RenderMan: So, yes. I am RenderMan. This is Murdoch Monkey. Just you know, I did a little biohacking on my liver last night, and so when I was working the slides guess who forgot to hit “save.” So I was just sitting in the back hacking together something, so if this seems a little disjointed I apologize.
This is a serious talk. Let’s…you know, try to be adults here. Vaguely. I mean, there are no children in here, right? Okay, good. I don’t want to pay any therapy bills.

So yes, Internet of Things. We all know about it. Manufacturers do not… You know, the security on them’s terrible. They don’t have a way to update them, or they just don’t care. Users don’t consider the security and privacy of using these things until it’s way too late. Groups like I Am The Cavalry are doing amazing work on automotive, medical… But nobody wanted to touch sex toys for some reason, so. But you know, this shows that IoT is permeating every part of our lives, including one of the most private: bedroom activities.

So, yes. Sex toys are now being connected to the Internet. For a lot of people that’s…they can’t grok that initially, let alone that there’s security issues. Basically what we’re looking at is sex toys, kegel exercisers, genital rings. If it goes into your genitals, your genitals go into it, or goes around genitals, those are the devices we’re worried about.
A large number of IoT research firms…yeah, they don’t want to look at this. Because there are stigmas around sex. We have a very weird thing in North America about sex. We’ll watch all the violence we want on television but you can’t see two people have sex. Like, it makes no sense to me.
So this started basically because I had had the idea rolling around my head for about ten years. Happened to mention it to the purveyor of an adult toy store back home in Edmonton. And she was like, “This is a good idea. I do all these in-home demonstrations.” It’s like a Tupperware party but different kinda Rubbermaid. But it’s like yeah, “I’ve got some old models. Ones where the batteries don’t work or a broken power connector…” and gave me these old demo ones. And I started diving into this stuff, and shit got real, real quick.

Because when you now realize it, the question is, is hijacking the remote control of a connected sex toy sexual assault?
I hear that uncomfortable giggling but no, think about it. You know, you have a partner. You give them permission to control this device. Someone else hijacks the connection. That person does not have permission. That fits the definition of sexual assault.
There have been several cases of rape by deception, where it was like if your twin brother has sex with your wife kind of a thing. It’s very interesting because they usually are dismissed on some sort of technicality. And I’m not a lawyer. I really want to put an interesting query into the EFF about this. Canada’s sexual assault laws specifically define consent obtained by fraud is not consent. So in this case yes, if you’re impersonating someone by hijacking their account or whatever yes, that is not… Consent goes to the person at the other end, not the account.
But it gets really weird when you start looking at laws because these are devices that’re voluntarily used. It’s the same data that their intimate partner would be sending, but not by that same person. But if they find out that it wasn’t the person you thought it was controlling it, the emotional horror and trauma from that should not be anywhere dismissed or feel any less than a physical assault.

