Niloofar Howe: Good morning and thank you. I think my role here today is take all the hope that you might’ve had after that session away as we head into lunch. So, Niloo Razi Howe, Chief Strategy Officer at RSA. And what I wanted to talk about today is the hacker industrial complex. At RSA we have this incredible fraud team that for the past ten years has basically gone underground and infiltrated a lot of the criminal networks and really tried to study the latest tools, techniques, as well as some very interesting social patterns which are beyond the scope of the talk today.
But I wanted to start by just setting the context here, and why all this matters, and to try and understand some the craziness that’s going on. Everyone in this room really knows what 2016 was all about. It was some of them biggest attacks we’ve had. And from my perspective it was just a window into possibilities for the future. I don’t actually think we understand the full ramifications of what we saw in 2016.

So whether you look at the Mirai botnet, the largest DDoS attack in history which showed that your refrigerator can take down Twitter. You look at Yahoo! and the unending sort of news stories that seem to be coming from that breach. One billion accounts hacked. There’s three billion Internet users, so the impact there is pretty huge.
Of course the DNC hack—you know, a country with the eleventh largest economy the world has repeatedly shown how it can cause us to lose faith in our systems, in our government, in our most fundamental processes, despite the fact that they don’t have the economic power that we do. And despite the fact that every demographic trend is working against them, they’ve been incredibly effective in cyberspace. 1.2 million pieces of malware released every day. And it all has very interesting implications to what we call the hacker industrial complex. Or the Wild Wild West of the Internet
So why is this all happening? It used to be the case that it was pretty hard to break into systems and actually extract valuable information. Rob Joyce, who is the new White House cybersecurity adviser, former head of TAO, gave a talk at the Enigma USENIX Conference in February 2016 where he— On YouTube, you can watch the guy who ran offensive cyber for the NSA talk about how he broke into systems with the hope, by the way, of showing people what they had to do to defend their networks.
And basically it’s a six-step process. Reconnaissance; you learn what systems are being used. You can use scanning tools. You can use email attachments, removal media, etc. You exploit those systems; you find a way in. You figure out how to persist. Install your tools so can move laterally. And all with the goal of collecting, exfiltrating, and exploiting.
Now, this entire attack chain used to actually be pretty hard to deploy successfully. The problem is it really isn’t that hard anymore. Not just because the tools are readily accessible, but what’s happening out there is there’s a crowdsourcing of the attack chain that’s going on. So you only have to know one piece of this attack chain, and you can get together—through social media—with people who are experts in other pieces of the attack chain, and you can actually conduct an entire operation—impossible to have attribution because it’s different groups doing it.
And all of this makes of course our life on the defense side pretty hard. Because their goal of course is to get to know your networks better than you do, which isn’t that hard. The only way you can actually defend you network is to actually know what’s going on.

And it brings me to a couple of ground truths. We have basically lost control over our network. All of the advances that have made our lives more productive, more accessible, more connected, have fundamentally disintermediated our ability to protect our environments. The democratization of information, of technology, of goods and services, of banking, of financial transactions with blockchain etc., means every aspect of our lives has become accessible and therefore vulnerable.
We’ve moved from a world where you had to be invited in and trust was presumed in our networks to a world where trust is presumed not to exist. And when you look at the combination of unmanaged devices, unmanaged digital identities, the sheer number of applications that are being created… And importantly the changing nature of the workforce, which today’s demanding to be able to access any application from any device at any time from anywhere in the world, means that without vigilant dedication to security, knowing our networks let alone protecting them has become very very hard.

Now, even when you have best practices in place, right— (network segmentation, dual-factor authentication) there are some headwinds that those of us who are on the defensive side have to face. First of all it’s asymmetric. An attacker only has to be right once to get into our systems, whereas the defenders have to be right every single time to stop them. The ROI on attack tools is continuous and basically unending. The same tools can be used over and over and over again. And when attribution is difficult, retribution is almost impossible.
