Kaliya Young: It’s great to be with you this morning. So I thought I’d start at the beginning. I founded the Internet Identity Workshop with some colleagues in 2005, and we are still convening. We began meeting really asking this question, how can individuals own their own digital identifiers? How can we get out from being underneath the platforms that we’re interacting with? Just a username and password, or now more recently you have these intermediaries like Google and Facebook, that you’re using to log into various things.
And then, if you got yourself your own identifiers how do you actually prove meaningful things about yourself using them? And the good news is after fifteen years of convening, we’ve gotten somewhere. Our next one’s actually happening next week, and you’re all invited of course.
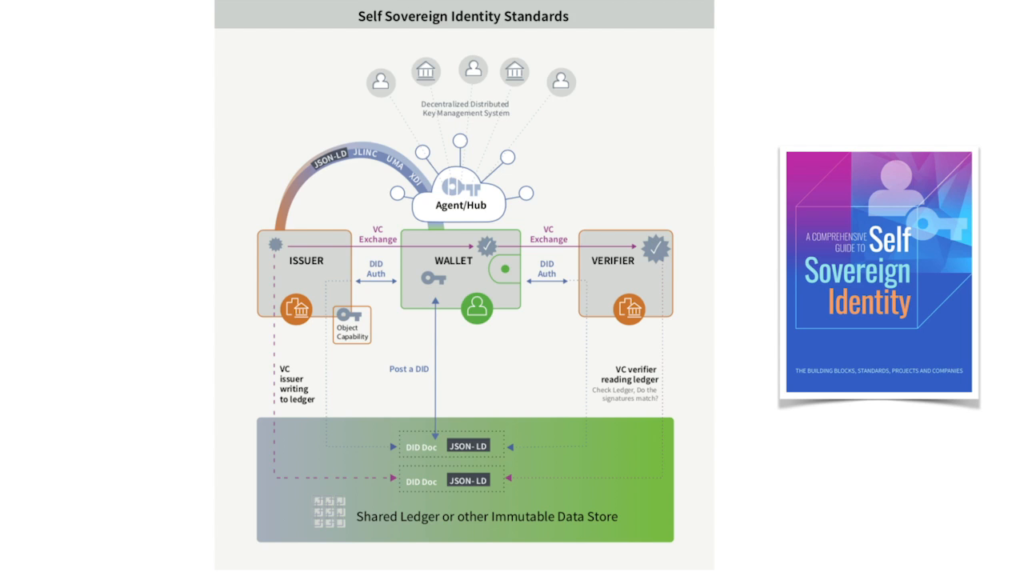
There’s a whole set of open standards around self-sovereign identity that have emerged. And I’m gonna touch on them really briefly.
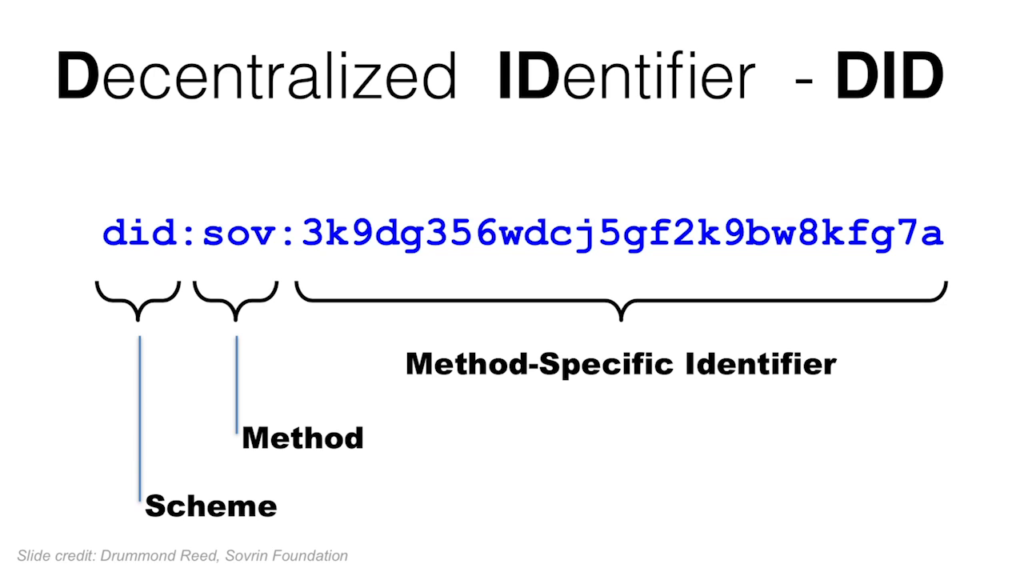
At the core of them is this, the decentralized identifier. And it’s an identifier that individuals themselves create, along with a public key and a private key, and they can post them to ledgers. And there’s lots you can read online about the technical details and I’m not gonna go into them now. There’s not enough time. But I invite you to explore them.
