Hello. Thanks for joining me this morning. I’m a little shaky. I spent a little too much time and energy at the speaker’s dinner last night. So bear with me if I have to stop for water a few times.
So I’ll be talking to you today about the state of the Internet, or as I am calling it “the network of sorrows.” And I think Shakespeare really does help us understand the technical underpinnings of our current Internet when he says, “When sorrows come, they come not single spies, but in battalions.”
So, let’s go back to the beginning, or close to the beginning of the Internet. It starts as a simple system, very academic. And in this world, the security model of the Internet was when someone did something bad, you called their advisor and yelled at them. We’re still working with the same model of the Internet.
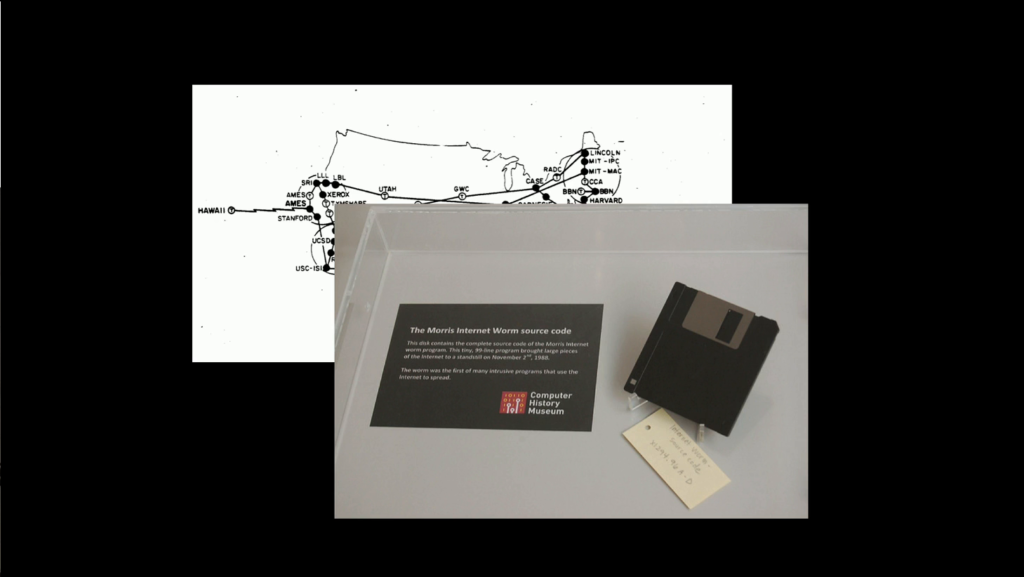
So when our first worm hit, the Morris worm (this is the picture from the Computer History Museum with the source code of the Morris worm), that was basically how it was handled, even though it became in the US the first conviction under the Computer Fraud and Abuse Act, it was still basically just call someone’s advisor and yell. And that’s kind of all we have to this day as a network security model.

And whatever your particular flavor of big adversaries on the Internet, whatever you prefer to be afraid of, whatever APT you decide to describe, it is very important to remember that these big adversaries that get a lot of media press, that get a lot of attention, they target a very small number of people. A very small number that concentrate wealth, or power, political power in the world. Little adversaries, the little wiseass adversaries that we’re dealing with every day, they target literally everyone in the world. Everyone. And you know, the motto of this conference is “Nothing’s beyond a good hack.” But let’s all admit that almost nothing is beyond like, asshats with a phishing script and a spell checker. That’s kind of where we’re at.

So fast forward from something like the Morris worm to today, or close to today. This is McAfee’s numbers for 2014. We’re talking about estimates of up to half a trillion dollars. Now, this information is extremely difficult to be sure about, and what counts as loss, and there’s all these different factors that go into it. But half a trillion dollars globally two years ago.
The predictions for this year from some analysis is that we’ll hit seventy-five billion in ransomware alone by the end of the year. Some estimates say that the loss globally could be well over a trillion this year, but it’s hard to say what a real number is. Because in many ways these figures can’t touch the real cost of insecurity on the Internet. The cost of humiliation and identity theft and privacy traded away. The lost time, the worry. The myriads of tiny personal tragedies that we’ll never hear about.
I have to say, when I was looking for this I was looking for a webcam picture of someone picking their nose, and it took me a while to find one that wasn’t blurred out. Also, I was too lazy to blur it myself.
One media report in the US estimated 8,500 schools in America have been hit with ransomware this year. Now, the reason why I think it’s really interesting to point out the American figures here is this is also a national system where as of last year, half of all students in US public schools qualify for poverty assistance. Those are the people paying these ransomwares. And it’s hard to get a real figure because most schools are hiding this when it happens. One survey I was looking at showed that half of hospitals in that survey had been hit with malware, often multiple times. How do we quantify that kind of damage? How do you quantify when duty nurses are too nervous and stressed out to get their procedures quite right? What is the cost in that?