Layer on top of that the fact that attackers have increasing access to more and more sophisticated tools—tools that nation-states only had access to a few years ago are in the wild and being used by them. And the fact that we have a global Internet but no global norms of behavior that we’ve all agreed to. Or, frankly, standards as an industry that we’re going to build our products to. You kinda get to the Wild West.
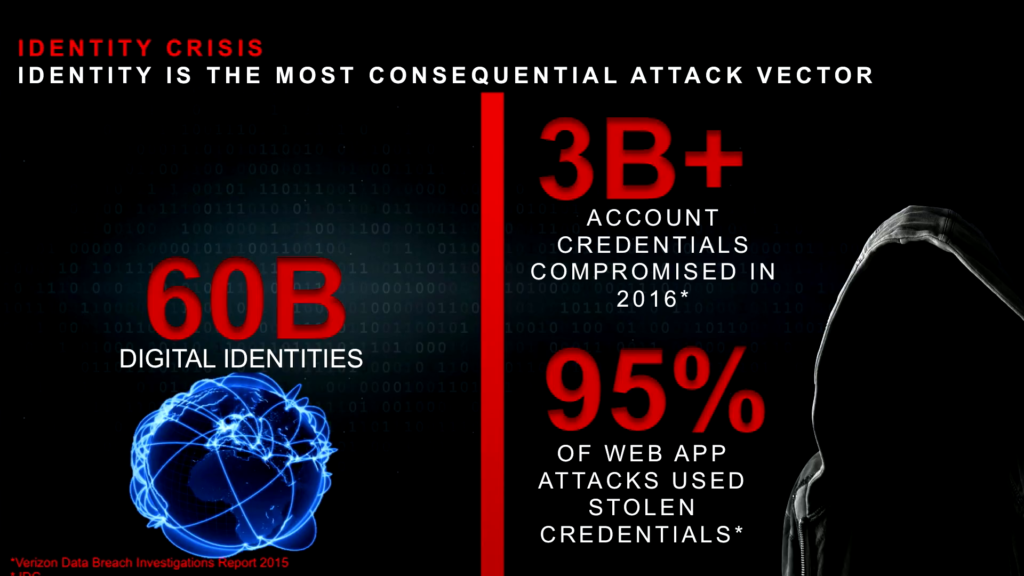
Now, the weakest link in all of this is us. It’s humans. Even with everything else in place, we kinda keep messing it up over and over again. And so there’s kind of an identity crisis going on. You have the world population over 7 billion, 3.2 billion Internet users, 60 billion digital identities. And the reason I say digital identities is because it’s not just human identities, it’s not just you and me. It’s all the applications and devices also have their own identity. So it’s not just the Internet of things we’re talking about, it’s the identity of things that we’re talking about.
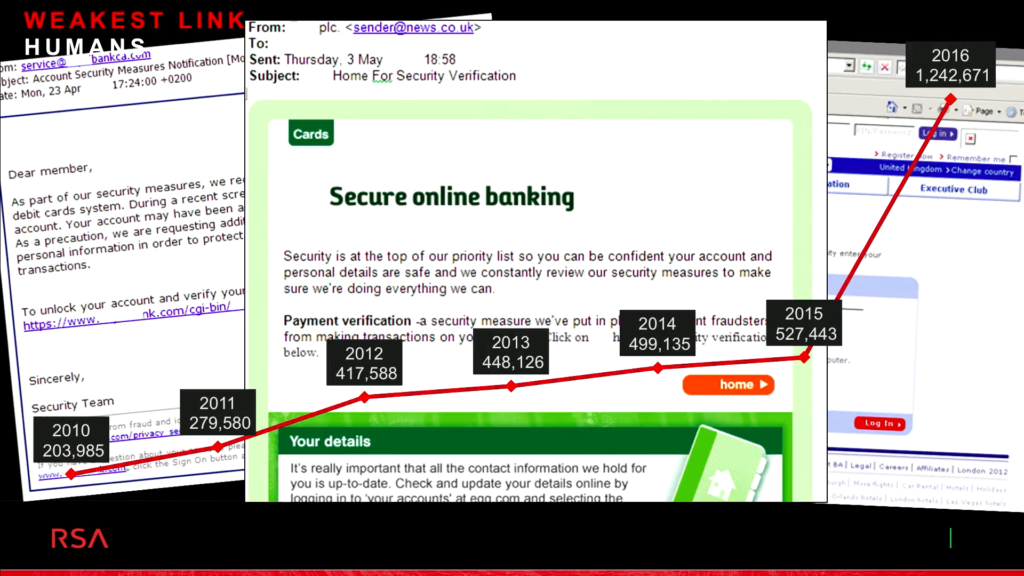
And when you look at the attack vectors and why these identities are so important, web applications attacks, which were the most common form of attack, 95% of them last year used stolen credentials. There were over three billion account credentials that were compromised. And so it’s no surprise that phishing attacks are on the rise. What we saw between 2015 and 2016 was a three-fold increase in phishing attacks, and they continue to be incredibly successful. And the tools that are being used for ransomware and all of that are really starting to become available to the bottom-feeders of the criminal community. By that I mean the least sophisticated folks in there.

