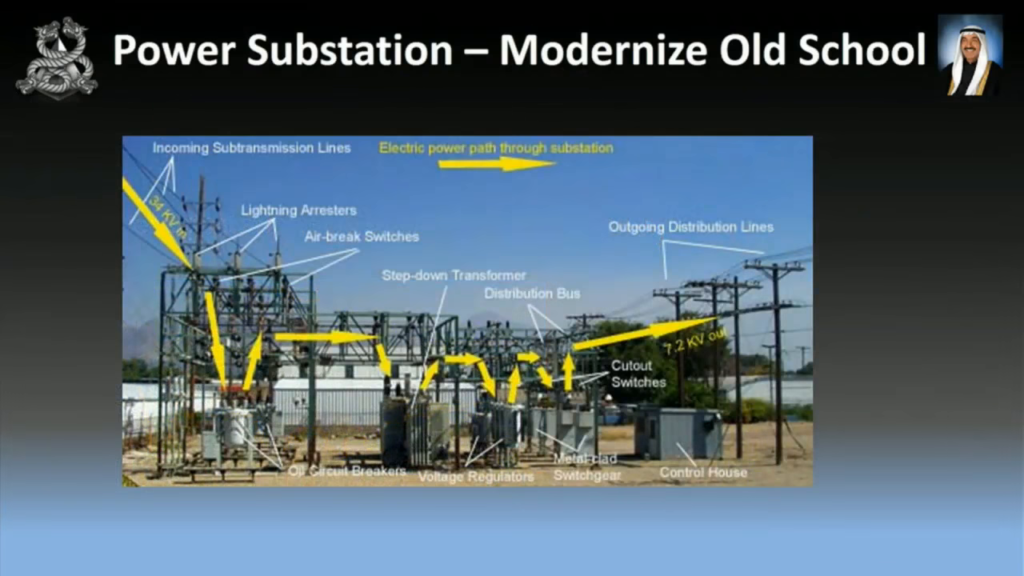
So here we have a transformer. This is not an American picture, so this is not your critical infrastructure…your honor. This is an Australian transformer. So the transformer’s down below, and at the top we have what we call mineral oil that keeps it cool. And when a transformer doesn’t have oil, it doesn’t work. So there’s no power. In 2014 in California, someone was shooting at these things, drained the oil, and then you guys were out of power for twenty-seven days and they just had to reroute power from another substation. So Simon’s suggestion, if you want to get hands-on you can shoot them, drill them, or angle grind them to drain that oil.
And I thought well, I’m not going to do that. And I’ve failed to hack in. I fucked up. I couldn’t do it. So, you guys have probably seen these before. They’re these spinning blades that they put on a helicopter that chop trees away from power lines. For those that haven’t seen it, just a just a quick look. [plays brief clip from following video]
https://www.youtube.com/watch?v=5t06LbvE3CI
Pretty cool. And it chopped trees from power lines. Now I thought that’s pretty cool but I actually want to chop power lines myself. I don’t have a helicopter, but why don’t I use a drone? So I thought, “I’ll make my own.”

So what we have here is two eight-inch circular blades attached to part of a bike frame, and those just spin really fast, attached to a cordless drill. And you’ll see that on the second picture I’ve actually removed the battery and I’ve actually removed the battery from the pack, only because the battery kept getting caught on the power lines, so I removed it. So how does it work? I’ll show you.
https://youtu.be/m1lhGqNCZlA?t=1893
So that’s a great device for cutting power lines. That’s the £5 model. And you could actually reduce it and we could get it under £3 so you can do it to the weaker drones. So you just use a series of drones, put the coordinates in, and it’ll just run straight through the power lines. The cables I used there were copper. The ones that are on power lines are aluminium, so it’ll go straight through those. If you’re going to make one of these be really fucking careful. There is no safety shit involved.
If you’re a bit of a tightass and you’ve got a small drone, just hook a ten-meter hose to your drone with a piece of wire and run it over the power line, and once it hooks onto the power line, it will drag it across and drop it over the power lines and just arc them. So that’s the cheap version.
So now that we own everything and we can hack everything including the banks, we need to understand how the media works. So we need to reverse engineer them. And that’s what we do for a living, so why don’t we do it with the media? So what we do is we apply what’s called the two-source rule. The media need two sources to use as a story, and I’ve got the sources on the right-hand side, and types of sources. So you’re going to need at least two sources to fool the media. Or you can actually pwn a few media outlets that we did from the telco, publish information, and then just release it.

