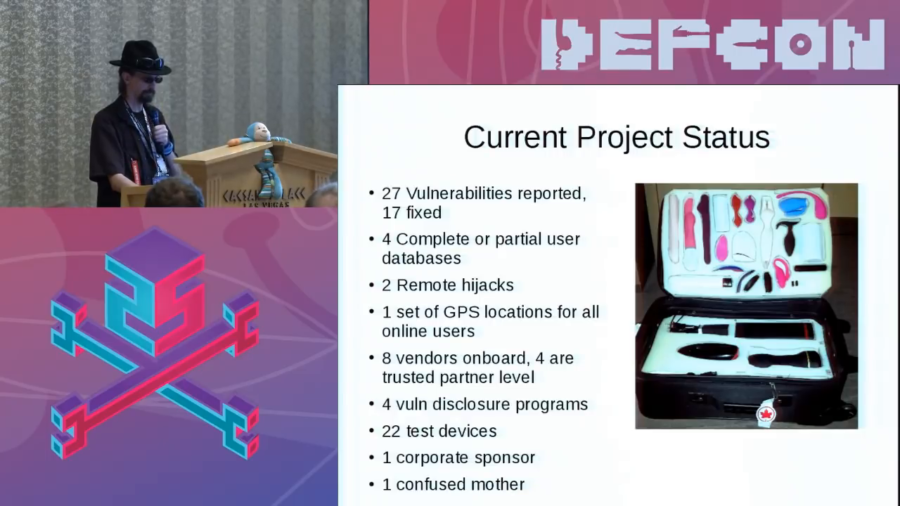
The greatest threat to the security and stability of our Internet today is distributed attacks, distributed denial of service attacks in particular. The Internet was built on a foundation of it works because everybody cooperates and we all agree. And that was a great environment when you pretty much could name everybody who was on the Internet, or you got to where you could name all the sites and you know, you could name all the organizations.
Archive (Page 1 of 3)

We’re at a time of huge expansion of the Internet outside of the kinds of Internet connections and devices that we’re familiar with. We’ve seen some of that over the past few years as we’ve moved from laptops, desktop computers, to smartphones and tablets and we’ve seen a big increase. Right now instead of a tablet and a laptop at home, you’ve got a tablet, two iPhones, and a desktop computer.

I think he would to some extent be surprised that business has hijacked the Internet in a certain sense. That the entertainment industry…I’ll just pick on them but other industries too, that’ve basically exploited that sort of delivery vehicle that was made not really with them in mind but they have gained such a dominant position in dictating how and where the Internet goes.

I would hope that ten or twenty years from now we live in a world in which Internet access is taken almost for granted, and that it’s conceivable that the Internet—the name “Internet”—will actually fade and we’ll just consider it part of the infrastructure that we’re used to just like you know, there’ll be a plug in the wall for information services over the Internet.

I’m pretty nervous about the 2020 elections. We’ve seen a lot of little deepfakes here and there. And I suspect it’s not going to surprise you to say that I’m worried that things are going to get far far worse and far more nuanced.

Today we face many highly complex challenges both nationally and internationally. From security of our information networks, to planning for and managing natural disasters, to emergence of new infectious diseases, to social and political conflict throughout the world, these challenges are messy, and highly interconnected.

You might be more comfortable thinking about deploying math and code as your tactic, but I want to talk to you about the full suite of tactics that we use to effect change in the world. And this is a framework that we owe to this guy Lawrence Lessig.
The interesting phenomenon related to the RSA algorithm and is not shared with some of the other algorithms is it is useful for both encryption and for digital signature. That is they are two distinct uses and this single algorithm is useful for both of those. And there’s an amazing and somewhat interesting story that then develops from that.
What we’re trying to do is to see over the horizons, looking at essentially a five-year time frame, and identify what will be the cybersecurity landscape in that context.