Lisa Rein: Next we’ve got Garrett Robinson from SecureDrop. We’ve been lucky enough that he comes back every year to give us and update on the incredible things that every year— it just seems to be more and more amazing, and so here he is again to tell us about another big year for SecureDrop.
Garrett Robinson: First of all I wanted to say I’m incredibly honored to be here, now and for the past two years.
My name is Garrett Robinson and I am the lead developer of SecureDrop, and I have been for the past two years, so this is an update on where we’re at after working on it for two years.
My first slide was going to be a quick introduction about the history of the project and how it evolved from DeadDrop, created by Aaron Swartz, but Lisa’s film completely stole my thunder and I can’t say anything about it now. While I was sitting there frantically thinking of what to say instead, one thought did occur to me. The thing about SecureDrop and the rest of the talk I’m about to give is that it’s changed a lot in the past two years. But what I realized was that the core design, the core architecture, is almost completely unchanged from what Aaron created and called DeadDrop over 2 years ago today.
I think that’s a really incredible testament to how brilliant he was as a technologist, that his ideas were so crystal clear and so powerful and still form a really useful basis for an important tool. When you work on open-source projects, it’s a way to really get to know somebody deeply, intellectually. You’re working closely on code, technical ideas, discussing things, trade-offs, etc. I unfortunately never knew Aaron personally, but I do feel incredibly grateful to have had the opportunity to in a way get to know him by working on his project.
So two years ago we only had one installation. Kevin Poulsen at The New Yorker installed DeadDrop, then called— it was the Strongbox instance. There were 375 commits and there were 20 contributors, many of whom are sitting in the audience today. Thanks you guys. You guys are awesome.
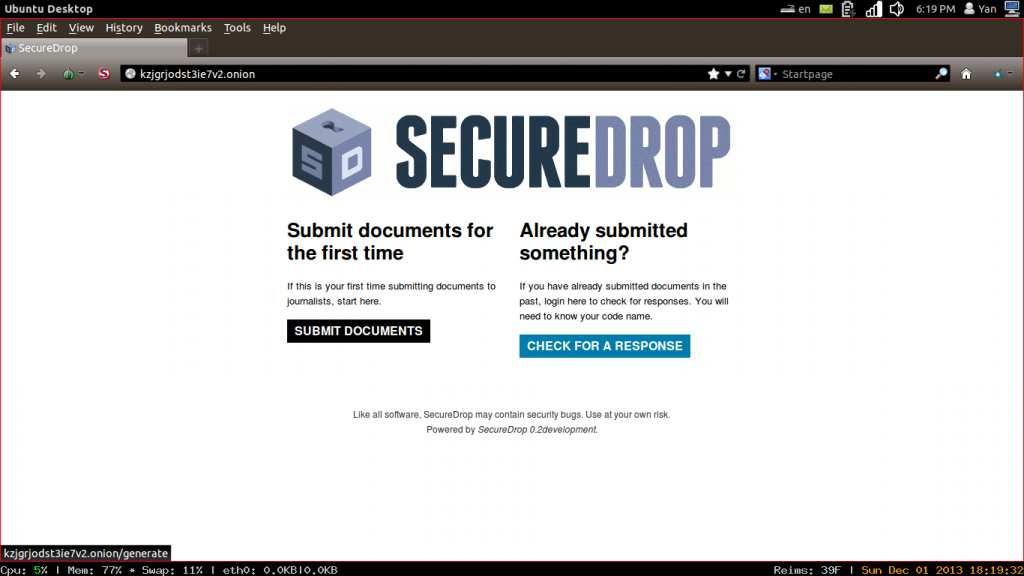
Image: Wikipedia
It looked kinda like this. It’s a web site, clearly, but beyond that kinda 90s. A bit stuck in the past. So now, today, two years later, what do we have? We have over twenty organizations that use SecureDrop. We have everybody from…The New Yorker still runs it, The Intercept, The Washington Post, The Guardian. To smaller organizations, NRKbeta, BayLeaks here in the Bay Area, a local organization doing awesome investigative work. They just published some pretty cool stories based on SecureDrop very recently.