You want to release the information to the news agency that will release that information without even questioning it. So for example Fox News, you want to use the Hillary Clinton information—they’ll publish it and they won’t even give a shit. You don’t want to do it in reverse because then they’re not going to publish it. They’ve got no interest in doing that.
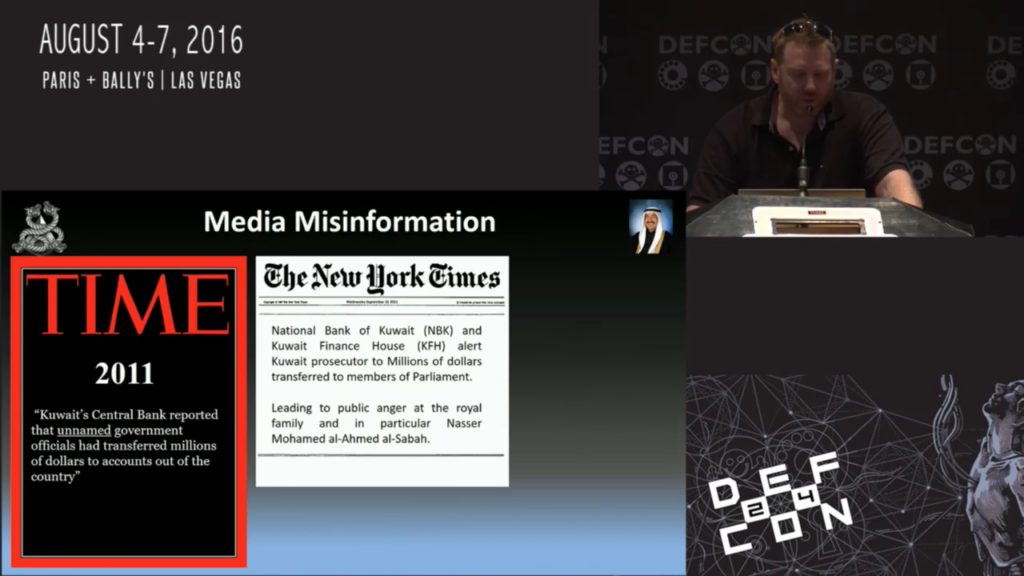
So what we did is in 2011 we used Kuwait Central Bank—we already owned them. So we used unnamed government officials to transfer millions of dollars outside the accounts into their private bank accounts. And we used the New York Times to do the same thing, using that two-source rule.
Now one of my idiot advisors thought this would be a great idea. He thought using a Kuwaiti prince convert[ing] to Christianity would be a good idea, and went with it. He did get the publicity he was after—we got a hundred media outlets that went with that. But it was just a stupid idea.

You need to use the people in this. When the CIA are planning a coup or revolution you need to get the people on side. You’ve got money in your hands. You need to use bribes. So use this sort of money to pay people to put implants within companies, professional agitation, misinformation. Or get corporate people to do stuff for you. You’ve got to heat the population up enough to give a shit to overthrow the government.
So for example the professional agitators, you would have a group of people that you would pay to cause a protest. And then you would get another group of protesters dressed in police uniforms to bash them up. And then you get that on the news. And if they weren’t published on the news, you publish your own news—you own the telco.
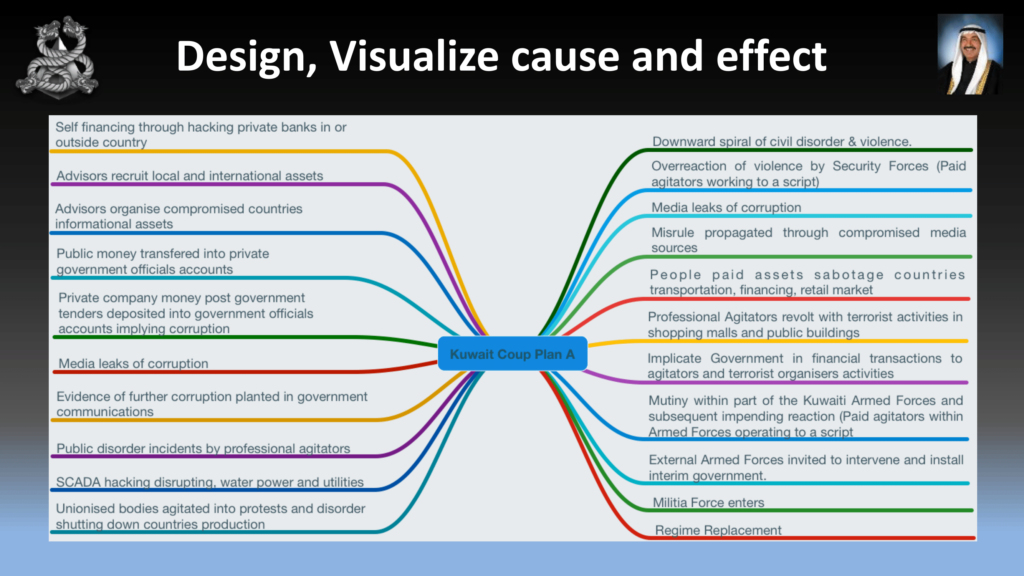
When you’re planning the operation, you need to plan it down to the absolute detail, and you need to be flexible because shit just won’t go right. You might lose a RAT. You just need to have to plan for changes in your operation.
So I’ve talked a lot, and I want to show you how it works in the real world. So I’ve put a video together just to show how it works.
https://youtu.be/m1lhGqNCZlA?t=2134
Okay, guys. What I want to leave you with now is for the new hackers in the new generation is just think bigger. So don’t try and hack bigger targets, but combine multiple targets and look outside of your industry to combine multiple things together. That’s it, guys, and then we’ll be number one again.