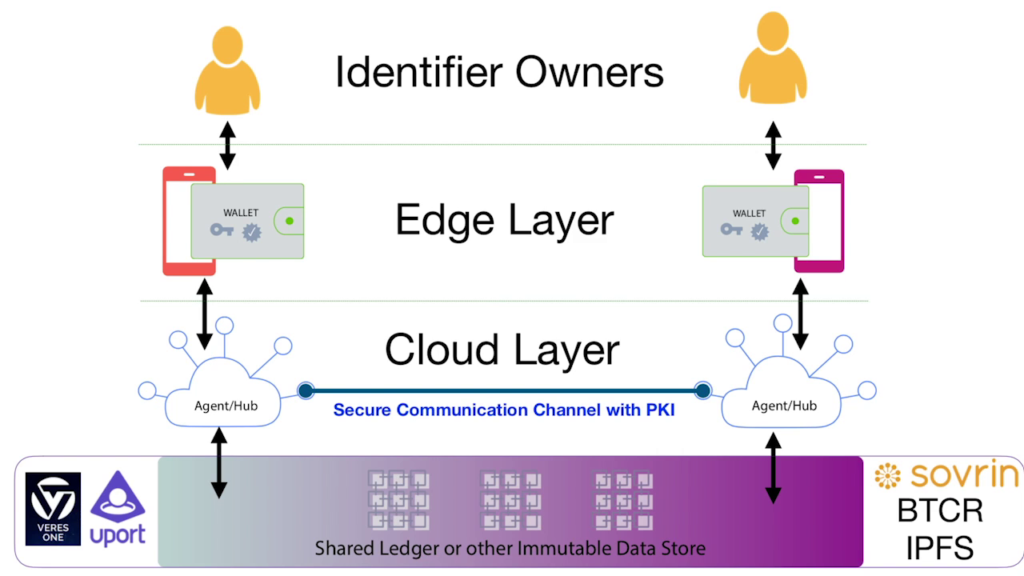
And conceptually at the top you have identifier owners. Then you have the next layer. You have individuals have digital tools that work on their behalf. So at the core of this is a wallet that they would probably carry on a smartphone.
And then next you have what is happening in the cloud, so that individuals will have agents that are cloud-based that are connected to their wallet. And these are also under their control. And the vision for these is that they act much more like a bank does today. We go and we put our money in a bank, and the bank helps us do things with our money. But it’s our money; we go back to the bank and go, “I want my money, I’m going to take it to the other bank.” The same should be true with our data. It shouldn’t break down if we choose to change service providers and those that are acting on our behalf with it.
And then next you have, as has been mentioned, shared ledger, distributed ledger technology, of which there are quite a few different folks (Sovrin is the one that’s been named here) already that are supporting this. And it’s really a routing infrastructure. There isn’t very much information stored on these in the distributed ledger. It’s really a way to go find and connect between agent to agent for individuals, and to connect using public key infrastructure.