In traditional stalking as we’ve known it, this gets really dark really fast. And those are the figures for what we think of as traditional stalking. Of course, the Internet has added a new layer to that. But also nobody how solid figures yet for sure in how the Internet is changing stalking, except that it’s making it a lot easier. Weirdly, possibly the biggest losers in that are men, whose rate of stalking is double online what it is offline.
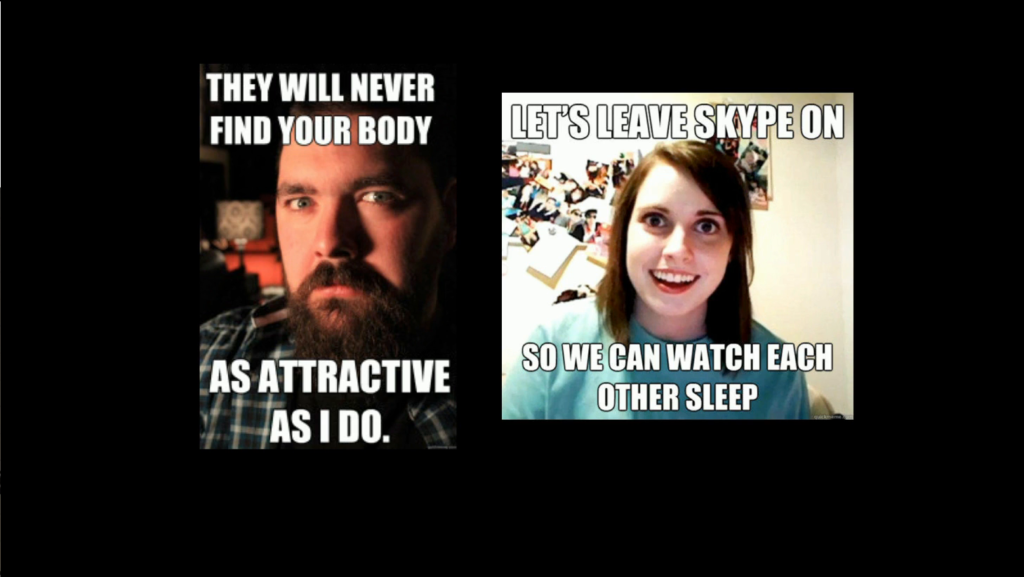
And this translates into a lot of creepy moments that cross these barriers on what makes you feel safe in the world. Because what happens with computer insecurity, what happens with small adversaries, is they tend to meet and amplify our basic human flaws.
And in the end, some of the most terrible things are the family and intimate partner violence that we see all over the world, whether we call it spousal abuse in the West, or honor killings in Pakistan, or gay kids who can’t find help, or teen girls who can’t find health and birth control services because of content filtration, because of management by families, administrators, schools, communities. All these things are part of the cost of small adversaries. Perhaps the greatest and hardest to quantify cost of our terrible, terrible security culture is the sense that so many people have—even the people in this room—that they have to fear the very thing that they must rely on for their lives and livelihood.
So, this is obviously a very different landscape from most of what we’re seeing in the media. And most of what we’re seeing in the media these days especially, post-Snowden and so on and so forth, is this discussion of these super-powerful actors who are spying on everyone but honestly not doing that much. And we’re still looking at this paradigm coming from law enforcement and from global governmental conflict that kind of talks about these things in terms of good guys and bad guys and discrete criminals. But treating adversaries on the Internet like discrete criminals is ridiculous. It’s bringing a gun to a locust swarm. The Internet will always make more asshats. I promise you that. The asshats are endless. And that means that essentially what we’re doing in security is threat modeling our environment really really wrong.
https://twitter.com/evepeyser/status/758141126352273408
I don’t know how clearly you can read this but it’s somebody asking a teenager why they’re using Snapchat. And we’ll come back to this point. But this teenager is threat modeling very well. I believe it’s a her, but she’s saying yeah, that she doesn’t care what governments do. Parents always been the OG Big Brother. And I think one of the things that this points at that is really important is that we live in an [as above, so below] network, that what big guys do, small guys emulate. And what small guys do, big guys pick up. It’s all traversing this hierarchy much more like an ecosystem than we often think it is.
Nobody can really tell us who’s acting for sure. And something that say, a big actor puts out there, the small actors can find. They can pick up. They can use it directly, or they can emulate it. I mean, we’re working in the first threat environment, basically in history, where generally the things people throw at each other, they can just pick up and use again. Now, it’s not the first time. This is an idea that goes all the way back to Rome versus Carthage, when Carthage was winning because they figured out how to put together all their ships like IKEA flat packs and Rome caught one of them and found out what the numbering system was for putting the ships together. And in a way, what we’ve done is we’ve taken that same threat model, that we’ve taken that same problem and moved it into our infinitely-replicating machines. It’s the problem that we have every on every desktop. It’s the Carthaginian fleet being taken over by the Romans.