So this brings me to basically the third ground truth. Which is criminals no longer need to hide in the dark. What we have seen is an absolute rise in a new industrial complex of hackers actually working in plain sight to conduct all of their criminal activity.
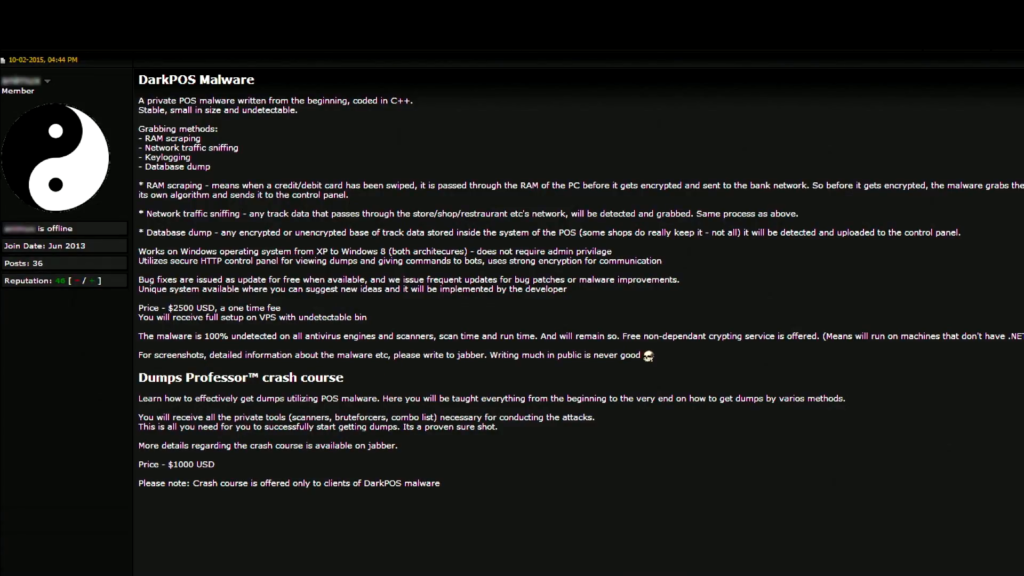
So today, you can buy cybercrime as a service. You want a Point of Service malware tool. You don’t know how to make it, that’s okay. You can go to a website and buy it. And here’s what’s amazing. You don’t just get the malware, you get all of the resources. All of the tools that you need to conduct your attack is available to you through these web sites. By the way, a lot of them also have call centers and service level guarantees.

You want to buy call center services. Pick your language, pick your gender, pick your accent. They’re all available. Credit card troves, and we get to this in a second. But the Internet is littered now with stolen credit card information. And what’s interesting is in some geographies like Brazil, they actually take advertising and trying to differentiate themselves through marketing very seriously. So they’re using movie posters to advertise the services that they sell.