You’ve probably all heard about the We-Vibe lawsuit after DEF CON last year. For those of you who weren’t around, Goldfisk and Follower did a talk where they found a number of issues with the We-Vibe. Full disclosure, I had actually put in the exact same talk that came to the exact same conclusions as them. They got selected. They were first-time speakers. I’d spoken way too many times here.
All boiled down to they didn’t have the right privacy policy in the app. It basically was the privacy policy from their web site. So it was mentioning you know, cookies and stuff like that. It didn’t disclose some of the information that they were collecting from the app and the device. And yeah, they got nailed to the wall because hey, if I had known that this was doing this I wouldn’t have bought it. Deceptive advertising, such.
Absolutely no evidence of malfeasance. Data didn’t leak. They weren’t abusing it. They weren’t doing dossiers on users or anything. It was just literally a paperwork oversight. So the biggest lawsuit regarding all this stuff had absolute nothing do with actually technical privacy or security but just legal paperwork.
They settle for $5 million in a class action lawsuit. And we should be finding out in the next two, three weeks how much people actually get out of that. Could be up to ten grand if you’d used the app and the device.
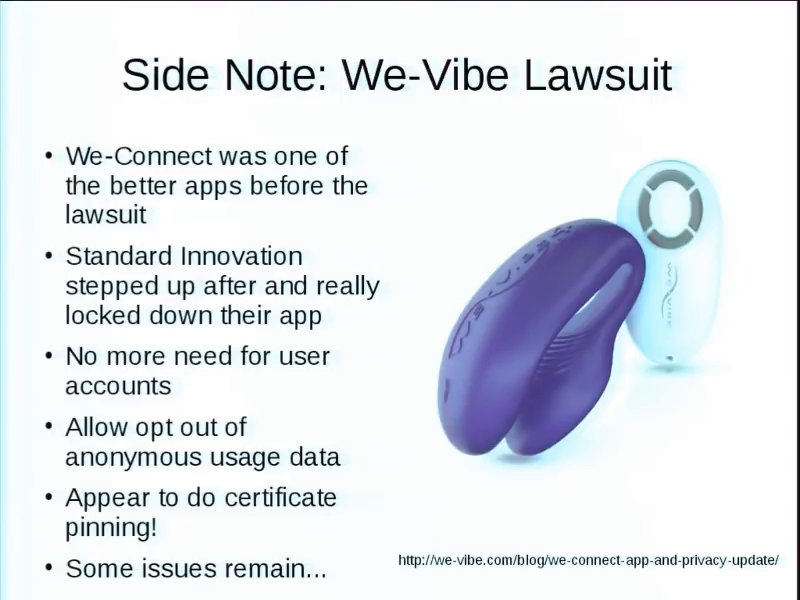
The interesting part is We-Connect was actually one of the better apps, even before all this. They were one of best ones I had tested. They still had some issues, but yeah, they were actually doing SSL at least halfways right. They were doing a lot of things that you would expect.
After they got hit with this lawsuit and the Goldfisk and Follower talk, they stepped up and basically completely reengineered their app. It’s now kind of like the gold standard I have for other vendors. It’s like you need to be doing all the stuff that they’re doing. They got rid of things like you don’t need to create an account to use it. So there’s no personal information being collected there. Allows for…you start it up the first time, it says, “Hey, would you like to opt out of anonymous data collection?” Cool. Gives people the chance right there, the first time. Looks like they’re actually doing certificate pinning. Like holy crap.
Still some issues. My favorite is that you still can’t visit their website over SSL. And I’ve been hammering on them on that for like eighteen months and they still have not gotten back to me at all. It’s just…it’s hilarious.

You’ve probably also heard about the Siime Eye controversy. This is a vibrator with an embedded webcam. Hey. I don’t judge. Basically because it’s doing video it needs bandwidth. And so it uses WiFi. When you start it up it becomes its own access point. So you connect your tablet, phone, whatever, to it. So it’s not actually connecting to the Internet or anything like that. So you view the stream. Control it from your phone. It’s basically Ralink System on a Chip running BusyBox. Interesting to note, I smuggled my GPG keychain across the border, on a dong. Because there was about eight megs of storage available on here. Proof of concept, had to do it.
Also there is the embedded web server, and yes I have actually hosted a web site…you know, an Internet on a dong. Literally all it is is a reworked cheap Chinese IP camera that they made fit into a particular container.

That’s a picture of my nose. Pen Test Partners, Ken Munro… Is he here? No? Okay. He’s probably over at IoT Village. Literally this thing was in the air from Amazon when they released their report. They had found all the same things I had already in the software, and I didn’t have the hardware yet to confirm the last few. While the report was factually correct, there was a lot of innuendo and jokes and just juvenile humor. They released it under a pseudonym of “Beau du Jour.” And it’s like…really guys? Come on, we’re professionals here.
So I took some exception with that, posted a rebuttal saying that yes your evidence of risks was true, but you blew it out of proportion. Like oh my god, these things are WiFi so they’re broadcasting to anyone and wardrivers can pick this up and add it to wigle.net. Now you show a screenshot wigle.net.
Well, if you actually log in to WiGLE and use the Siime Eye SSID in search, you find two. Both of them are at roughly the same location outside a four-story sex shop in downtown Tokyo. So out of…I forget how many they’re up to, there are like 600 million access points cataloged, two. And it’s demo stuff in like an incredibly packed part of town. So like yeah, the risk is very very minimal on that.
Yes, there was a default PIN that interestingly, their previous software didn’t give you any way to change it, or none of the instructions. It would tell you repeatedly “change the password, change the password.” But not how.
So I posted this rebuttal, and working with Ken Munro on that, they made a bunch of press but unfortunately this whole project didn’t get mentioned so I’m like, [fist in the air] “Ken!” But no, it got them on same page. But it shows that people are paying attention. That the public is now considering this.