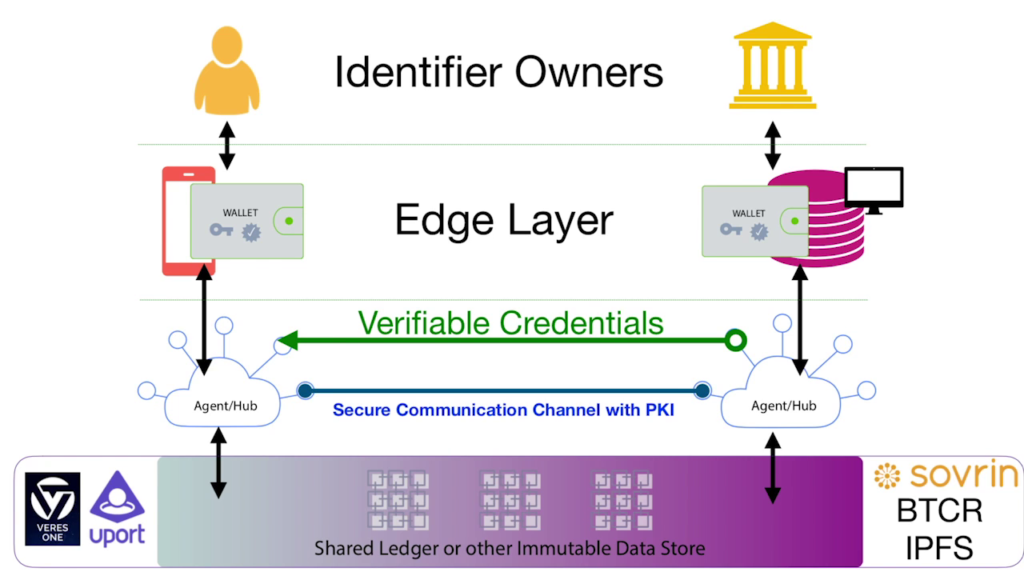
And the other thing that you can do with this is verifiable credentials to support the movement of attestations, credentials, claims—however you want to call it—from institutions to individuals.
So where do these verifiable credentials come from? And one source is registries. And this is what I’m really grateful for Mike’s work, is kind of to go oh right, okay, that’s one way to look at them. And I spent the last two years at UT Austin in their new Masters of Science and Identity Management program. And I’ll tell you a little bit of the story and then I’ll walk through what we have.
In that program, we were in a cohort of twelve folks. And we would get new teachers, right. This happens in a cohort program. And we kept talking about identity as if it was one really big thing. And I was like wait a second. There’s different forms of identity, in different places, and we need to have a framework to think clearly about it.
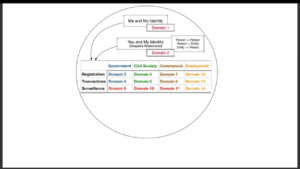
And so this is actually part of Mike’s paper. So what are the different places that PII, personally-identifiable information, ends up in databases? And this is the anchor for how I thought about dividing up the world of identity into some manageable chunks.
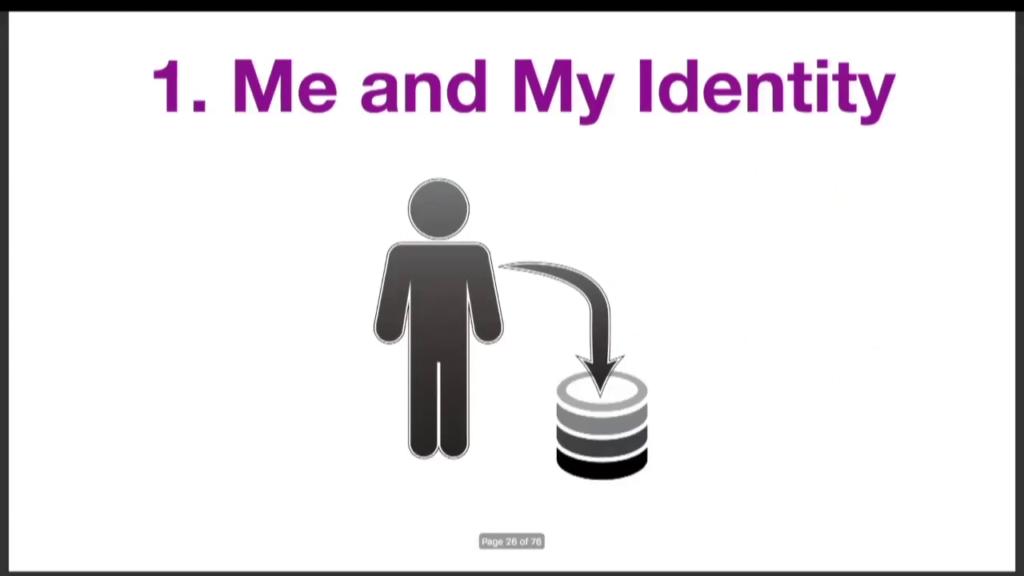
And so at the top of this is me and my identity. And this is the place where I as the individual collect and manage and store my own information. And we have several varieties. User-centric digital identity, this is what the folks I’ve been supporting, convening at the IIW, have been working on for a long time. There’s the Indie Web efforts. Folks have been working on these challenges in that context. You have the quantified self movement, which is all these tracking and all sorts of tools for people to manage and track their own information. And now this new kid on the identity block, the self-sovereign identity work. So this is me and my identity.