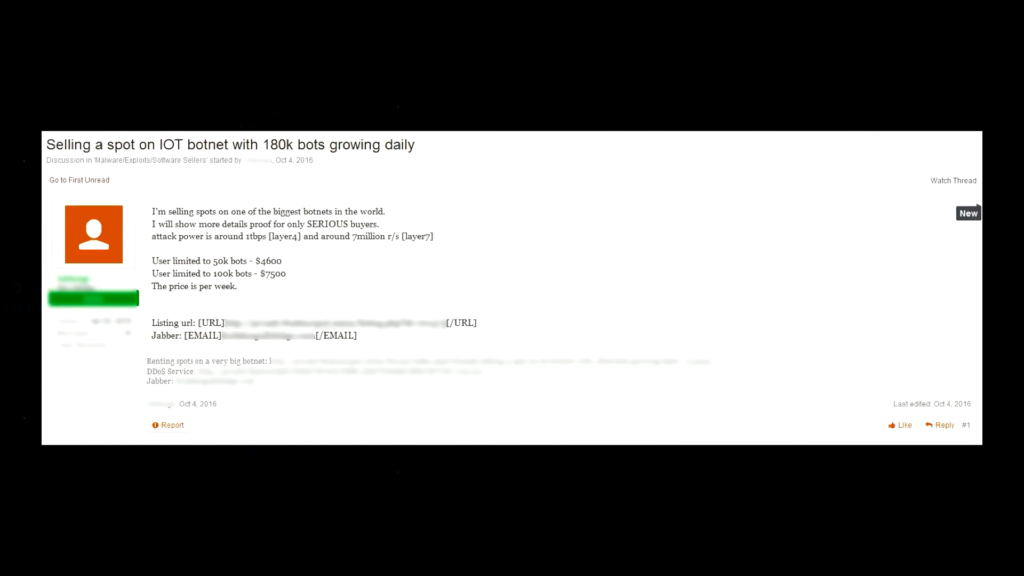
Let’s say you want to launch a DDoS attack but you don’t exactly know how. Totally okay. You can buy a spot on the Mirai botnet. Fifty thousand bots for $4600. That’s about ten cents a bot. Kind of affordable. And they will launch the attack for you.

So what’s really fascinating as we look at what’s going on in this criminal industrial complex is the use of social media as the platform for conducting criminal activity. So, outside of the US, where there [are] still some laws in existence, around the world the need to go into the dark web is becoming less and less required. Because prosecution rates are less than 1%. So the criminals have actually moved to these social media platforms, and I want to show you really quickly what the new dark web looks like.
[The next several paragraphs narrate a demonstration running approximately 10:38—13:48 of the recording, but the text and included screenshots should generally suffice.]
So this is my Facebook page. Let’s just make sure it’s working. This is my son getting a hockey award. That’s my daughter, my son’s putting on her goalie pads. So just showing you this is real.
So let’s say I got fired from RSA and I really really needed to buy a shoes and can’t afford them, so I kinda need someone else’s credit card to do that. So, you guys all know what CVVs are, right? The credit card verification value. It’s what you need in order to use someone else’s credit card. So let’s just run a search on CVVs.