So vendors were already freaked out by the We-Vibe suit. Seeing this getting dragged through the mud didn’t help them much either. It was also a great example because they had tried to do a coordinated disclosure with the vendor, but they never replied. This is why you need vulnerability disclosure programs that actually are acted upon.
The problem with these things is that you have the potential for really dumbass regulations and stuff like that. I mean you’ve got some 70 or 80 year-old geriatric congressman or senator trying to figure out this technology and it’s like, “Oh my God, that’s aberrant! Sex!” considering that they’re probably also doing their secretary or something. Yeah it’s like you’re looking for solutions to a problem that doesn’t exist. It may not be your thing, but doesn’t everyone deserve privacy and security in what they do, even if you don’t agree with it? If not, you’re wanting people to be hurt, you’re a terrible human being. And it’s issues like that that are why I started this project.

So internetofdon.gs. In case you’re wondering, .gs is South Sandwich Islands. I had actually inquired with some friends that issue CVEs. There’s a big thing with IoT stuff, they don’t know how to issue a CVE for some of it because it’s using other projects’ software but it’s only for this device configuration… So I was like screw it. So I’m doing Dong Vulnerability Exposure IDs, mostly for my own sanity. When I was submitting things there would be like half a dozen things that I wanted to make sure that none of them were forgotten. So having an identifier helped.
But also the reports. You can actually start seeing what sort of issues are happening. I’ve already helped a number of vendors build vulnerability disclosure and management programs. Because if somebody finds something, why the hell aren’t you just making it easy to report? They’re giving you free work. Like…makes sense. Again, nonjudgmental, just want to have people use these things privately and securely.
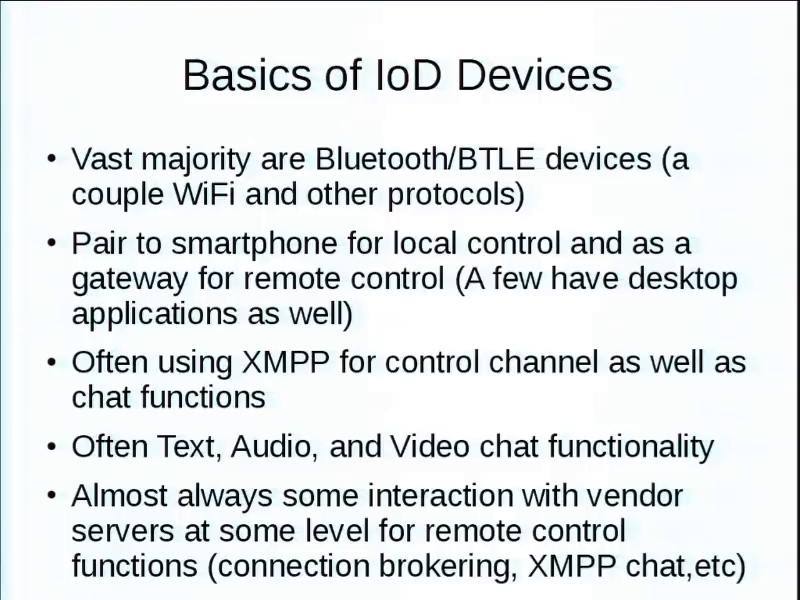
The vast majority of these are Bluetooth. Bluetooth LE. This is about the only WiFi one. They pair to a smartphone or tablet for local control, but also as a gateway for remote control via the Internet. A few have some desktop applications. XMPP is a very common control channel on these. It provides you text chat functions as well. But they’ll also do text, audio, and video chat—full-fledged video teleconferencing teledildonics. Sweet. So lots of interesting attack surfaces there, when you think about it, between the text, the audio, and the video.
Almost always, there’s some sort of interaction with a company server for brokering the connection or finding each other or something. But trying to convince vendors you need to be as hands-off as you can possibly be. Because yes, it might be easier to do things this way where you tag unique identifiers to everybody, but…no, that’s where things get weird. So the more hands-off you can be, the better.