Next is a category that often gets overlooked, but how do elders, children, folks with disabilities, and others manage their identity? They do it with folks acting on their behalf. So you have “you and my identity,” or delegated relationships that we need to have accountability in the systems to support folks who aren’t managing their own identities having others do it on their behalf, but in a way that means they’re not giving away their credentials—that there’s accountability.
So, these are the sources for data and identity information in the next twelve domains. And we’re gonna step through them.

So the first one is government registration. And there’s two forms, really. There’s primary registration, which is done by parents on behalf of their children. This is when you register your child’s birth at the county level, and now more recently also with the federal government to get the issuance of a Social Security Number. And then also secondary registration is all the registrations you do after that, often yourself, using those primary documents to get a driver’s license, to get a passport. All kinds of different things need you to get another identity issued to you by various governments.
And all of these systems and processes are very recent inventions. Most of them are less than a hundred years old. And there’s a loop that happens, actually, where modern states came into being in part because they went out and registered their citizens, who then thought to themselves, “I’m part of this thing called a state.” So this actually forms a recursive loop in terms of people’s sense of identity when these processes are put in place.
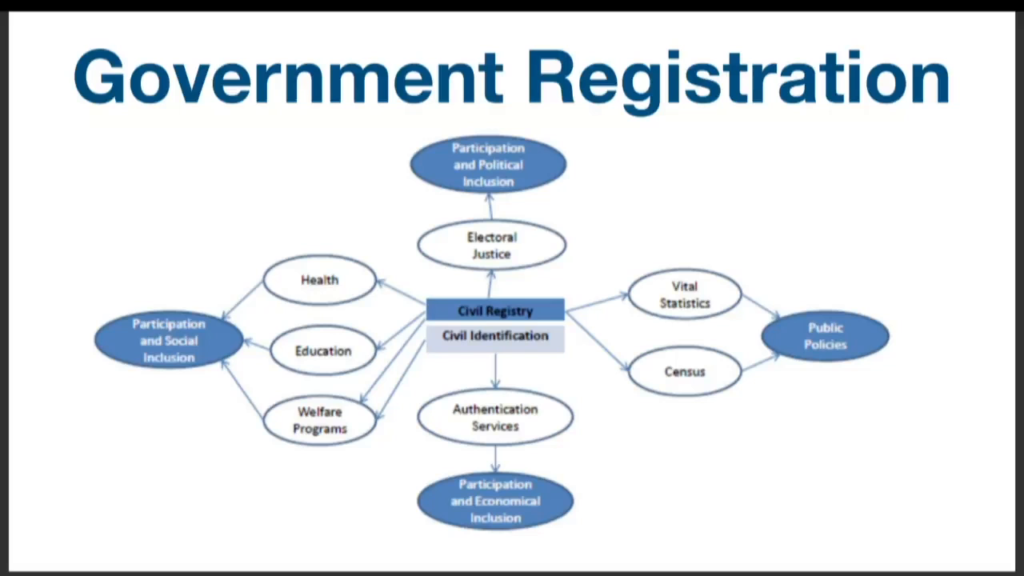
And this is a map from Mia Harbitz, whose work is in the CRVS space (civil registration of vital statistics) about what happens when you have effective civil registration in terms of enabling a holistic picture of its impact on society.