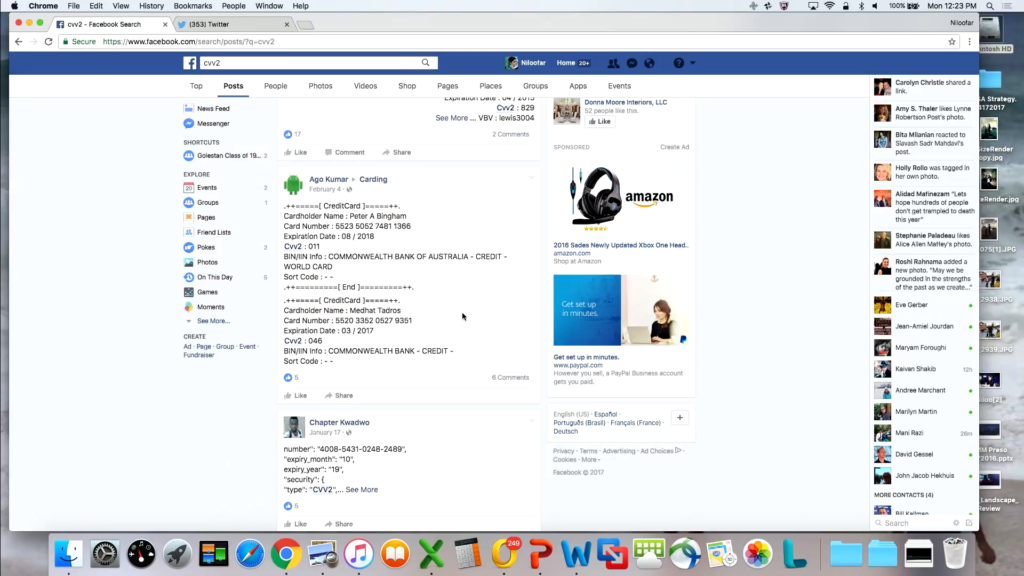
Here we go, first post. There’s the credit card number, and the expiration date is April 2015, I don’t think I can use that one. Let’s keep going. Some advertisements for some places we can go. Let’s look at this one. He’s just advertising his wares. You need to actually contact him. Here’s a good one. Peter Bingham; does anyone know Peter Bingham in Australia? Because his credit card is right there, with the CVV information as well as from the Commonwealth Bank of Australia.
And you can keep going down. Here’s a good one from JPMorgan Chase, Michael Lynch. I even have his address. And a ZIP code and his phone number. All right there for me to use, right on Facebook.
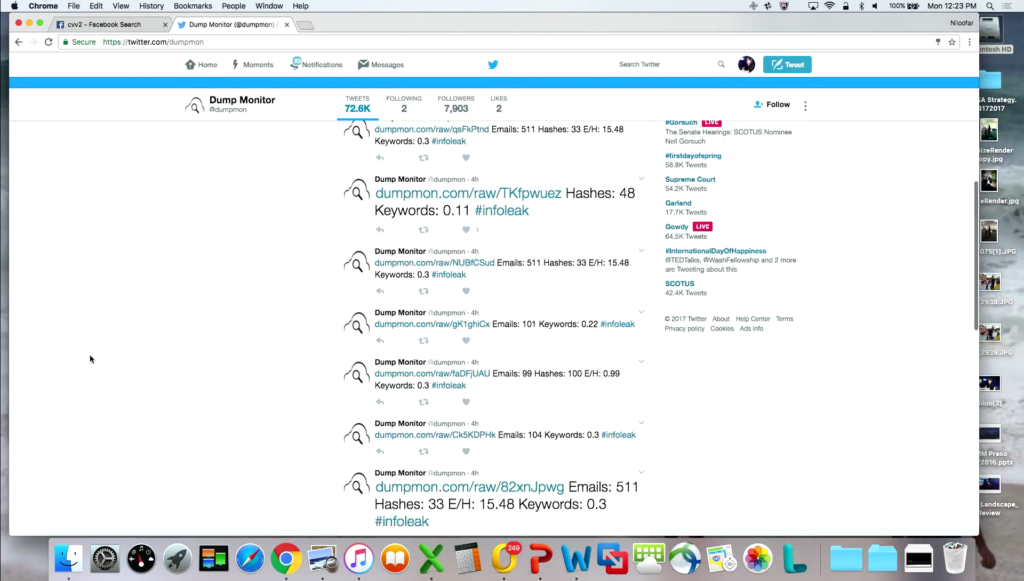
Now let’s go on Twitter for a second. So here’s what’s fun on Twitter. (By the way, before the election when you put in “dump,” really it wasn’t that that came up.) So here’s a Twitter feed that basically scrapes the Internet for all sorts of dumps of personal information.