But in an environment where everybody can pick up everybody’s tools, we’re all weirdly empowered now. And I mean kind of weird in an almost fey sense like, our powers are weird, they make us weird, and they make our conflicts weird. It’s again that idea that our tools are interacting with our human flaws in really really interesting ways.
And let’s talk about some of the tools, because we all know these tools. They’re remote administration tools— The tools of small adversaries are the same tools that we are recommending to people that they use against small adversaries. Remote administration, encryption, email phishing, ads. We told people to install AVs and updates to their machines, and now malware often looks like AV and updates.
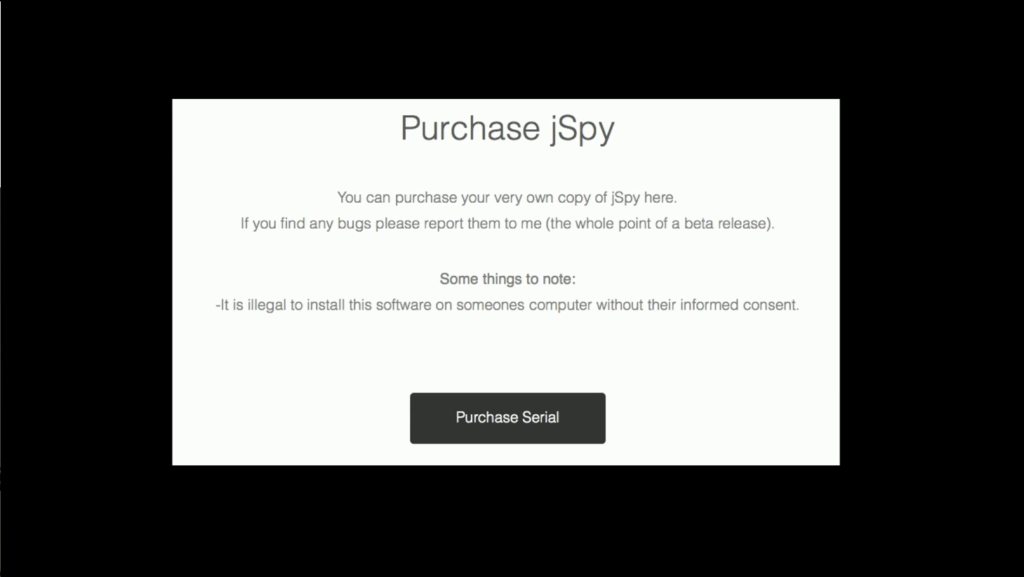
And everything in our fields is dual-use. Everything that we can use to help somebody can later be repurposed to hurt them. Our sorrows come in battalions these days.
“For security reasons, I cannot give you SSH access to the box but you can use TeamViewer via my desktop.” pic.twitter.com/9ewmSyzInw
— Raphaël Vinot — @rafi0t@social.yoyodyne-it.eu (@rafi0t) August 29, 2016
And even our own understanding of how our tools are working gets really confused. This is just one of my favorite tweets recently. “For security reasons, I can’t give you SSH access to the box, but you can use TeamViewer via my desktop.” The fundamental misunderstanding. It’s a sign that we’ve kind of lost the thread of how these systems are working. We want to fix things, but the most common complaint I hear are this disconnect between the information that can help and the actions that can implement that information. Understanding a system and then acting on it in a way that creates change. And these are the places in which both naïve and sophisticated users are disconnected, at this point.

So this is all really heavy stuff, and I want you to go ahead and take a moment with a kitten picture so we can stop thinking about bad system administrators and people being killed by their exes. Or we can keep. I don’t know.
But I do want to emphasize in this that most people who are pulling a paycheck in this field are not interacting with the pain that most people are experiencing from network insecurity. Because you end up working for people who pay. And that high school… That was a 1925 picture of my own high school. That high school can’t afford anyone in this room. And that means that so much of this pain and insecurity in the world isn’t readily visible to the people who work in the field, who are supposed to be fixing it.
It’s not entirely on you guys, or on even the crappy programming that makes this happen in the world that so much pain is caused by the network these days. But it is the fact that we are all going to have to be part of the solution to this project if the 21st century network is to improve.
Now, I want to turn around a bunch of this heavy stuff and start talking about where we start to fix these systems. Because the truth is we have, as a field—and I don’t want to limit that just to security. I think this is true of all of technology. We have left the biggest and best tool we have on the table. Each and every one of these machines on the Internet at some point has connected to it the most complex and sophisticated pattern matcher that we have yet found in this universe. It’s got a human attached to it. And they’re not part of our security models. As a matter of fact, we generally see the human as a liability.