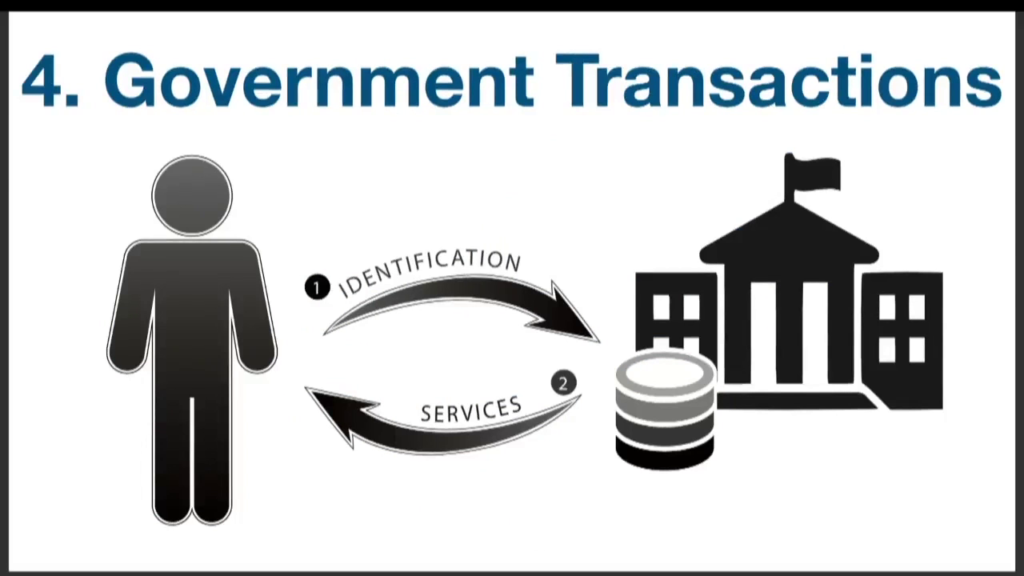
Next you have government transactions, and this is where you show up with the documents you had in step one, which is getting registered, and you go and use them to do things, actually. And this is actually where you find a bunch of registries. You can’t register your car unless you have a driver’s license in which to make the connection, right. And when you do land transactions that are recorded by the government, they ask you to present government-issued ID.

Next we have civil society. This is a whole cluster of organizations that come together for the purposes of this, which is organizations which you have an ongoing relationship, and that are providing not just commercial transactions but health, education, many other things. And all of these institutions have a registration process and some sort of issuance of credentials that you re-present when you show up to ask for the services.
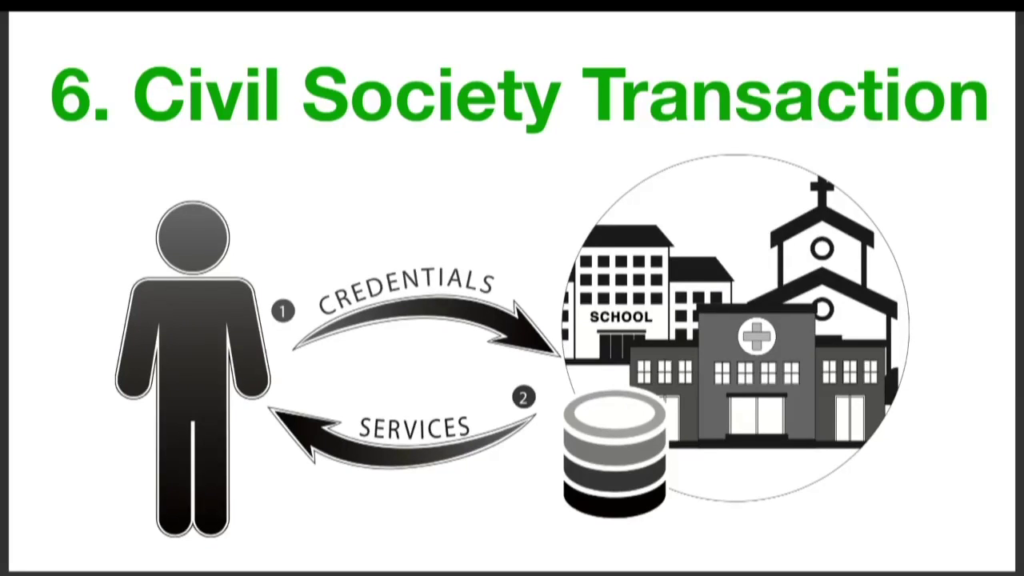
And you present the credentials you got through the registration process, and you’re able to transact to get the services. And this is also a place where we find, ta da, a registry. Professional licensing often happens in these types of institutions, right. This is another registry.