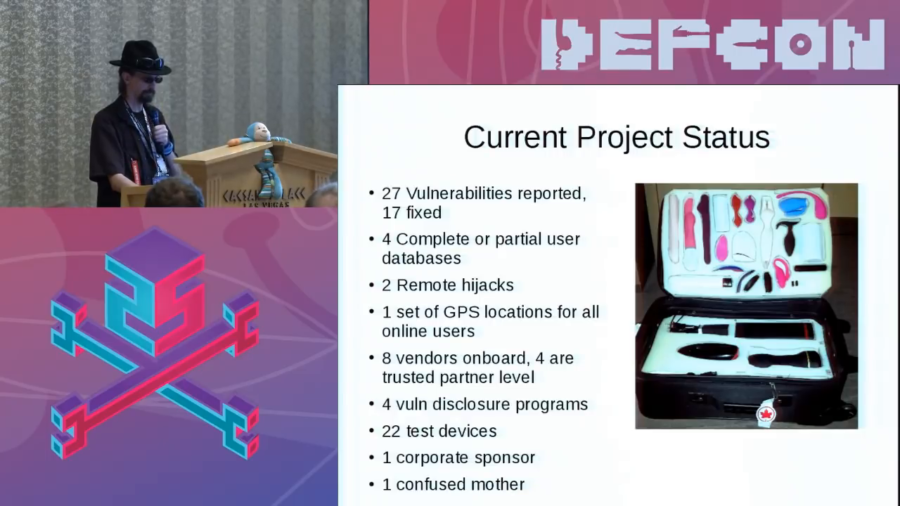
So, so far twenty-seven vulnerabilities reported, seventeen fixed, though I haven’t checked in the last week. Four complete or partial user databases. Two complete remote hijacks. One set of GPS locations for all users that were online at the time. I’ve got eight vendors that’re on board with doing vulnerability disclosure programs. I’m helping them basically to realize hey, you’re a software company now whether you want it to be or not; you’re gonna have to do certain things.
Four have reached what I consider a trusted partner level. It means that they have a very good and well-established vulnerability disclosure program. They’re being proactive, and just fully embracing the idea that okay, we need to be secure. Twenty-two test devices in this lovely hand-cut foam case. Which is really fun as carry-on. One corporate sponsor, and a very confused mother.

So yes, we are supported by Pornhub. Wait, you’re all familiar with it? Oh, I thought it was just some obscure little site. Drunken email to their marketing people saying, “Hey, here’s the project. Going to buy some of these devices. They’re expensive. You know, can you somehow?”
Immediately got a reply, “Yep, we’re on board. We love this.” Originally they were trying to get some of the vendors to send free stuff. Eventually just settled on, “Here’s a big pile of cash.” So yes, I had a bank transfer from Pornhub for keeping my clothes on. That just seems…weird. But again, try and explaining that one to your mother.

This is really weird research. I’m generally not embarrassed or shocked or anything like that. But still it’s… The things you see…you know, it’s not necessarily for the timid. Because people have some interesting fetishes. There are people who like the idea of a random anonymous person on the Internet controlling their vibrator. But that’s you know, informed consent. That’s your thing.

But the vulnerabilities that you find are shocking. Not everyone knows how to do SSL, if they’re using it at all. User information, personal information disclosure, partner disclosure, GPS, permissions, blah blah blah.
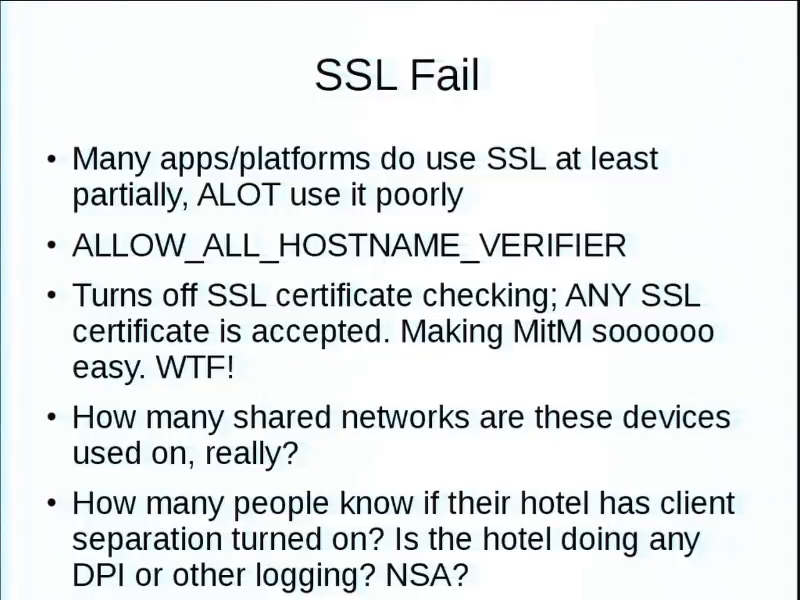
I’d say at least half, if they’re doing SSL, “allow all hostname verifier,” which basically turns off SSL certificate checking. So you can stick any certificate in there for easy man in the middle. So, why did you implement SSL in the first place? You just turned it off, basically.
A lot of these devices when you think about it, spouse is traveling for work or something. They’re probably using them in hotels, which are shared networks a lot of times. So I don’t know if anybody here’s ever done sniffing on wireless networks, but it’s amazing what other people will be doing. It’s amazing how many people watch porn in airports.
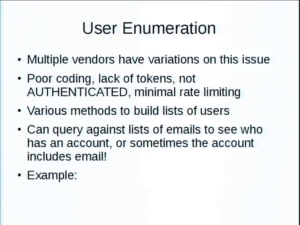
User enumeration. I found variations of this where you could basically find out if a certain email address has an account there, for whatever purpose. So with Lovense, you could basically do a simple query and it would just come back with true or false. No authentication, no tokens required, no nothing. Anyone anywhere in the Internet could just do a GET request and it comes back with true or false.