But we’re leaving a huge amount of computational power on the table right there. Right now, your users should be the ones who are advocating for the security changes that you want to see in the world. And they’re not. Right now there’s a lot of conflict between the people who are trying to secure things and the people who are trying to use things. And that’s ridiculous, because you have the same goals.
One of the things that I’m always baffled about is when we’re trying to figure out what’s going wrong with a system, we’re not asking the person who knows what should be happening on that system. Should there be a bunch of traffic going to IRC? Well, I actually know whether or not there should be a bunch of traffic going to IRC on this box. But no one has ever asked me, in any of these systems. No one has ever kicked up something saying, “Does this look right to you?” And yeah, we’d have to find a language to do that, but what an amazing piece of information you don’t have in a system when you’re not asking the human if that’s what they’re doing right now.
Humans love to respond. I mean both as animals, and as employees. They love to respond to the restriction of systems. So one of the things that I’ve wondered in the past few years is why we don’t take systems of data that we don’t want exfiltrated and put them on narrow bandwidth connections? Let that get annoying. If you’ve got like a giant patient database, why not put it on your network under a 56k connection? So if somebody’s trying to pull it all, someone’s gonna notice. Because there’s no reason. When you have vast amounts of people’s personal data, there is basically no reason to pull it all at once. If somebody’s doing that it should hurt the network. And people can respond to that pain.
That’s like one example. I think probably if we brainstormed enough, we could come up with a hundred examples of ways in which people could respond to what’s happening on the network in ways that would be faster and easier than trying to get the machines to respond. Because people have context. People can match patterns. People know which kitten is cute. Machines don’t do that. Machines are good at adding things. We’ve got a system that’s good at pattern matching, and a system that’s good at math, and we keep trying to tell humans to do more math. And computers to do more pattern matching. That seems like we’re missing a few opportunities there.

And then, one of the biggest things that we need more of between users and technicians in the 21st century is more respect and more listening. We spend a lot of time telling users they should listen to us, but we don’t spend nearly as much time listening to users. And partly that’s because users don’t normally speak the languages of technicians. But that doesn’t mean that they’re not passing you information. Even in consumer choices, users are passing you a lot of information. If you look at these applications here, applications and behaviors, they’re trying to solve the same problems that security teams and system administrators are trying to solve.
They’re trying to go through things like Dropbox to get away from the problems of of malicious attachments. They’re trying to reclaim privacy with things like Snapchat and WhatsApp. And I think that these behaviors on their part are fantastic and should be encouraged. A lot of people will step in and go, “But you know, it’s all lies and there’s all these other problems.” But that doesn’t mean that that was the intention of the user. The intention of the user was to fix the systems they were in. And that intention, that’s interesting. That means we’re on the same side.
So if Snapchat is lying to its users, then we need to take these lies and make them true, in the famous words of George Michael. We need to take these tools to the places where the users are and help them understand what state they’re in at any given time. You know, we went to Google mail, and part of the reason people went to Google mail was because this shit was not working for them. Because they’re trying to solve their own problems. And they went to these very specific behaviors. Like our fourteen year-old girl who went to Snapchat to avoid her parents. Like the myriad of teenagers who have hopped from social network to social networks so that they could describe a safe space for themselves.
You know, we live in an age where asshat marketers will tell us that kids and people don’t care about their privacy. They’ll trade it away for a coupon. But it’s just not true. I don’t know if you remember being a teenager, but teenagers are incredibly privacy-seeking. How many of you always were cool with your parents walking straight your room? Was that cool? I mean, if it was totally cool, raise your hand. I’ll point you out.
But for most of us, we definitely wanted—every one of us has doors on our bathrooms. We all want privacy. So why is there a disconnect with the Internet? A lot of it has to do with digital literacy. And a lot of it has to do with what’s going on. And the fact is we need our tools to work for us, first and foremost. While all of you have a door on your toilet, all of you will use a toilet without a door if you need to. I promise. And that’s one of the things I want you to think about when we’re talking about security stuff. Because in the end, one of the conflicts that comes up over this, one of the reasons why users are seen as a point of insecurity, is because getting the job done is more important than getting it done securely. And that will always be in conflict. You will always be ready to use [a toilet without a door]. If you really need to.
So, people are not stupid about their security and their privacy. But they’ve been lied to. And that’s part of the problem that we as a community are in a position to help with, to fix. And one of the other things I think gets disconnected between technicians of all stripes and the people who are not in their fields is that we often think people don’t listen or don’t care because we forget that this isn’t other people’s jobs. If you are sitting in this room, to some degree people are paying you to use a long password. People are paying you to to worry about key management. If you are a trash collector or radiologist or a lawyer, this takes away from your work day.
So honestly, one of the reasons we want to bring good tools to where people are is because if you have a radiologist, you don’t want your radiologist to learn PGP. I promise. You want your radiologist to look at your frickin’ scans. You want them to look at it again. You don’t want them to worry about whether their communications with you are encrypted. Because that’s time that they’re going to take away from trying to spot something on your lungs. Which would you really rather they do?