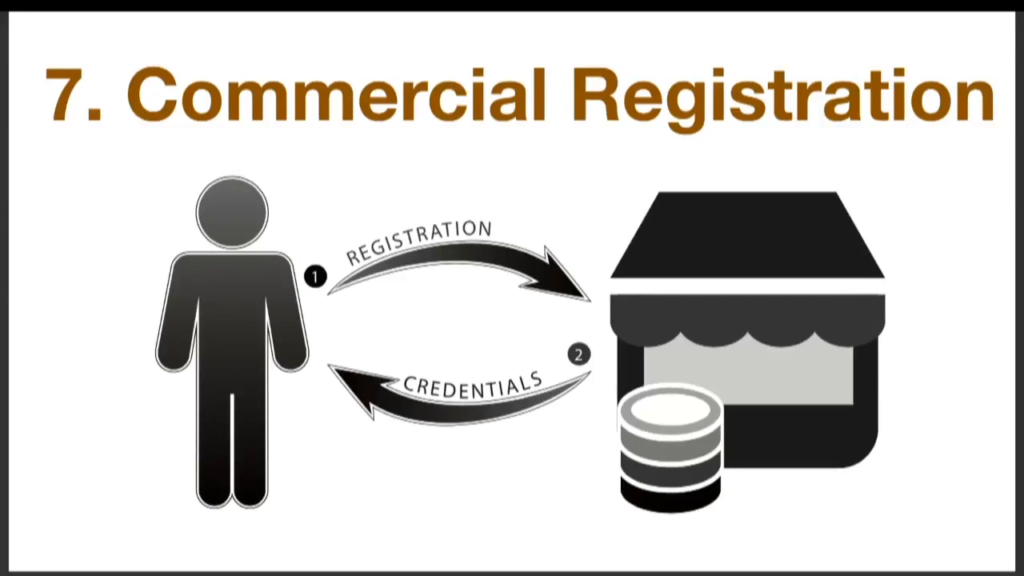
You have commercial registration. This is where you sign up to get that loyalty points or a customer number with a service provider.

And then when you present, you show up, you share whatever it was you got in the registration process along with payment and you get your goods and services.
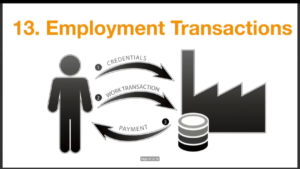
Next you have employment registration. This is where individuals are applying for jobs, sharing information about who they are. Once they’re offered a job and it’s accepted they’re enrolled into the enterprise systems, and they get a credential and they present that credential to do work. And in return they’re paid for that work.
So, this next category is where we end up with PII in databases and surveillance. And in my research there were three main kinds: voluntary known, involuntary known, and involuntary unknown. And this happens across all of the contexts that I’ve already gone through. So you have government surveillance happening, of all three types. You have civil society surveillance—so this is like CCTV cameras going into school or you know, various ways that people are being tracked. And a lot of it’s voluntary. Like I put on some sort of health monitor and it’s going back to my doctor, I understand that’s happening and I’m choosing it.