And here’s what’s really cool. I went on this this morning just to make sure that we could do this fast. They post emails and passwords. This just got got posted early this morning. This is 68 million hacked Dropbox accounts. And they’ve listed the email address as well as the hashed password for you to access. So they’re just giving you a taste of what’s in that trove. If you want to actually access all those accounts they give you the URL to go to. Which is awesome.
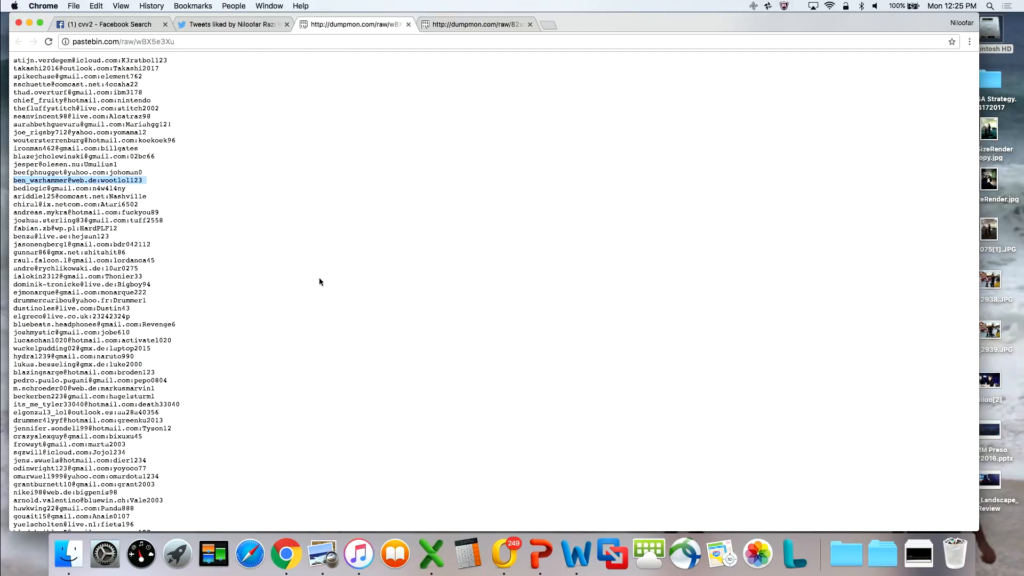
There were a few other places that I liked this morning. So here’s a more common one that you find. This is actually just another dump. But it’s got all the user names and passwords for these emails. So if anyone knows ben_warhammer, for example in Germany, user name and password is up here.
So in less than thirty seconds I can either go find a credit card on Facebook that I can use… By the way, I was looking Facebook last night just to see what was there, and there was a post on exactly how to use—step by step instructions—a stolen credit card on Amazon. How to set up the account, the minimum purchase that would let you not get caught by their fraud team, and what dollar values you should use as you made your purchases with these stolen credit card accounts.
[End of narrated portion.]
Now interestingly, that post got taken down within a few hours of being put up there. And so these social media sites really do try and scrape for content, and the reason I liked a bunch of the feeds on Twitter is because they do get pulled every once in a while. But not before they can because a fair amount of damage.

So again, the whole reason that I wanted to show this to you is it’s all out there. I mean, the amount of information that you can access online is fairly crazy. So as we look at what’s going on out there, over the past six months we have seen a 300% growth rate in the use of social media online. It varies by geography. In China, Baidu and QQ tend to be the most common platforms that are used, for example. They’re actually really good about scraping criminal activity off of those platforms. But the criminals have figured out how to use evasive techniques, use characters that don’t get caught within those systems.