So, we specialize in society for a reason. Because we really want people to pick up our trash. We really want people to defend us, or protect us, from the law. We really want doctors to find the things and fix them that are wrong with us. And we really don’t want those people taking their time away from that to learn how to do what we do. Until you are ready to go spend a day of the week picking up everybody else’s trash, you’re not in a position to tell everybody else to learn how to do your job.

And I think one of the things that is kind of a cultural disconnect for our century is that nobody got into computers because they wanted to deal with nondeterministic systems. I mean, even from like age nine when I started, the great thing about computers versus everything else in my life was that they did exactly what I told them to do. So we in society in general, one of the ways of talking about human history is that we were in this crazy state of nature where lots of things could happen and eat us, or crawl inside our bodies and kill us. And we created these walled cities, we created these civilizations to get more control over that environment.

And then inside of those barriers of civilization, we started creating more and more and more complexity until we finally created a network that is no longer deterministic. So right inside of all that civilization, we created the weird again. And so that’s where we are now. We’re inside of a civilization that has created a network that is ecologically weird again. So I’m sorry. We got onto this because we like determinism, but we’re going to have to deal with nondeterministic systems. And part of that nondeterminism that we’re all facing is the human appetite, it’s the human mind. And it’s the power of the human mind.
So, I think we all kind of think of ourselves a lot of the time as like, edging on to math and physics. But closer, I think, we’re dealing with biology. So I think all of you are slowly transforming into really weird biologists. And when you’re inside of nondeterministic systems, and when you’re talking to biologists, one of the things you will find out is that the first job of biologists is to listen. It’s to listen to these systems. And to let go of a certain amount of control. Not just to the words people say, but to the needs that they’re describing.
You know, one of the reasons that we live in a security nightmare is because everybody still needs to use email. Usually to pass files and to get to things that are not their email. If we all just used text email it wouldn’t be quite so bad. So how do we meet those needs, personally and organizationally, for passing files on the Internet? And yes, I still wake up a lot of mornings saying, “It’s 2016. Why can’t we still pass files on the Internet? Why is this still a problem?” I definitely thought this problem would be solved by you know, the mid-90s.
So, when I talk to people about this stuff, and I take time to explain systems to them, I also get them to describe the systems to me that they’re interacting with. And even when they’re wrong, they’re not wrong. They’re describing their experience. And one of your jobs, if you’re trying to create a system that works altogether, is to figure out what they’re describing about that system through their experience.
One of the one of the early ones that I did many many years ago was that I interviewed a bunch of people about their experience of certain software, and they would consistently say, “Oh, this is the part where it thinks. The computer has to think here for a while.” Most of the people I was interviewing were older, in this particular user set.
And what I realized was that what they were telling me consistently when they say “my computer has to think about it right now” is that my computer is swapping. And this was the 90s. Swapping was kind of a bigger deal in some ways at that point. But I was able to learn something about the architecture of the software from this very colloquial way of talking about computers. There’s so much more there. There’s so much we could be gathering from how people are using systems, what they need. And when we meet those needs, or work with people to meet those needs, we start creating mechanisms for them to understand their own lives, and behave better in the systems that we’re working with, and we get more free time.
Because people, I’ve got to say, people are brilliant. They’re amazingly brilliant. I mean, the same people who think they’re idiots know how to fill out forms and drive. Which is kind of amazing when you think of starting off as hunters and gatherers. We’re really interesting, adaptable people.
We’re leaving a lot of interesting techniques on the table as well. Ways of teaching our users things. My favorite form of software interfaces is games. And not just because games. But because games have lots of interesting problems to solve and they just went through and solved them. And we should probably be picking up some of these techniques.
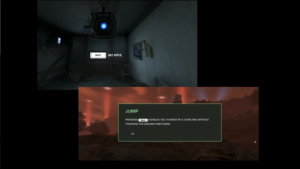
So these are some screen shots from tutorial modes of different games. And what we’re doing here is we’re letting quite complex systems explain themselves to a user. And this is something that the gaming field has spent a lot of time working out. Complex, internally-consistent systems being taught to the user at the very beginning of use. And I mean, some of it is fantastic and brings in humor, and then it’s like, the bottom here is actually explaining to you what a jump is. At the same time, when explains to you what a jump is, it’s both humorous and it makes a connection to things that you know from your own physical life into into a gaming environment. So these tools are out there. We can start studying them. We can start picking them up.