So, took my personal address book with about 275 addresses and ran that through, just proof of concept. I have some friends with some surprising interests I didn’t know. But this shows you can find out things about people that maybe they don’t want to share. One of them was a friend a friend Bluetooth research and had some of the Lovense devices. Didn’t know about my projects, so it was really funny to email him and say, “Dude, why do you have these?” And he’s like holy shit, that I was able to find this.
I ramped it up with the Ashley Madison dump. Dumped all the government addresses I could find. Queried about 10,000. They’ve already had enough damage to their lives. I’m not going to disclose anything. But there was a handful of trues from very interesting places.

OhMiBod. The app has a search function for finding potential partners. Some of them, if you have a privacy bit set for public, you could do a partial username search and you come up in the list. If you had the privacy bit set to private, you had to know the entire username, and that’s the only way you can connect.
But in the GUI it limited you to I believe three characters is the minimum. But only through the GUI. If you did the query directly, single characters. Which means A through Z, 0 through 9, you now have all the public.
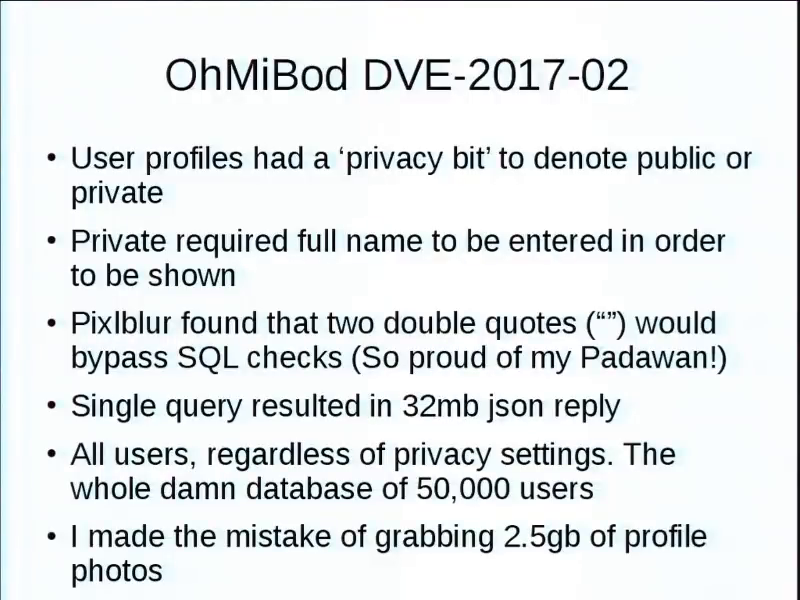
Lots of interesting information there, but it got worse, because my padawan (a student I’m mentoring) figured out that you just put a couple double quotes in that and you click and it’s like oh, this is taking a while. Because there’s a 32M JSON reply of everything, private or not. Like, the whole bloody database. Like 50,000 users, here’s everything. Of course that also included the URL for all the profile photos, and I made the mistake of downloading all of them. I have now got more dick pics than I know what to do with.
Some apps are more social. They have ways to find new “friends.” Sometimes a server provides more info. Like you post a vibration pattern, and do so anonymously. But in the return from the server, it still includes the user’s email address. So…you’re not helping.