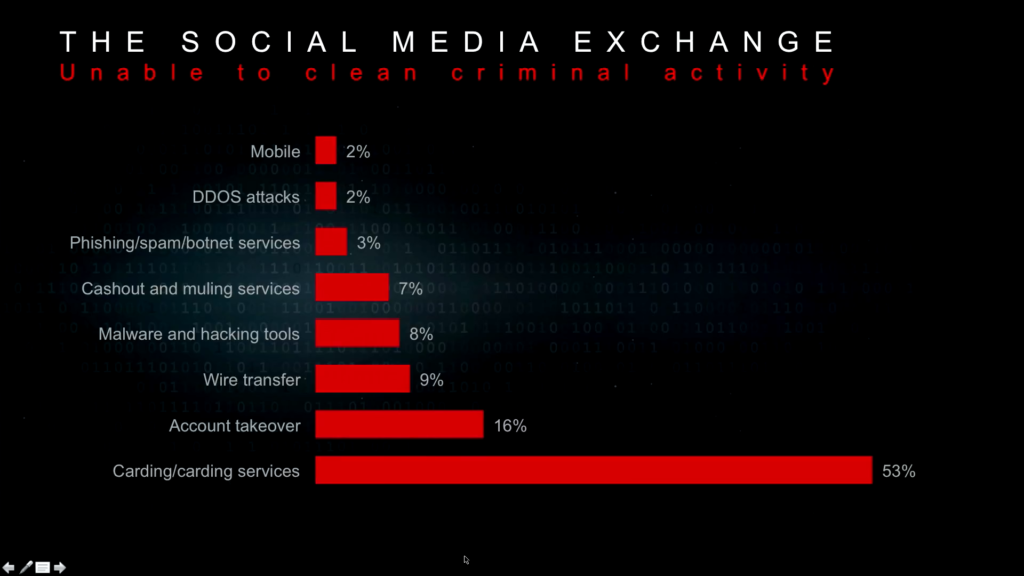
So WhatsApp continues to be the most common and favorite social media platform that’s being used. And when you go on to these social media platforms, the amount of activity that’s going on is fairly endless. The carding services I showed you [are] the easiest thing to access when you’re there. But everything from malware, hacking tools, muling services, phishing, botnet services, all of that is accessible with just a few clicks.
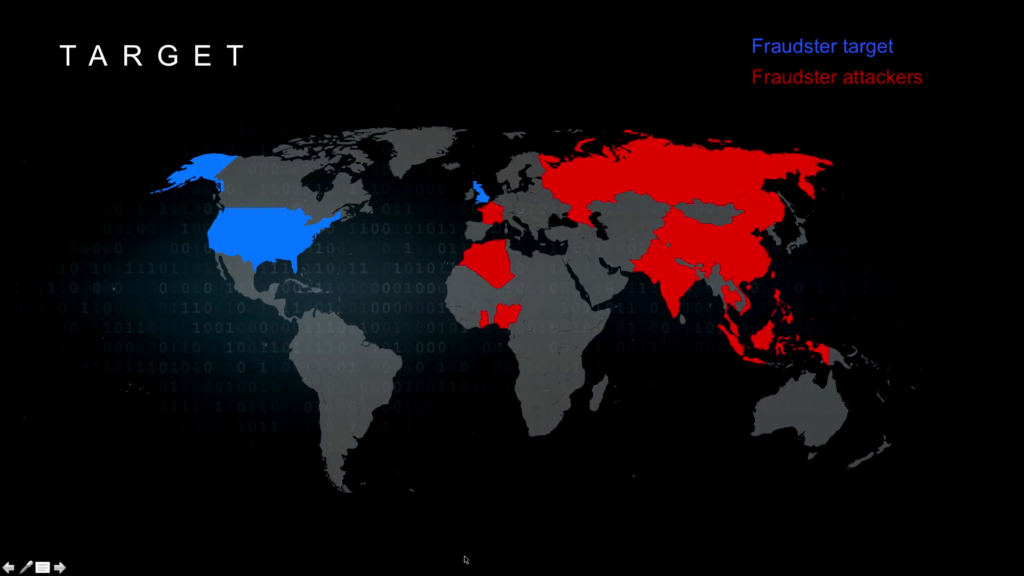
Now, as we look at how this activity takes place— And this is just a map of countries that are launching the targets and the countries that are the target—the red being the attackers and the blue being who’s being attacked—you can see that the US and UK are the target, and the attacks are coming from all over the world.