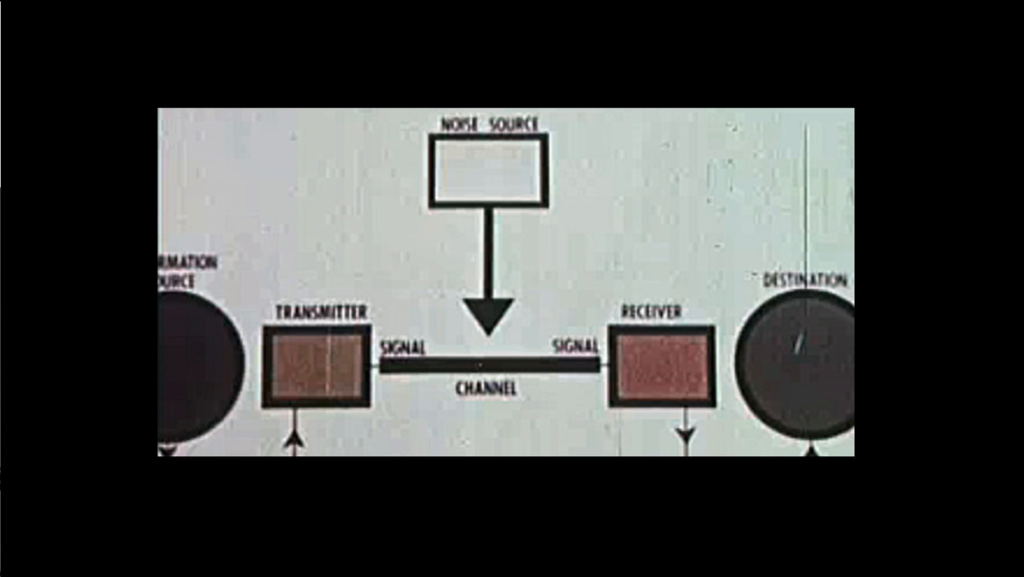
“A Communications Primer,” by Charles & Ray Eames (1953)
And generations have been scrambling. Generations even within our grandparents’ time have been scrambling together a lot of the information that we need to create these literacies. Like, fundamental literacies about the world we’re living in. This is a screenshot from the Eames’ primer on communication theory. When I start to work on digital literacy, I don’t start with tools. I start with the basic frameworks of thinking that the tools fit into. Because then people ask me the right questions. Then people ask me things like, “But wait. If I start using encryption and nobody else is, don’t I stand out?”
When I hear that question, I’m thrilled. Because what that tells me is the other person is starting to model the system in their head. Which is how humans work. So the thing I hear consistently is that nobody wants to learn this stuff. John Oliver’s line, “You smell like canned soup. Leave me alone.” I hear from security people that we can’t teach them. We can’t teach them digital literacy. But I think that we also have to recognize that security requires respect, a mutual respect. And right now there’s not a lot of respect between the users of the Internet and the technicians of the Internet, either way. And somebody’s going to have to start bridging that.
And it all feels really impossible to a lot of people. And there’s a lot of people who’ve said that it’s just not doable, we’re going to have to figure out how to have a 21st century Internet with nobody knowing how to use computers. And I don’t think that’s either true, or possible.
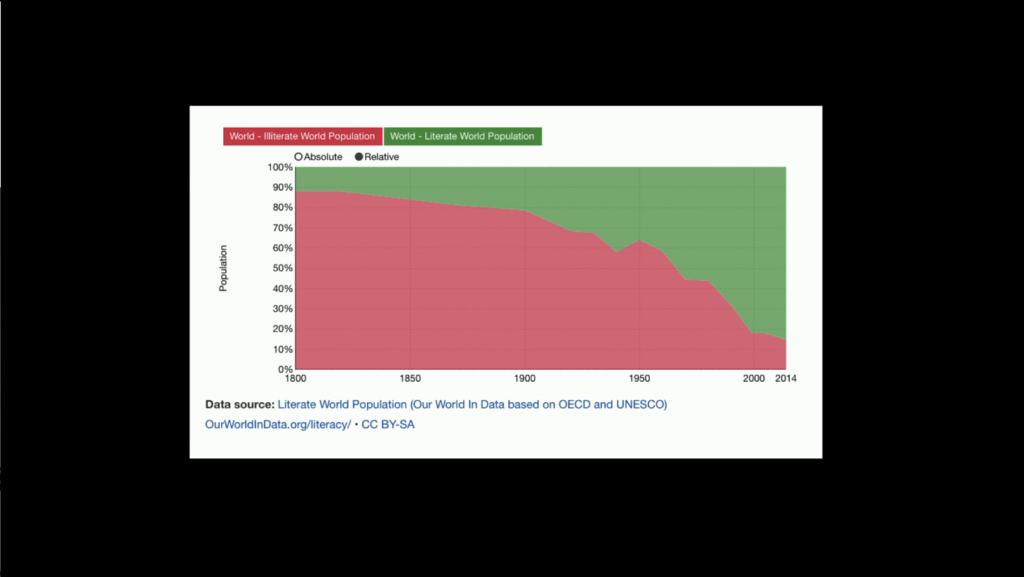
Max Roser and Esteban Ortiz-Ospina (2016) – ‘Literacy’
And I want to pull you back into the last, I think, great projects that was like this. It was the great political project of the 19th century, which was are creating democracies. Devolving power from aristocracies into democracies. And there was a realization pretty early on in that process that you couldn’t have illiterate democracies. So one of the great projects of the 20th century was to teach everyone how to read. And if you think teaching everyone what a computer is is hard, try taking billions of people and teaching them how to read. That’s a big ask. But this is what we did. We went from a 20% literacy rate in 1900 to over 80% literacy rate by 2000.