And there are actually even more than are on this list, but people just have begun in the past year or so emailing us at Freedom of the Press and saying, “Hey, we made a SecureDrop. It’s over here in Austria. It’s over here…all over the world.” These are just the ones that we were involved in setting up. There’s actually more. We don’t really know how many there are, but at least twenty, which I think is one of the great things about it being an open-source project. Anybody can set one up if they think that they want to.
And more coming soon. Cryptome, the venerable leaking organization and raw document source, treasure trove, is setting one up. It’ll be announced very soon. And we were just in New York recently. We set up two more instances that’ll also be coming soon. We now have over 3,000 commits, so a hundred times the number of commits we had before, which is awesome. This has been the steady work we’ve been doing on the project for the past two years. And we now have 63 contributors, which is awesome. Thanks again everyone who’s here, everyone who may be listening. We could not do it without you.
And this is what it looks like now. It a lot prettier. Again, this was all contributors. I am awful at design. I’m a software engineers, so it kinda has to be that way, I think. But some people came through at one of our hackathons and made it look really beautiful and it’s a lot more usable now, so it makes me really proud to work on it now that it looks so great.
We recently totally did our documentation over. It’s way more readable, it’s searchable, and people have been saying already that it’s way better to install SecureDrop and use SecureDrop with the new documentation.
One of our really big, kind of enduring policies is that we audit SecureDrop. So we hire outside security firms to inspect our code, find problems, report them to us, we fix them and publish the results. It’s an unusual process, especially for an open-source project, but it’s becoming more popular as security becomes more and more important for everything that we use on computers.
On our first audit, this was the conclusion:
We attempted to deploy a version of DeadDrop on our internal network by closely following the provided instructions. After approximately 30 person hours, we concluded that the combination of incorrect directions, errors in provided scripts, and complicated design make it unreasonable for regular system administrators to set up DeadDrop correctly.
That was a bummer.
So this year we did our fourth audit, and this is a lot of text, so I’m going to highlight two parts that I think are really worth noting.
SecureDrop’s extensive hardening places it well above industry standards due to its emphasis on security and privacy. Overall, the newly introduced components do not add to the already limited attack surface, as the SecureDrop architecture remains the same. The addition of a Grsecurity-enabled kernel significantly raises the bar for attackers who manage to successfully exploit the application server via various memory corruption style attacks. Additionally, all interfaces except the one used by sources are only available over authenticated Tor hidden services. These factors, combined with SecureDrop’s existing defense in depth measures, make traditional forms of server compromise significantly difficult.
One is that “SecureDrop’s extensive hardening places it well above industry standards due to its emphasis on security and privacy.” All these various things that we’ve been doing this year, we’ve got a hardened kernel on every SecureDrop now, a ton of additional hardening, more testing, more auditing. These things combine to make it really hard to hack, which is the whole point.
We have a new web site. Our awesome sysadmin Kevin Gallagher and Crystal Lee worked together to create a brand new SecureDrop web site. It explains how it works, and people who want to set it up can go here and learn how to do that. It’s really nice; check it out.

This actually happened a little over a year ago, but I wanted to say it again because it was so awesome. You guys might’ve heard of that guy and you might’ve seen this movie. It’s a great movie. We were really excited because we were included, along with a number of other really great projects, in the end credits as a project that according to the director were essential for the making of the film. So that was a really special honor. (These other guys, the Tor Project, I don’t know who they are. Weird.)
We’ve been working on some other stuff that we’re going to be talking about more in the future. I think this is just one example of stuff that we’ll hopefully talk more about soon.