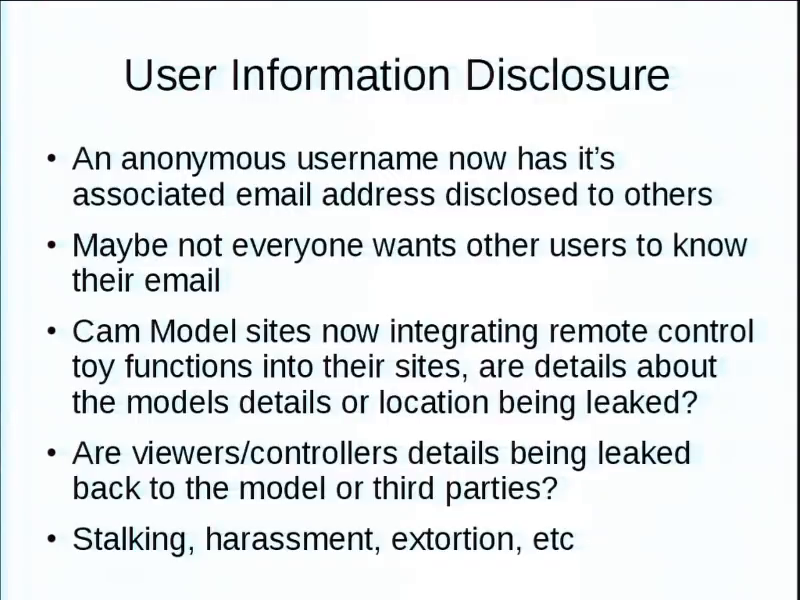
An anonymous username now has its associated email disclosed to others for whatever sort of spam or hijacking purposes. But think about this. Things like cam model sites. The potential for stalking and harassment, if information is disclosed of their location or their private details. That’s scary, right.
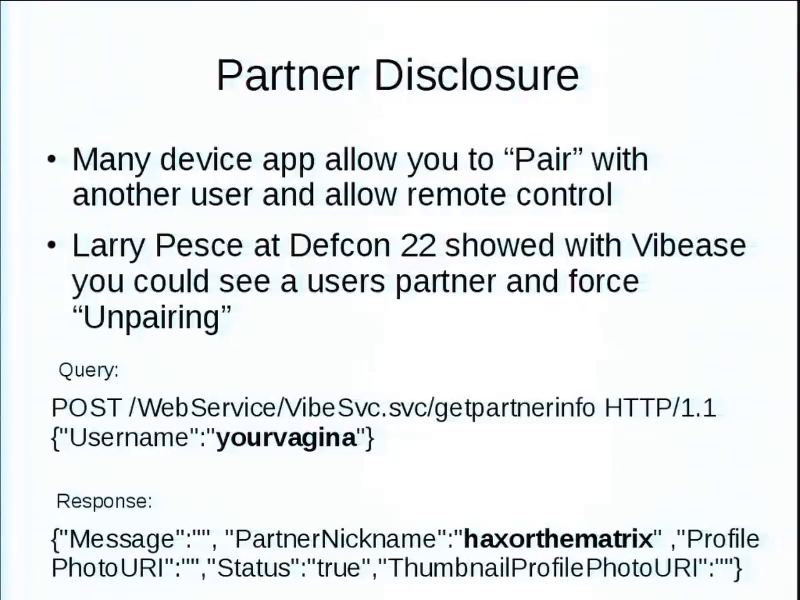
Partner disclosure. Larry Pesce at Defcon 22 showed this one. Didn’t report it at the time, the bastard, but it has been reported and fixed now, where he was basically able to query for username “yourvagina,” and it would respond with your partner’s nickname “haxorthematrix.” Yeah. So you could tell and build social graphs of who was connected to who. Because you could connect to multiple people over time and it would still report over time.
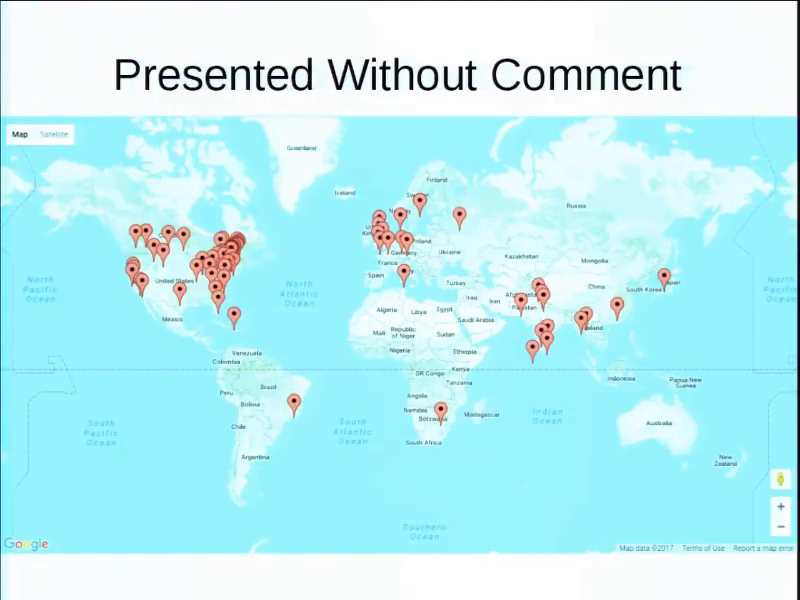
I’ll let you figure out what that’s about.
Embedded API keys. They’re always fun. I have one that has left their admin MailChimp API key in the app, unobfuscated. Full access to their marketing email lists, user subscriber lists and everything, so you can query all that. And send mail as them if you really wanted to. They’re not replying to my emails. I may have to send an email to them, from themselves, or just drop a 0‑day, you know.
So, it’s all for a good reason. Some of this is funny but there are serious concerns. Security and privacy should be in all IoT, especially these devices. As you’ve seen, this is just a quick few examples—there’s a lot more where they’re not. This industry literally does not know what they don’t know. They have been hardware manufacturers of manually-operated devices until very recently. They don’t have people like us around to say, “Hey, that’s not a good idea.” They just are never interacting with us. So I’m trying to build some bridges to wake them up to reality. And when you hand them their 50,000 user database on a silver platter you have their undivided attention.