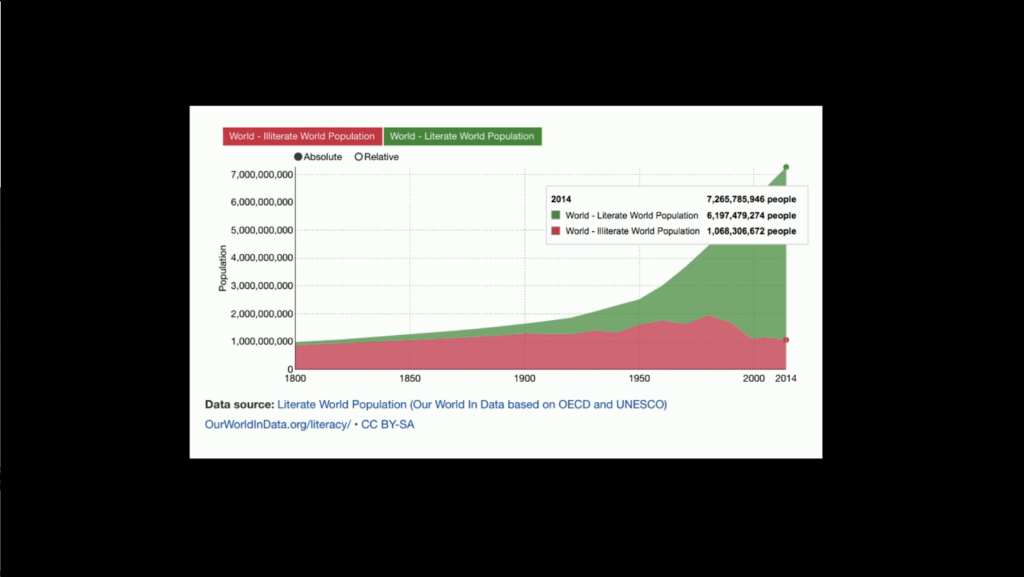
Max Roser and Esteban Ortiz-Ospina (2016) – ‘Literacy’
And if that’s not impressive enough, let’s take it from looking at those percentages to looking at absolutes. That’s the literacy rate. That’s what it did. That was an amazing project that humanity pulled together to do. And in case you want an even more impressive number, let’s look at that absolute figure at the end. Because that’s 7.2 billion basically literate people in less than two hundred years. That was really hard. We had to pull together a lot of resources. We had to get a lot of people who weren’t traditionally talking to educators and weren’t traditionally educators into being educators. We invented a lot of institutions for that.
And here’s the great thing. We, in the 21st century, get to reuse those institutions. We don’t have to build them again. We can start bridging between the people who work in the companies that we work for, but also the schools that work in the area that we’re in. I really want to get more people in this community talking to educators. Starting to bring in that generalized knowledge, that conceptual knowledge. Start getting it in there early. And that’s when we’ll really start seeing this landscape change. It’s not just getting everybody to install a Flash update. It’s getting them to understand what all those words mean so they’ll figure out to do it themselves.
And then we get to have a really awesome Internet. Because right now your biggest enemy, and one of the biggest enemies in the 21st century, isn’t evil hackers, or APTs, or big governments, or organized crime, or even lazy programmers and apathetic management. Your biggest enemy is the fundamental fear and helplessness people feel when they pick up their Turing machines. When we start to beat that, we’ll really be getting somewhere.
Thank you, and I’m happy to turn this into a discussion and take questions.
Moderator: So. Lots to think about, as usual when Quinn’s around. Questions?
Audience 1: I mean, if you learned to read in the 50s, you know how to read now. But if you learned how to use a computer in the 90s, you don’t know how to use a computer now. So computer literacy is much harder to [report?].
Quinn Norton: I fundamentally disagree. Because I think in my lifetime, the fundamentals of digital literacy have not changed. You know, when it comes to understanding the— This is why I don’t teach tools. Yeah, if I taught you one book about how the world works in the 1950s— And I have a book actually from 1900 which was a reference book of all the things you would need to know from the 20th century. It’s great. If that was your only book, absolutely your literacy would not help.
