As we’ve moved into increasingly digital spaces, so online worlds, we’re moving away from your traditional physical spaces where you have public streets; where you have public squares; where people can go to protest, and into areas, if you would call them that, that are entirely controlled by corporations.
Archive (Page 2 of 5)

One of the things I really want out of art, what I see the job of the artist to be is to try to learn how to see the historical moment that you find yourself living in. I mean that very simply and I mean it very literally. How do you see the world around you?
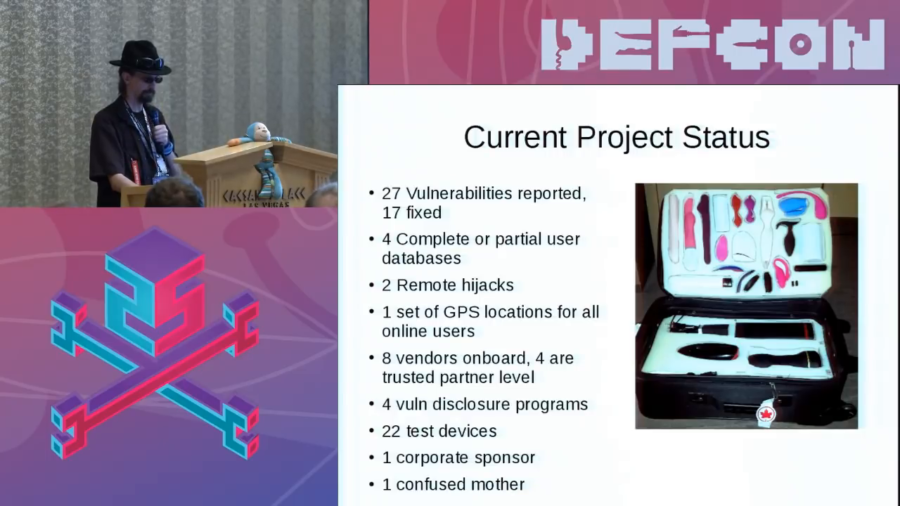
A large number of IoT research firms…yeah, they don’t want to look at this. Because there are stigmas around sex. We have a very weird thing in North America about sex. We’ll watch all the violence we want on television but you can’t see two people have sex.

The big concerns that I have about artificial intelligence are really not about the Singularity, which frankly computer scientists say is…if it’s possible at all it’s hundreds of years away. I’m actually much more interested in the effects that we are seeing of AI now.

We have been documenting and researching into human rights or digital rights violations that are taking place in Palestine and Israel. And one of the most recent case studies or work that we’re looking into is the use of predictive policing by Israel, which is rather a sensitive issue given that there isn’t a lot that we know about the subject.

We have to ask who’s creating this technology and who benefits from it. Who should have the right to collect and use information about our faces and our bodies? What are the mechanisms of control? We have government control on the one hand, capitalism on the other hand, and this murky grey zone between who’s building the technology, who’s capturing, and who’s benefiting from it.