Now, you will notice, for anyone who knows much about cybercrime, that Brazil’s not on this map. The reason Brazil’s not on the map is because Brazilians tend to be very localized in what they do. So their fraud activities are pretty geographically limited. They don’t tend to go out of their geography. But we are absolutely the targets for most of these activities.
And the the skill set for sure varies by geography that you look at. So for example, the Russians tend to be incredibly sophisticated, very business-oriented. Probably they’ve come up a few times today, and I assume they’ll be continuing to come up a few times. The Chinese are also very sophisticated. They they focus a lot more on hardware and mobile. And then as you make your way to West Africa it tends to be very much about financial transactions and things that can generate money very very quickly.
So to highlight the complete absurdity of what’s going on online I thought I would show this this website, this carding service web site. I don’t know if you can tell, but it’s a very kind of professionally set up web site. It has a cart, it has a place for billing questions. Tickets, if you have questions about what they do. And this particular group was subjected to a DDoS attack. And they were really upset that they were subjected to a DDoS attack. Now keep in mind, right, they’re selling stolen information. They’re selling stolen credit cards. Here was their reaction. This is from June 2015, and for anyone who cares this is a website set up in West Africa.
“Dear friends. We noticed that our site was under several attacks when a group of ‘hackers’…” (Because they’re not.) “…tried to blackmail us, intimidating us with DDoS attacks and abuse.” Right? How dare they. Let’s keep going. “…with our friends and customers…” Right? “With our friends and customers we overcame all the difficulties and saved our business.” How many criminals talk about it this way? “We always play fair, brothers, and we want you to play fair.”
So, what is beautiful about this, from my perspective, is just trying to understand the mindset of the people who are doing these activities. And their view of right and wrong is very very different from our view of right and wrong. And some believe it’s a legitimate business. Doesn’t really have victims. And it’s simply a way to make money in very difficult environments. And it kind of underscores the need for us to keep working and pushing, which is why all of the policy conversations are important. This is the global Internet, and we do not have norms of behavior that we’ve all agreed to. And clearly they vary so much by geography.
So I will end on that note. And hopefully it’s not completely hopeless as you guys head into lunch. But I’m happy to entertain a couple of questions as well, if anyone has them.
Audience 1: [question inaudible]
Niloofar Howe: No, there’s no need to be depressed. There’s just a reality out there. I mean the good news, right, is credit cards are pretty well-protected. But if you’re connected to the Internet, this is the world and the people that you’re connected to, and it’s just really important to understand that reality.
Audience 2: So just following up on that final point about norms of responsible behavior. In your research or as you looked at these different criminal actors, did you find that there were any attempts to establish kind of of standards for responsible behavior among that crowd? And if not, is that something that you see coming?
Howe: So, the answer to that totally varies by region. I wouldn’t say that there’s necessarily standards of behavior. But there are folks who are invited in and folks who are not invited in. So if you take for example the Arab-speaking countries, if you can’t interact with them using not just the language but also the way they greet each other and speak to each other and all the pleasantries that goes around it, you will absolutely not become part of the community. So there’s very well-defined norms in terms of communicating who’s allowed in, who’s not allowed in, where you conduct your activities. But there aren’t really standards of behavior emerging, as far as we can see.
[To upcoming audience member:] Okay, I know you guys do this for a living, so go easy on me.
Audience 3: Don’t worry. So, we track a lot of—in addition to Russian and Chinese cybercriminals—we look at a lot American cybercriminals. And one thing that I was wondering is, within your team’s research do you see similar sophistication in US-based cybercriminals? I know the tend to be kind of localized in their targeting. Do they run businesses in the same way? I’m just kind of curious what you guys are seeing.
Howe: So, most of our research has focused on the international communities, for a lot of reasons including— And my talk here— Because in the US we actually enforce our laws. So it is much more difficult to conduct business the way folks around the world are conducting business, where the laws may not be well-defined, prosecution simply doesn’t happen in certain parts of the world. But it is a very different environment in the US.
Alright. Thank you.
Further Reference
Cybersecurity for a New America event page