Yes, this means I have a bag full of sex toys I travel with. But you know, for me this is a serious issue. And you know, the difference between screwing around and science is writing it down.

Basically, several of the vendors that I’ve helped have actually approached me, wanting to start some sort of trade group or consortium or something like that to adopt a voluntary privacy and security set of standards that they would adhere to through like a third-party auditors or some sort of transparency report to basically say, “Hey, we take security seriously. Here’s how we take it Seriously.” You know, full disclosures and having vulnerability disclosure programs. It makes consumers aware yes there are risks, yes we are dealing with them. It’s not just ignoring them or anything like that.
Still trying to figure that out. I don’t know if it’s going to be a seal of approval on the box, you you know, you’re going to see my face on there going [enthusiastically makes “thumbs up” gesture], “It’s secure!” No. Still a ways off. Still trying to figure out how I’m going to do it because I have no idea what I’m doing with this project. It’s a new area for me.

There’s other things like Google Play and the Apple App Store, they will ban “adult” apps for random reasons. Well then that means you break the update cycle. So yes, the manufacturer may fix an issue, but it’s not going to get pushed out. So people have to sideload apps and stuff like that so you’re making them turn off security. Like that’s…dumb.
Data collection from users in places where sex toys are illegal. I believe in one of southern states it is still— I believe…Texas, it is illegal to own more than six sex toys. So I won’t be going to Texas anytime soon. But you can see how data harvesting might be an issue.
Physical harm, as we found out with Samsung. You know, lithium ion batteries burst into flames. Considering where these things are generally put, that would make your day suck.
And I’m waiting for things like the first divorce case to cite oh you know, the guy’s remote vibrator app was connected to a secretary’s device not his wife’s. That sort of thing.

Anyways. I hope that I convinced you that there are some serious issues here. Because they’re not regulated like medical devices, there are no standards or anything like that. So as the public, we have to hold them to a set of standards.
Get over the discomfort. The exact same chipsets that’re in so many fridges and children’s toys and everything like that, it’s…just different packaging. We need your help to educate people and say, “Hey, guys. Let’s raise the bar.”
So, if you’re interested in this I will be around and trying to organize a hackadong. Probably at the IoT Village to…you know, people can starting apart apps and give you some help there. If you’re good at policy writing and stuff like, I could really use some help for the voluntary framework.
Buy me a beer so that I can wipe away some of the memories of things I’ve seen. And we also have a Patreon to just offset the few op costs we have for server time and that. So, alright. Cool. Thank you.