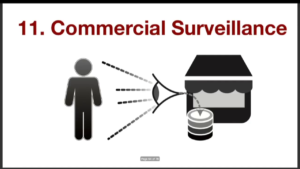
And then you have commercial surveillance. And finally, employment surveillance. So this is where…this is really old. Taylorism is not new.
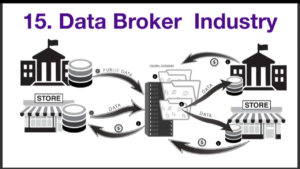
So those are the next twelve domains. And then finally you have the data broker industry that’s pulling data from all of the above contexts—public data, data from commercial entities, compiling it into digital dossiers and reselling it to government and the commercial sector.

And then finally all of these domains are subject to attacks on the black market both by state actors and criminals. And this data is being spread around in that way. So there you have the domains of identity.
Now, I want to quickly tie it all back together and be like, how do we actually— If you notice in all these little diagrams there’s the person. And what if we put the person at the center? Going back to SSI, using their wallet and their cloud agent, that they could collect the credentials that they get from government and then reuse them when they show up on the door of government to do transactions.
They can collect credentials from their civil society institutional engagement, their professional licenses, their number from the water polo association—all kinds of credentials in digital form. And when they use them it’s really easy for them. Their employment registration credentials, proof of where they’re employed, and use those in a much more secure way to even log into those systems of the enterprise. And then, commercial registration, all their loyalty cards, and points, etc. And use them.
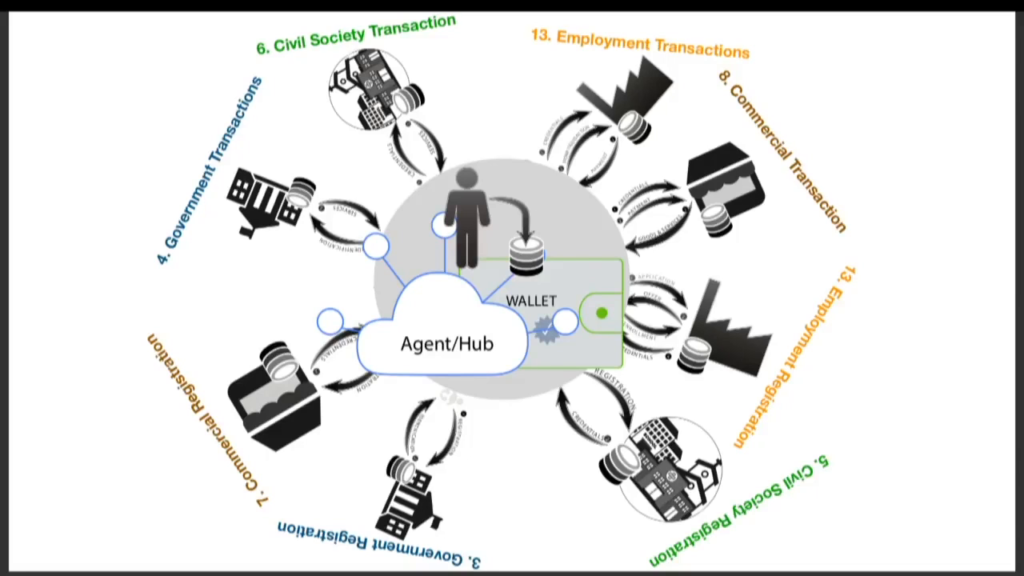
So, self-sovereign identity is what sits in the middle enabling individuals to manage all these different relationships in a way that is significantly less complex than each of those institutions needing to have a business relationship with each other to see those credentials.

So, we are really seeing the emergence of a new layer of the Internet for people, I believe. Layer 8, on top of the one we have right now. And I want to close with this quote, Protocol is a language that regulates flow, directs netspace, codes relationships, and connects life forms. It is etiquette for autonomous agents.
And these are also the new set of protocols to really enable us as people to connect to one another and connect to organizations.
And I’ll leave you with this. To get to this future we need to coordinate the development of common building blocks, code, infrastructure, and protocols. We must ship interoperable products, and we need to work towards alignment and control. So with that I thank you, and look forward to the panel.