But if you’re getting the idea that you can kind of read future books because you’ve got this one book— If you can understand what a Turing machine is— And this is the thing, is like, I find when I am teaching, that when I start by explaining what a network is and what these machines are, then things start to make sense. Then I can say okay, here’s a tool. I’ll tell you what the tool is, you tell me what it’s doing. And that knowledge is lifetime. Because frankly, Claude Shannon is going to be right until the heat death of the universe.
Audience 2: A question comes to mind when I speak to some people about encryption or whether or not we can communicate over PGP or Signal. This is something that I thought was a popular way of thinking before the Snowden revelations, but it still persists, which is why don’t we communicate over signal, why don’t we use PGP? And they’re like, “Well, I don’t want to be suspicious.” And I’ve spoken to a number of people, for example who work on Iran and they fear that the US government might be spying on them. They’re like, “Well, we have nothing to hide so we’re okay with them reading all of our stuff anyways.” And this sort of stance towards privacy still exists, and I just want to know how you sort of approach this.
Norton: Yeah. And I encounter this quite a bit. I mean, one of the one of the first-offs on this, and and I like to point out that the most successful encryption that we’ve ever done is the one that we didn’t have to get anyone to use, that was that was kind automatic, which was SSL. Like, the only big adoption win the security community has ever had is SSL. So, explaining to people that they’re already using it is one of the— You know, if you shop online, if you read your email over something that’s encrypted, if you log into things… If you log into things, you’re already using encryption. Because it’s infrastructure.
So getting people to understand that it’s infrastructural gets them I think much faster past the point of let’s just stick another level of infrastructure on our communication. I feel like this is starting to change in a positive way also, because of people starting to develop tools for dealing with context collapse, which is a whole ‘nother talk. But like, that idea that their stuff can be taken out of context is a reason why you can get people to… Seeing their stuff taken out of context gets people to the point where they’re much more interested in encrypting things that they don’t want taken out of context. And that for me has been the win with people who want to live very open lives. Like, I will say live your open life where you want it to be open, but where you don’t want to be recontextualized let’s use encryption. And that helps so that they can see that the minutia of life is often the thing you want to encrypt much moreso than the big declarations of life.
But again, for me it always comes back to explaining the infrastructure. Explaining the underlying thing. That’s where I get all my wins when I’m doing training. If you log into things, you’re already using encryption. You do have something to hide. It’s not…a shameful thing, it’s just your password. I hope that helps.
Audience 3: I’ve got a question, Quinn. You ask people to get involved with the local educators. How do you recommend them doing that? There’s lots of brains in this room. Lots of skills and experience. How can everybody in this room go out and get involved with the local educators?
Norton: You know, this is very country and location dependent. Well, there’s a lot of youth education in hacker spaces. And if there isn’t local youth education in hacker spaces, I think it’s worthwhile to kind of set something like CoderDojo up in your city. Take a little time on that. And that’s a beginning, because it starts to kind of get into kid space with this sort of stuff, where you’re starting to kind of just getting people interested in a very non-threatening way.
I mean, it’s entirely possible to talk to local educators, just formally either talk to the district or I don’t know the shape of it where you live. But talk to a school, talk to a district, and say, “Hey, I’m interested in helping with digital literacy issues.” And right now I’ve got to say I’ve spoken to educators around a lot of the world, and there’s nobody that’s like, “Digital literacy? We’re not interesting in that. I don’t see how it’s relevant.” There’s not a single school district anywhere in the world that is saying that right now. Everyone is desperately trying to grapple with these problems.
And everyone’s kind of trying different approaches, and a lot of it’s very haphazard. And very very little of it is connected with the people who are doing this work in their day-to-day lives. How many of you have done, are connected with, or are doing any work with educators at this point? Raise your hand. How many of you have kids? Right.
So a few of you have a bit more in this fight than the others. So if you’ve got kids and they’re getting involved with schools, one of the places you can start is the schools where your kids go. And if they can’t work with you because of often bureaucratic things, say “Where do I go next?” I know that we don’t have a lot of time in any of our lives, but this is kinda worth it. This is worth at least taking a little bit of time. And even if you get to the point where you can’t do a lot, even if you know where the interfaces are and you can tell other people where they are, that starts getting the information out. And it starts connecting the two communities. If you just find out this is the person that you talk to at the school or at the district if you want to be helpful in these things, if you want to contribute to a curriculum or something like that.
There’s also really really interesting stuff going on in places like YouTube, where people are doing a lot more fascinating and educational material. If you’re ambitious, you can put stuff up there. If you’re less ambitious, you can advise people who are trying to put that sort of thing together. Just getting the knowledge out there, being a resource, I think is one the places you can start, and finding the people who need you as a resource.
Moderator: Any more are questions? No?
Norton: Well, thank you very much.
Further Reference
Interview with our first Hack.lu 2016 Keynote: Quinn Norton at hack.lu