Golan Levin: Next up is Runa Sandvik. She’s an engineer with the Tor Project, and highly knowledgable about privacy and security and how it intersects with culture. I’m thrilled to introduce Runa Sandvik.
Runa Sandvik: My name is Runa Sandvik. I figured I would give a presentation to better explain the work that I do and show, hopefully not too technical, but show how you can think about the way you go about your online life and the traces you leave online, and what this means for the work that you do, the people you interact with, and so on. This is a presentation that I gave a couple of months ago to a bunch of journalists. I don’t know if there’s any journalists here, but if the presentation seems very journalist-specific that’s why. I think it will apply to if not all then some of you here, but it was especially geared towards journalists.
I work for an organization called Freedom of the Press Foundation. Before that I was with the Tor Project. The Tor Project is a non-profit that develops a piece of software called Tor that essentially allows you to be anonymous online. It means that when you’re using Tor, the web sites that you’re visiting do not know that you’re the one visiting them, and your Internet Service Provider cannot see which web sites you’re visiting Your employer, your partner, anyone else using your computer, cannot see which web sites you’re visiting.
This software has been around for twelve years now. It’s been open source since 2002. About six months ago, I went to work for Freedom of the Press Foundation, which is another non-profit that specifically helps journalists do the very important work that they do every single day. This means helping them use digital security tools. Helping them understand the different tools. Helping them understand the threats that they face online, as well as help them safely receive documents from anonymous sources. So we have this system that we developed called SecureDrop which allows the journalists to use Tor, and allows the sources to also use Tor to safely communicate and exchange documents in an anonymous way. So if say, the NSA or someone else wanted to figure out who’s the source, who’s the person that’s sending these documents to one of these organizations, they would just see that someone is using Tor to do something. They can’t necessarily say that this person is using Tor to upload these documents to this news organization.
In addition to that, I have also spent some time creating a list of journalists that have been arrested in Ferguson while covering the protests there. So on the Freedom of the Press web site there is a blog post listing I think there’s twenty-four journalists now that have been arrested between mid-August and now. So there’s the full list, there’s a link to a news article about every single journalist, and there’s also a records request for the arrest report, for the mug shots, and for a couple of other interesting bits and pieces.
In this presentation I covered threat modeling, which essentially just means figuring out what it is that you need to protect, and who you need to protect it from. It is the case that we assess risks every single day. I can’t really see you here but raise your hand if you check the weather before you leave your house in the morning. Some of you do. And why is that? We check the weather because if it’s going to rain we might want to bring an umbrella, if it’s going to be really cold we might want to bring a hat, and so on and so on and so on.
Now, the situations that we face are not always the same. It is the case that a protest by what might be a kindergarten is not the same as a protest in Ferguson or in New York or Chicago or Oakland, as we have seen over the last couple of months. We evaluate risks by doing research. And in this case, this is from September/October I think?, the Washington Post covered the protests and at one point issued this statement and said that “following the lead of over news organizations, The Post has decided to outfit its employees with gas masks purchased at a chain hardware store.”
So initially this was not gear that the journalists had with them in Ferguson, but the Post made this risk assessment, it was a part of their threat model now that that was something that the journalists needee and that they should have while covering these protests. So again we re-evaluate the situations.
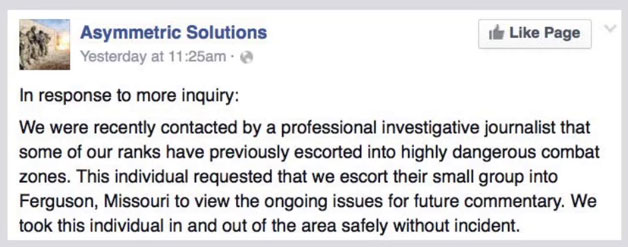
This one I include because I thought it was a bit interesting. It’s a post on a Facebook page from an organization called Asymmetric Solutions based out of Ferguson, or based out of Missouri at least, St. Louis. They had tweeted a couple of days prior that “we have for the first time deployed a ‘high threat team’ to Ferguson.” And a lot of people started to wonder, was this something that local law enforcement felt that they needed? Was it something that protestors felt that they needed? And so they issued this statement that said that they were recently contacted by a professional journalist that wanted their help.