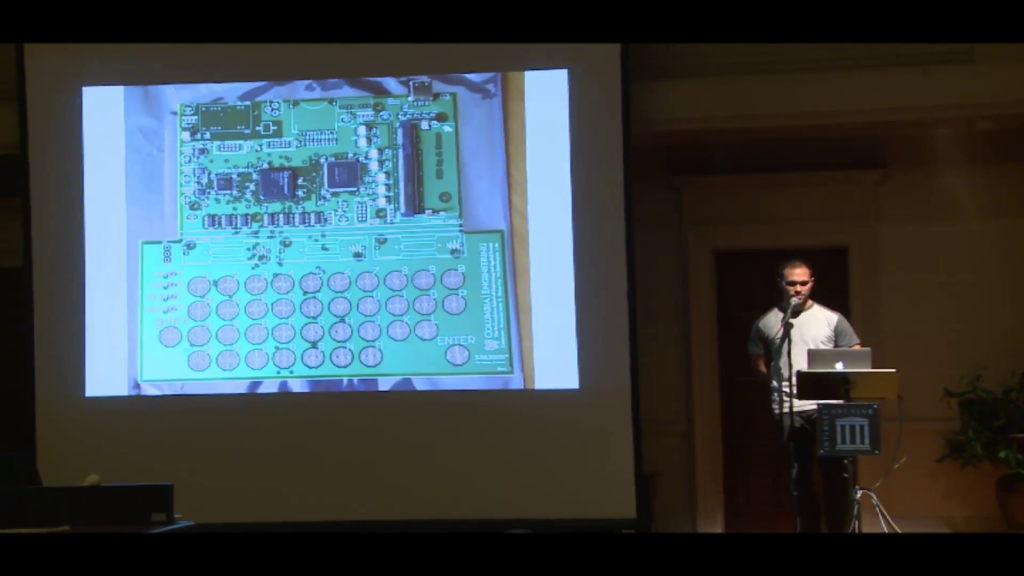
We’re working with a group of professors and students at Columbia University on some custom hardware for SecureDrop to make it even more secure. I don’t want to go into this at length because you’ll all fall asleep, but this is a prototype board that we just took a look at and saw a demo of last week. We’re hoping to talk more about it, and it will hopefully make a really huge difference in the security of the system for everybody who uses it. So it’s kind of awesome.
One question that we get a lot about SecureDrop is “Does it work?” Obviously we can’t really talk about it in detail. It’s really important that we maintain the security of what we know about it, and we personally try to learn as little as possible. But I can say that it is being used, you have probably read news stories that were sourced from it, and Columbia University’s journalism school is writing a report on it right now which will probably come out next year that is based on interviews with people who use it in the field, and it will hopefully explain a bit more about how it’s useful, how it impacts journalism, and we hope we can point to it and say, “See?” but until then we have to be kind of quiet about it. Hush hush.
Really quick, I wanted to say that the parent organization that maintains SecureDrop is the Freedom of the Press Foundation, and we’ve been growing. We currently have a total of six employees, which is twice the size we were last year. We’ve hired some really awesome people. We’ve hired Harlo Holmes, who is a digital security trainer. She is awesome, and that’s a really cool picture of her. We’ve hired this guy, his name is Conor. He’s really cool, too, awesome developer working with us. He’s over here. And just two weeks ago, we hired another software engineer for SecureDrop. His name’s Noah. He’s also here. So I hope with all these new really talented people we can continue to do more exciting work with SecureDrop.

Image: aaronswartzday.org
Finally, I wanted to say that this is not a picture of a lumberjack and the guitarist from U2, although it looks like that, I know. That guy is me (hard to believe) but the guy on the left is James Dolan, who was one of the original architects of SecureDrop along with Aaron and Kevin Poulsen. James left the project only known picture of him in existence. He’s kinda like Bigfoot. He wouldn’t want me to say this, but he has had an incredible influence on the project. It wouldn’t be what it is without him, and I just wanted to thank him for everything he’s done.
That being said, there is a lot more to do. Everyone who was at the hackathon knows we have a lot of work to do to keep making this project more secure, easier to use, and more impactful. So get involved, and thanks.