Now, Asymmetric Solutions, they’re ex-military that provide essentially bodyguards. So an investigative journalist felt the need to hire a group of ex-military officers to come with them to Ferguson to cover the protests. Someone had then evaluated the situation, re-evaluated after seeing what was going on, and then hired this group to go in with them.
This was a lot of Ferguson talk. A lot of protests, also very specifically for journalists. But it is the case that just as we evaluate situations offline, we need to do that online as well and think about the information that we have, think about where we leave traces of the work that we do, who we share this information with, how they protect the information that you share with them, and so on. And so there’s sort four questions that I like to suggest that people think about when they start thinking about their own threat model.
The first one is “What do you want to keep private?” It’s not the case that we talk about hiding anything. It’s about protecting information, protecting sources in the case of journalists, protecting information that other people have shared with you. This can be a lot of different things, it doesn’t have to be documents that Edward Snowden shared with you. It can be photos, it can be blog posts, it can be research, it can be different types of projects. I think a good way to start thinking about this is think about the information that you have and the information that you’ve worked with over the past week, past three days. And then think about how you would feel if all of this information was published on a Tumblr tomorrow. That should give you a good idea where to start and what kind of information you want to keep private.
The second one is “Who wants to know?” For most of us the NSA is not necessarily our biggest threat. It could be someone you work with, someone you know, ex-partner, disgruntled employee. It can be a lot of different people that will want to know the information that you have.
“What can they do to find out?” They can steal it, they can hack your computer, maybe they already have access to your email. There’s a lot of different things that these people can do to find the information that you have that they might want. And it’s also the case that you might not necessarily be the target. Someone who is close to you could be the target. There’s been stories over the past year or so that show how hackers who have targeted journalists specifically have not necessarily gone after the journalist that for example wrote the story that they didn’t like. I think earlier this year Forbes was hacked by the Syrian Electronic Army because the Syrian Electronic Army was a bit unhappy with a couple of articles that had been written. Instead of going after the journalists who wrote the stories specifically, the Syrian Electronic Army went after the social media editor and managed to hack into this person’s account and from there made their way into the Forbes platform and started posting content. So it’s not necessarily you that’s the target but people who are close to you can also be the target in these cases.
Then there’s the question of “What happens if they succeed?” In some cases it can be an article is not published, a source is revealed. It can be your project never happens. A competitor launches a product before you do. There’s a lot of different things that will happen here. Another story from I think 2012, where a journalist or documentary filmmaker, I think, had gone to Iran to interview a bunch of activists about the work that they do there, and had phoned and had interviewed a lot of people and talked to a lot of people and gotten more names of people that he should talk to. Then he was stopped on the border going home and all of his tapes, all of his notes, everything was taken away from him. Suddenly every single person that he talked to was at risk because they were doing things that the government didn’t necessarily agree with. But that’s a very extreme example I think. It’s not necessarily the case that someone might die because you don’t have a strong enough password on your email account, for example. But for some people in some cases that should be a part of their threat model.
The solution is to make a simple plan. With that I mean think about what your threat model looks like. What kind of information do you have, how can you protect it, how are you protecting it right now, how many copies are there of this information? Make a plan for how you are going to keep that information safe. And keep it to yourself. It sort of is the case that if you come up with a great plan for securing the information that you have, you don’t necessarily have to go about and tell absolutely everyone about it.
This Twitter account, if you haven’t heard about it before, it’s called Need A Debit Card? It’s fantastic. There are people that are so excited to get a debit card that they tweet about it straight away. If you also look at the replies to some of these tweets you will see the person will tweet again and ask, “Why do people keep asking about the number on the back of the card?” Some things are better kept to yourself. And I figured I would leave you with that.
If you have any specific questions about digital security tools or anything like that, then I am around for the rest of the evening. Happy to take questions about that, too. Thank you.
